
Recently, Palo Alto Networks has released an in-depth analysis of FrostyGoop, also known as BUSTLEBERM, a sophisticated malware targeting operational technology (OT). This malware gained attention in July 2024 when it disrupted the heating systems of over 600 apartment buildings in Ukraine during sub-zero temperatures, leading to a two-day outage.
FrostyGoop represents the ninth known ICS (Industrial Control System)-centric malware but stands out as the first to exploit the Modbus TCP protocol. This protocol is commonly used in industrial environments, making its exploitation particularly alarming. According to Palo Alto Networks: “FrostyGoop sends Modbus commands to read or modify data on industrial control systems (ICS) devices, causing damage to the environment where attackers installed it.”
The malware leveraged vulnerabilities in internet-exposed devices, such as MikroTik routers, to gain access to ICS networks. Once inside, FrostyGoop sent malicious Modbus commands to ENCO control devices, disrupting their operation and causing system malfunctions that required extensive remediation efforts.
FrostyGoop is written in Go (Golang) and employs an open-source Modbus library to execute commands. Key features include:
- JSON Configuration Files: These files define specific Modbus operations, including reading and writing data to ICS devices. The details can also be passed as command-line arguments, enhancing the malware’s flexibility.
- Debugger Evasion: FrostyGoop detects debugging attempts by checking the BeingDebugged value in Windows’ Process Environment Block (PEB), avoiding common tools used by malware analysts.
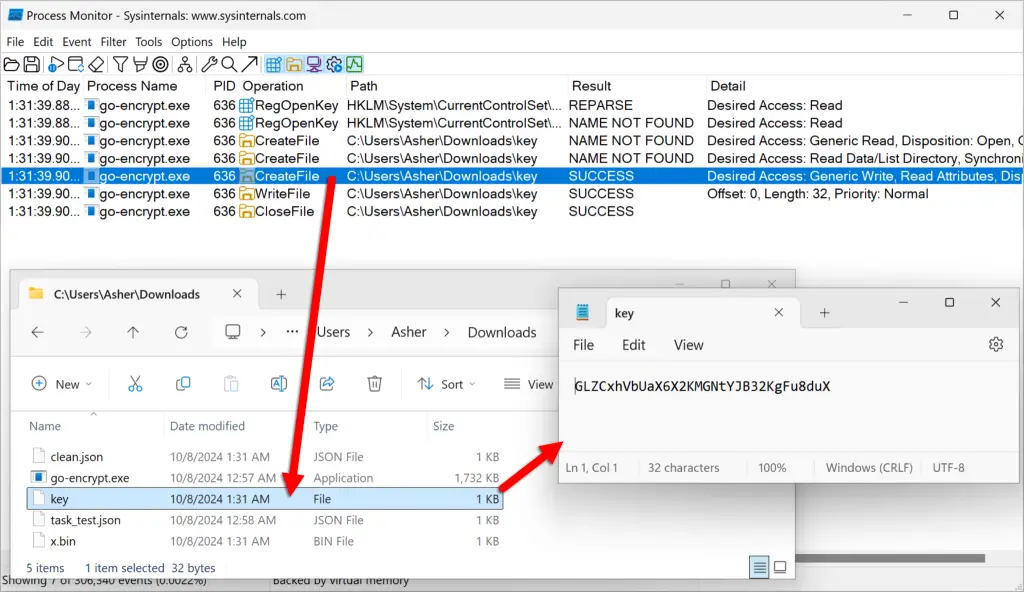
- Encryption Support: The malware may use companion tools like go-encrypt.exe to encrypt its JSON configuration files, concealing its operational details and complicating detection.
The analysis revealed, “Our telemetry indicates that 1,088,175 Modbus TCP devices were exposed to the internet from Sept. 2-Oct. 2, 2024, and 6,211,623 devices were exposed overall.” These devices, particularly ENCO control devices, often lack modern security measures, leaving them highly susceptible to such attacks.
The FrostyGoop attack underscores a growing trend in cyber warfare targeting OT environments. Palo Alto Networks emphasized: “An increasing number of OT networks have been connected with IT networks to facilitate facilities management. This has unleashed new ways to perform cyberattacks that can not only damage the cyberspace realm, but also the physical world.”
As OT networks increasingly converge with IT systems, the need for comprehensive cybersecurity measures grows. By addressing vulnerabilities and adopting proactive defenses, organizations can mitigate the risks posed by advanced threats like FrostyGoop.
Related Posts:
- China-Backed Hackers Escalate Cyber Campaigns, Targeting Operational Technology
- Attackers Exploit Critical OpenMetadata Flaws for Cryptomining on Kubernetes
- Report: the development of cyber security in the oil and gas industry in the Middle East is lagging behind
- CVE-2024-41798 (CVSS 9.8): Siemens SENTRON PAC3200 Meters Vulnerable to Easy Attacks, No Patch!