
A new report from Mandiant, a leading cybersecurity firm, paints a comprehensive picture of UNC4393, a prolific ransomware gang that has attacked organizations across the globe. The report offers insight into the group’s evolution, tactics, and the factors contributing to its recent decline.
Mandiant has responded to over 40 separate UNC4393 intrusions across 20 different industry verticals. While traditionally not targeting healthcare, recent breaches in this sector suggest an expansion of their targets. However, this is just a fraction of their activity, with over 500 victims claimed on the Black Basta data leak site.
UNC4393 has shown a significant evolution in its operational tactics and malware usage since its emergence. Initially leveraging the QAKBOT botnet for initial access, their techniques have evolved, especially after the QAKBOT botnet takedown. They have shifted from using widely available tools to developing custom malware and relying on access brokers.
UNC4393, a financially motivated threat cluster, primarily uses BASTA ransomware. Initially tracked since mid-2022, Mandiant believes their activity began earlier in the year based on BASTA DLS activity. The group mainly gains initial access through QAKBOT infections delivered via phishing emails, often using HTML smuggling techniques.
Mandiant suspects that BASTA operates on a private, invitation-only affiliate model, unlike traditional ransomware-as-a-service (RaaS) operations. This exclusivity likely contributes to their efficient and rapid operations, with a median time to ransom of about 42 hours.
UNC4393’s malware arsenal includes several sophisticated tools:
- BASTA: A C++ ransomware encrypting local files with .basta or random extensions.
- SYSTEMBC: A tunneler retrieving commands from C2 servers, often used to hide network traffic.
- KNOTWRAP: A memory-only dropper executing additional payloads in memory.
- KNOTROCK: A .NET utility creating symbolic links and executing ransomware.
- DAWNCRY: A memory-only dropper with encrypted shellcode for further exploitation.
- PORTYARD: A tunneler establishing connections to C2 servers.
- COGSCAN: A .NET reconnaissance tool gathering network and system information.
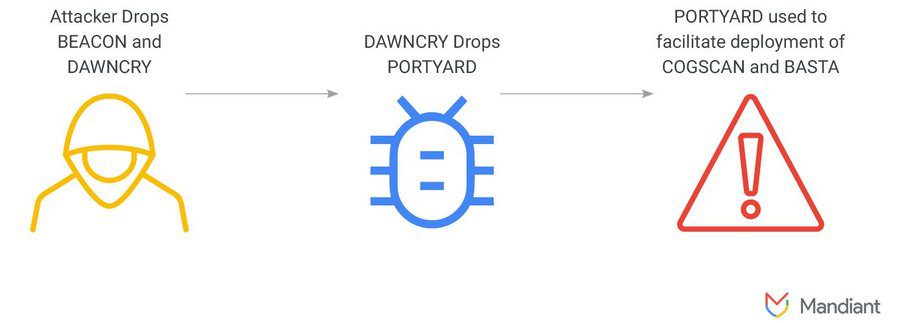
UNC4393 initially relied on QAKBOT infections for access but shifted tactics following the botnet’s takedown. They began using other distribution clusters, such as DARKGATE and later SILENTNIGHT backdoor, showing a willingness to adapt and partner with various actors for initial access.
SILENTNIGHT, a sophisticated C/C++ backdoor, communicates stealthily using HTTP/HTTPS and can dynamically generate command-and-control domains to evade detection. This versatile malware boasts a plug-in architecture, enabling diverse malicious activities ranging from seizing system control and capturing screenshots to logging keystrokes, manipulating files, and even accessing cryptocurrency wallets. It also employs browser manipulation techniques to pilfer sensitive credentials.
After gaining access, UNC4393 employs living-off-the-land techniques and custom malware for persistence and lateral movement. Their reconnaissance tools, like BLOODHOUND and COGSCAN, help map victim networks and identify targets for further exploitation.
UNC4393 aims to quickly exfiltrate data and execute ransomware, leveraging tools like RCLONE for data theft. Their methods have evolved from manual ransomware deployment to using custom utilities like KNOTROCK, which streamline operations and reduce deployment time. Interestingly, if their ransomware deployment fails, UNC4393 may abandon the attempt but could retarget the same environment later.
For further information, the full report can be accessed on Google Cloud’s website.
Related Posts:
- QakBot Returns with Evasive Tactics, Posing Renewed Threat
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware
- DarkGate and PikaBot: New Malware Threats Emerge from Advanced Phishing Campaign
- OneNote Exploited: Malicious Campaigns Unveiled in Note-Taking App
- CVE-2024-26169: Windows Zero-Day Vulnerability Abused by Black Basta Ransomware