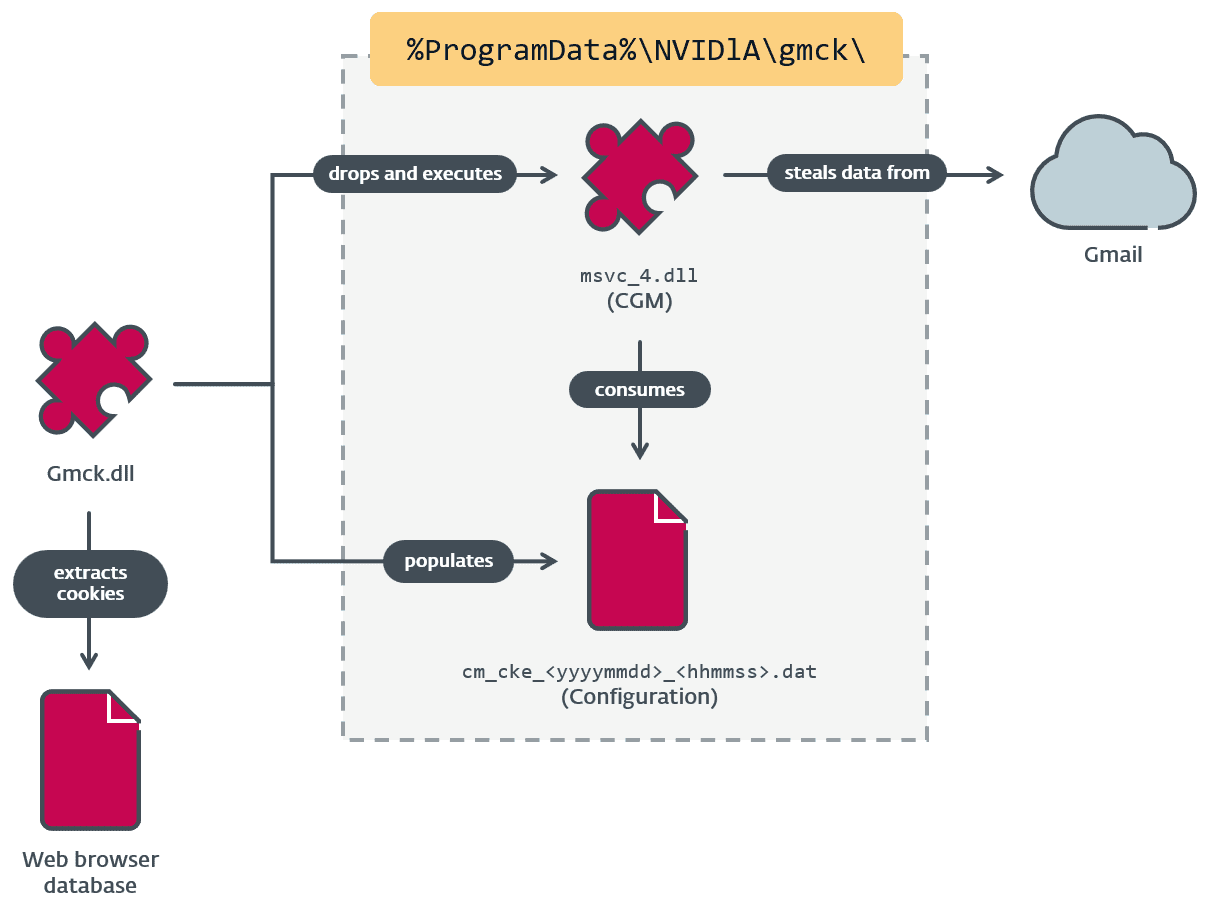
Interactions between Gmck and CGM | Image: ESET
In a recent discovery, ESET researchers unveiled “CloudScout,” a sophisticated cyberespionage toolset employed by the advanced persistent threat (APT) group called Evasive Panda. This China-aligned group has reportedly used CloudScout to infiltrate the networks of government and religious organizations in Taiwan. The toolset primarily exploits stolen browser session cookies to access and exfiltrate data from popular cloud services, including Google Drive, Gmail, and Outlook.
