
Forcepoint’s X-Labs research team has uncovered a sophisticated and stealthy phishing campaign orchestrated by the notorious Darkgate malware. This report reveals the intricate details of the campaign, its propagation methods, and the technical nuances that make it particularly challenging to detect and neutralize.
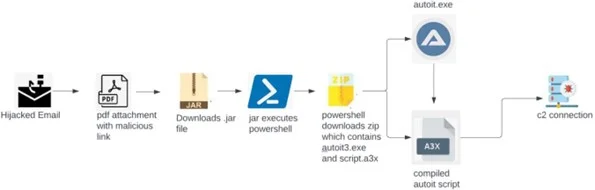
The Darkgate campaign primarily leverages phishing emails to distribute its malicious payloads. By hijacking email accounts, the attackers send out emails with seemingly legitimate attachments, such as XLSX, HTML, and PDF files. These emails are designed to trick recipients into downloading and executing the malware, which then spreads across the victim’s network, leading to potentially severe consequences such as personal data theft, financial loss, and compromise of sensitive information.
The campaign kicks off with an email featuring an invoice purportedly from “Intuit QuickBooks” in a PDF format. This PDF prompts users to install Java to view the invoice, providing a seemingly legitimate link. When users click on this link, they are redirected to a geofenced URL that initiates the download of a malicious JAR (Java Archive) file.
Analysis of the JAR file unveils a multi-stage attack. It downloads a ZIP file containing an AutoIt script, a tool known for its use in previous Darkgate campaigns. The script, heavily obfuscated to evade detection, ultimately executes shellcode and establishes connections with remote command-and-control servers.
Researchers noted that the URLs used in this campaign bear striking similarities to those previously associated with QakBot, another notorious malware strain. This suggests a potential connection between the two threats or the reuse of infrastructure by different threat actors.
The Darkgate campaign poses a significant threat, especially to businesses and individuals relying on email communications for financial and sensitive information exchanges. The use of geofenced URLs and obfuscated scripts highlights the attackers’ efforts to evade detection and persist in targeted systems.