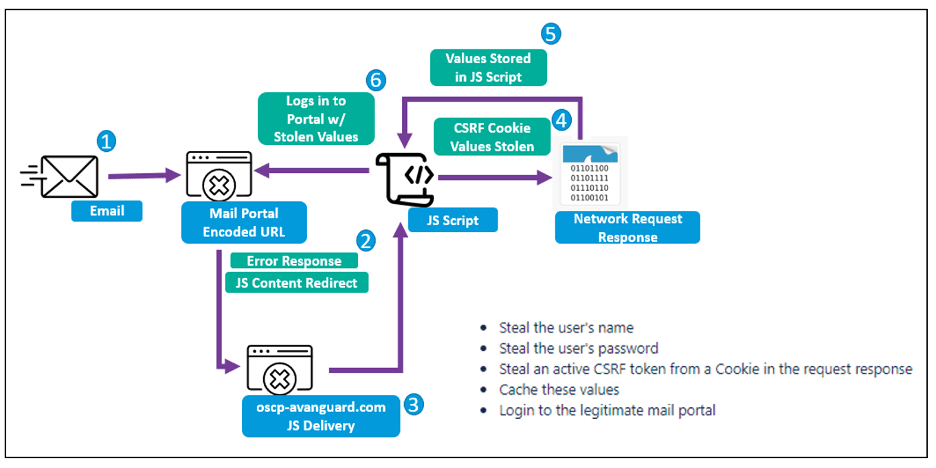
TA473 cross-site request forgery infection diagram. | Image: Proofpoint
In the realm of cyber threats, a concerning trend has been recognized by Proofpoint researchers: advanced persistent threat (APT) actors are increasingly targeting small and medium businesses (SMBs). These highly skilled, state-backed cyber threat actors, linked to Russian, Iranian, and North Korean interests, operate under strategic missions encompassing espionage, intellectual property theft, destructive attacks, state-sponsored financial theft, and disinformation campaigns.
Amidst the torrent of daily cyber threats, the significance of APTs tends to be overlooked. These elite adversaries, while less common, prove to be more focused, and thus, more dangerous. Data analysis from Q1 2022 to Q1 2023 unveils that these state-backed actors are notably interested in targeting SMBs – entities often lacking the robust cyber defenses of larger corporations.
Emerging trends in APT campaigns have been identified, revealing the techniques and strategies employed against SMBs. Firstly, compromised SMB infrastructure has been co-opted for use in phishing campaigns. Instances have been observed where an SMB’s web server or email account is infiltrated, possibly through unpatched vulnerabilities or credential harvesting. Once compromised, these assets are used as springboards for further attacks.

For instance, the APT actor TA473, also known as Winter Vivern, executed phishing campaigns targeting US and European government entities using compromised SMB infrastructure. These breaches involved unpatched WordPress domains and Zimbra webmail servers, with the actor leveraging these vulnerabilities to deliver malicious malware to third-party targets.
Additionally, financially motivated attacks against SMB financial services have been perpetrated by APT actors. These state-aligned cybercriminals have set their sights on the financial sector, targeting institutions, decentralized finance, and blockchain technology with the intent of pilfering funds and cryptocurrency. An instance of this was observed when the North Korea-aligned TA444 targeted a medium-sized digital banking institution in the US with a phishing campaign.
Finally, the rise in APT supply chain attacks targeting regional managed service providers (MSPs) has become apparent. These MSPs, often with inadequate cyber defenses, oversee the protection of numerous local SMBs, rendering them prime targets for APT actors. An example of this trend was observed when TA450, attributed to Iran’s Ministry of Intelligence and Security, targeted Israeli regional MSPs via a phishing email campaign.
In conclusion, the threat landscape is evolving, and SMBs, often viewed as softer targets, are increasingly under the radar of state-backed APT actors. These sophisticated adversaries exploit SMB vulnerabilities for their strategic missions, posing significant risks to SMBs globally. To safeguard against these escalating threats, businesses and MSPs must adopt agile and robust cyber defenses like Proofpoint Essentials, capable of detecting targeted attacks and high-volume threats from cybercrime actors.