ESET’s report states, “CloudScout utilizes stolen cookies, provided by MgBot plugins, to access and exfiltrate data stored at various cloud services”. MgBot, a well-known malware framework associated with Evasive Panda, supplies these session cookies through specific plugins designed to integrate seamlessly with the CloudScout modules. The researchers detected three key CloudScout modules—CGD, CGM, and COL—each of which targets a different cloud service.
The modular nature of CloudScout makes it adaptable. Each module is programmed in C# and focuses on specific targets, with some modules potentially in development to extend its reach further. The report notes, “We analyzed three CloudScout modules…We believe that at least seven additional modules exist,” implying that this toolset may have broader capabilities.
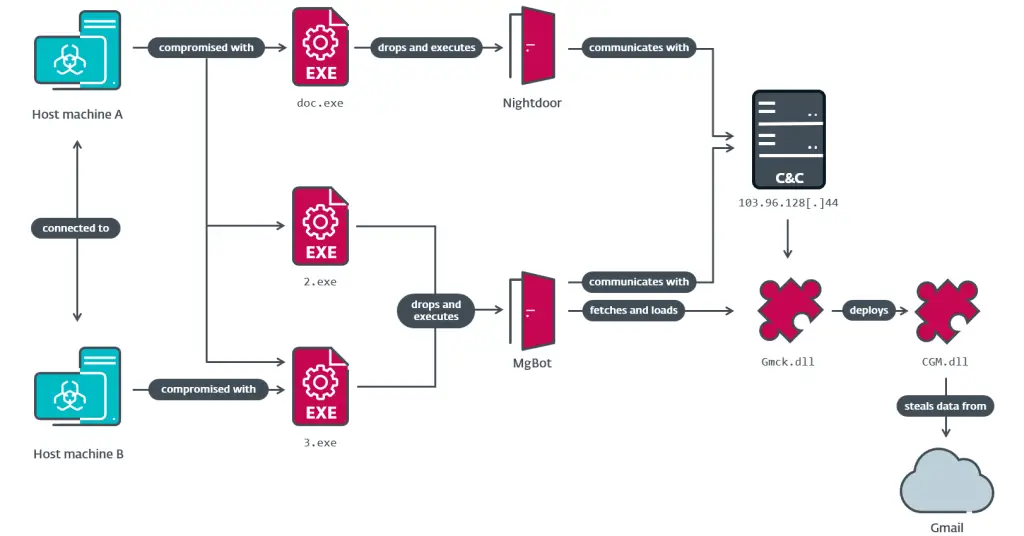
CloudScout’s stealth lies in its use of cookie-based authentication, bypassing security measures like two-factor authentication (2FA). Instead, by hijacking authenticated web sessions, CloudScout modules perform actions as if they were legitimate users. This technique is particularly effective for gaining unauthorized access to cloud-stored data, which is then exfiltrated. As ESET describes, “The stolen cookies allow the attacker to retrieve data stored in the cloud, right from the victim’s machine.”
As ESET continues to monitor and study Evasive Panda’s latest capabilities, it underscores the importance of emerging defenses like Google’s Device Bound Session Credentials and Chrome’s App-Bound Encryption, which aim to combat cookie-based intrusions.
Related Posts:
- PANDA Banker Malware Attacks Bank Institutions, Cryptocurrency Trading Platforms, and Social Media
- China-Linked Mustang Panda Targets Vietnamese Entities in Cyber Espionage Campaign
- Stealthy New Golang Trojan Exploits Fake Certificates for Evasive Communication
- Google Keeps Third-Party Cookies, Enhances User Control in Chrome
- W3C Slams Google’s Cookie Reversal: Privacy at Risk?