Infrastructure Diagram | Image: Team Cymru
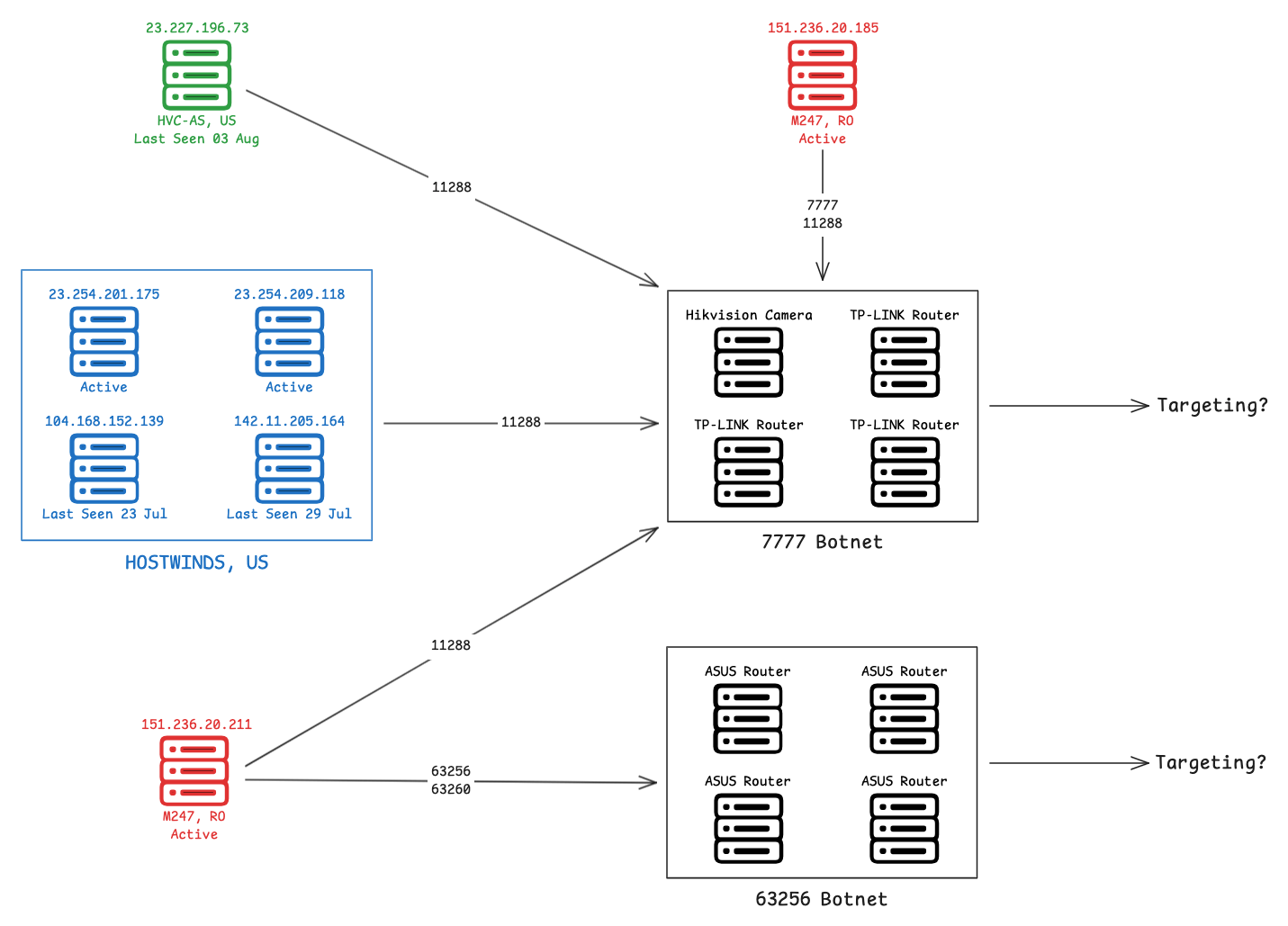
Security researchers from Team Cymru have identified a significant expansion in the activities of the “7777” botnet, first detected in October 2023 and named for its use of TCP port 7777 on compromised routers. Recent investigations reveal that this botnet has dramatically increased its scale of operations, despite ongoing containment efforts, raising concerns among experts.
Initially, the “7777” botnet was observed engaging in malicious activities targeting Microsoft Azure cloud services, characterized by low-volume attacks that made detection difficult. At that time, the botnet comprised approximately 10,000 nodes; however, by August 2024, the number of active devices had decreased to 7,000.
Recent data indicates that the botnet has expanded through the use of new infrastructure, exploiting open port 63256 on infected Asus routers. This expansion has allowed the botnet to encompass nearly 13,000 active devices, which experts believe represents only a portion of the broader malicious network.
Researchers also uncovered seven IP addresses associated with the botnet’s command and control operations. Four of these had been mentioned in previous studies, while three new IP addresses require further analysis. These IP addresses are used to manage compromised devices and may be linked to cyberattacks on Microsoft 365 services.
A significant portion of the infected devices consists of TP-Link routers and Hikvision cameras, consistent with earlier research findings. The new segment of the botnet, operating on port 63256, primarily targets Asus routers, highlighting the evolution of the attackers’ methods.
Despite efforts to combat the botnet, it continues to operate, maintaining a substantial number of compromised devices. Specialists are continuing to study its infrastructure to better understand the botnet operators’ objectives and potential attack vectors.
Experts strongly advise users to update their device firmware, use robust passwords, and regularly monitor network activity to prevent potential compromises.
Related Posts:
- Hackers use Cisco Router flaws to attack Iran, 3,500 routers hacked
- Code for exploiting Zero Day Huawei Router Vulnerability is public
- Nearly 240,000 fiber router exist authentication bypass flaw that can be remotely attacked
- US/UK warn Russia to hack into global routers