fwaudit v0.0.4 releases: Platform Firmware Auditing Tool
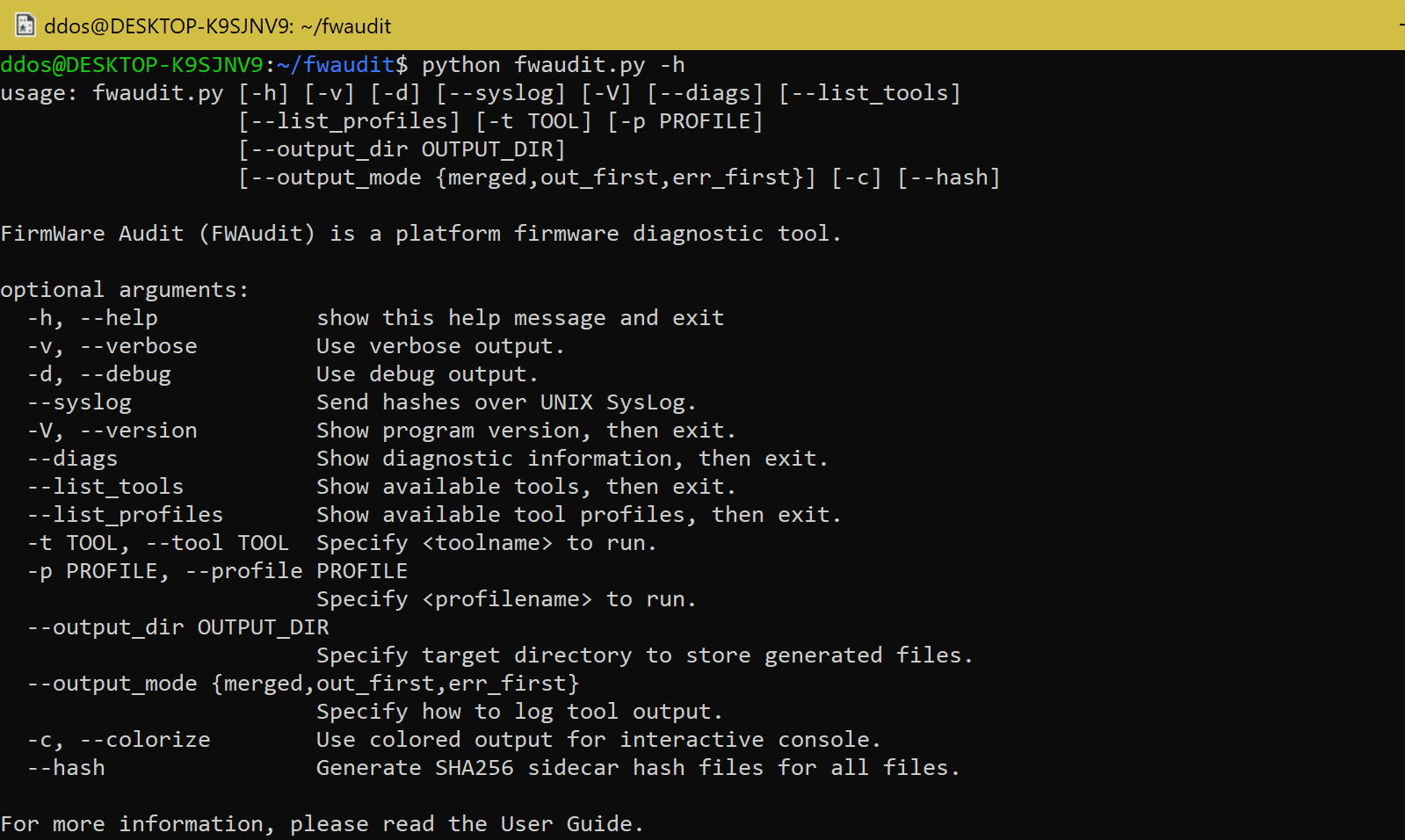
Firmware Audit (fwaudit) is a platform firmware test utility. It runs tests and gathers diagnostic and security information about a system’s firmware. The target audience is System Administrators, Site Reliability Engineers, DFIR, and enterprise Blue Teams. FWAudit is a front-end to multiple tools, both ‘live’ and ‘offline’ firmware analysis and diagnostic tools. Initially, the main tools are the CHIPSEC project and the FirmWare Test Suite (FWTS). More tools are planned for future versions. FWAudit is GPLv2-licensed Open Source — technically Free Software — Python tool.
It currently works on Intel x64 UEFI systems running Debian Linux. More architectures and operating systems are planned for future versions.
FWAudit generates a lot of output: multiple directories and files for each tool invoked. Each time FWaudit is run, a new directory is created to store the results. The tool has 3 uses of directories:
- The Parent Directory (PD) is the top-level directory where all FWAudit output is generated. The default PD is, ~/fwaudut.data’, the user can change it via the –output_dir option. If this directory does not yet exist, it is created before the first tool is run.
- A new Per-Run Directory (PRD) directory is created each time FWAudit is run, each run’s output is stored in a separate directory, the directory is named with a YYYYMMDDHHMMSS timestamp format. (Please don’t run the tool more than once per second, else we’ll have to add milliseconds to the PRD name…)
- Each tool run has its own Per-Tool Directory (PTD). FWAudit runs the same tool in multiple ways, using different command line options, by naming each different tool usage with a different ‘namespace’ name, eg. ‘chipsec_spi_rom_dump’ for the ‘chipsec_util spi rom dump’ command. This ‘namespace’ string is used for the PTD.
Running FWaudit generates a <PD>/<PRD>/<PTD> directory hierarchy. Each file has stdout saved, either separately as <tool>.stdout.txt and <tool>.stderr.txt, or merged as <tool>.output.txt. If hashing option is specified, additional sidecar hash files are created for these output files, eg <tool>.output.txt.sha256. Additionally, each tool may generate additional files, for example, ‘chipsec_util spi rom dump’ command generates a rom.bin file. These files are located in the <PTD> along with the output files.
Changelog
v0.0.4
- Version 0.0.4-PRE-ALPHA
- added INTEL SA-00085 Discovery Tool for CVE-2017-5705,CVE-2017-5708,CVE-2017-5711,CVE-2017-5712,CVE-2017-5706,CVE-2017-5707,CVE-2017-5709,CVE-2017-5710,CVE-2017-5706,CVE-2017-5709 ME / TEE / SPS Vulnerability
- added verifiable sha256sum format file for all output, including stdio. –hash option
- added –manifest option to generate manifest file
- fixed sudo bug on MacOS
Install
Prerequisites:
The current release of fwaudit has the following system restrictions:
* architecture: Intel x64
* firmware: BIOS, UEFI, ACPI
* operating systems: Debian GNU/Linux
* tools: CHIPSEC, FWTS, ACPICA tools (acpidump, acpixtract), lspci, lsusb
* Python: requires the CPython 2.7x. Reason: the UEFI Shell version of Python is CPython 2.7x, which CHIPSEC for UEFI relies on (and bundles).
UPDATE: Intel has recently ported MicroPython to UEFI, so this requirement may soon change.
Download
git clone https://github.com/PreOS-Security/fwaudit.git
Use

Tutorial
Copyright (C) 2018 Lee-Fisher





