fuzzable v2.0.6 releases: Automating Fuzzable Target Discovery with Static Analysis
Fuzzable
Framework for Automating Fuzzable Target Discovery with Static Analysis
Vulnerability researchers conducting security assessments on software will often harness the capabilities of coverage-guided fuzzing through powerful tools like AFL++ and libFuzzer. This is important as it automates the bug hunting process and reveals exploitable conditions in targets quickly. However, when encountering large and complex codebases or closed-source binaries, researchers have to painstakingly dedicate time to manually audit and reverse engineer them to identify functions where fuzzing-based exploration can be useful.

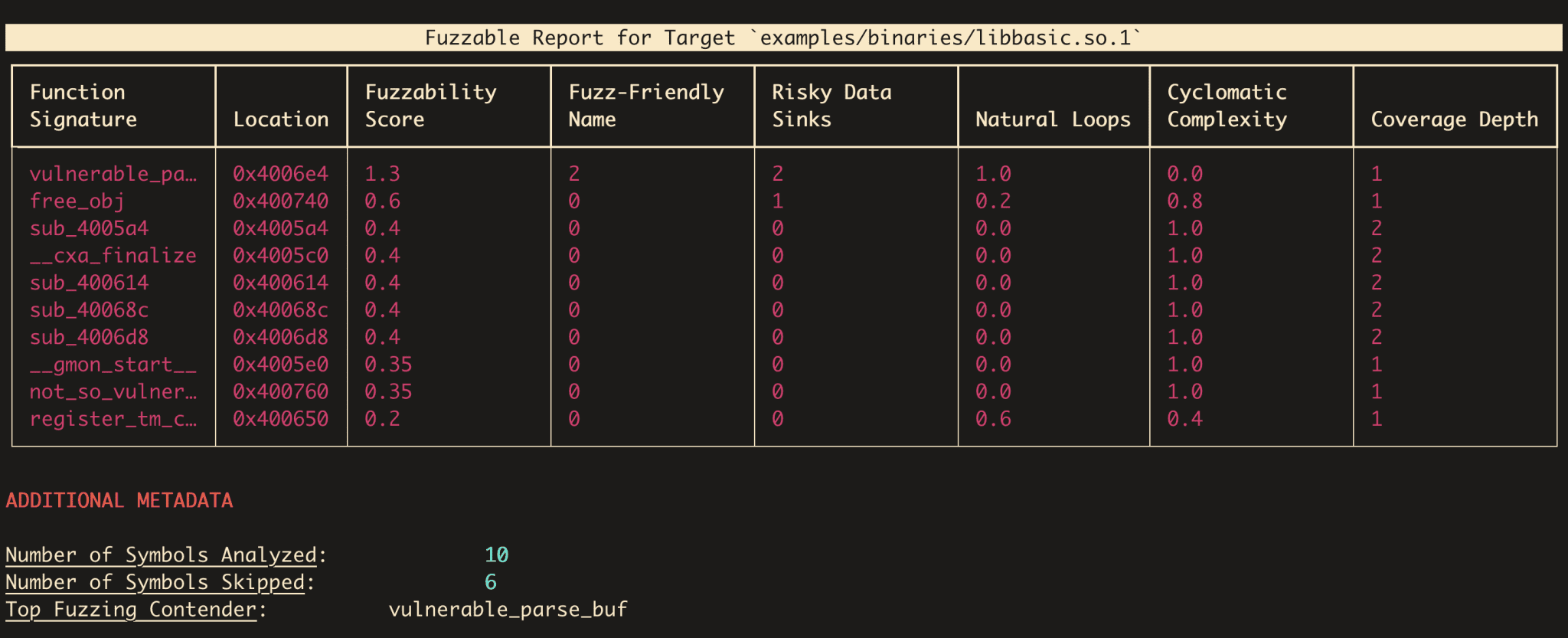
Fuzzable is a framework that integrates both C/C++ source code and binaries to assist vulnerability researchers in identifying function targets that are viable for fuzzing. This is done by applying several static analysis-based heuristics to pinpoint risky behaviors in the software and the functions that execute them. Researchers can then utilize the framework to generate basic harness templates, which can then be used to hunt for vulnerabilities or to be integrated as part of a continuous fuzzing pipeline, such as Google’s oss-fuzz project.
In addition to running as a standalone tool, Fuzzable is also integrated as a plugin for the Binary Ninja disassembler, with support for other disassembly backends being developed.
Check out the original blog post detailing the tool here, which highlights the technical specifications of the static analysis heuristics and how this tool came about. This tool is also featured at Black Hat Arsenal USA 2022.
Features
- Supports analyzing binaries (with Angr and Binary Ninja) and source code artifacts (with tree-sitter).
- Run static analysis both as a standalone CLI tool or a Binary Ninja plugin.
- Harness generation to ramp up on creating fuzzing campaigns quickly.
Changelog v2.0.6
- Fix TypeError in LIEF integration by @bstee615 in #55
- Bump docker/build-push-action from 3.3.0 to 4.0.0 by @dependabot in #56
Install & Use
Copyright 2022 ex0dus-0x