Infection chain overview
In a detailed analysis, TRAC Labs has exposed a phishing campaign named Gabagool that targets corporate and government employees. The campaign leverages the trusted reputation of Cloudflare’s R2 storage service to bypass security measures.
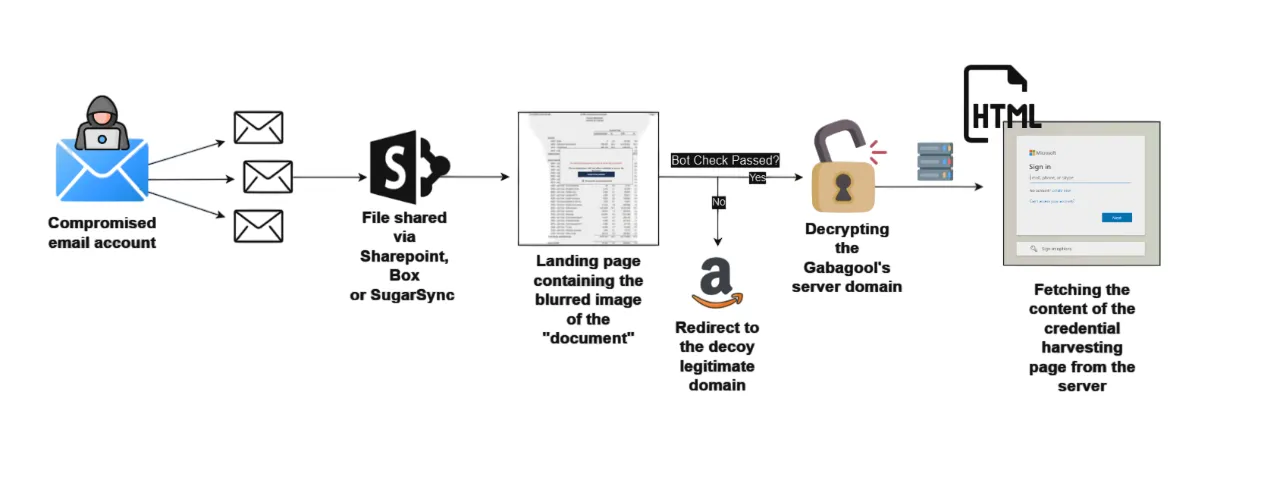
Gabagool begins its infection chain by compromising an employee’s email account. The compromised account then sends phishing emails to other employees, embedding malicious links within images or documents. For example, an image might be labeled “NEW FAX DOCUMENT(S) HAS BEEN RECEIVED,” with an embedded URL directing victims to seemingly legitimate file-sharing platforms like SharePoint or Box.
“These emails prompt recipients to view an image attached to the email, which is disguised as a document. Embedded within the image is a malicious URL-shortened link leveraging tiny.cc and tiny.pl that contain a redirect chain.”

However, these redirects lead to phishing pages hosted in Cloudflare R2 buckets. “Threat actors can abuse Cloudflare R2 buckets for phishing by hosting malicious content or phishing landing pages in these buckets, leveraging the trusted reputation of Cloudflare to bypass security filters,” the report notes.
The Gabagool phishing kit employs obfuscated JavaScript and sophisticated bot detection mechanisms to evade security measures. Key features include:
- Bot Detection: The phishing pages use checks like detecting headless browsers (e.g., Selenium), monitoring mouse movements, and testing for disabled cookies. If bot activity is suspected, users are redirected to legitimate websites.
- Credential Harvesting: Once users pass the bot checks, the phishing page loads a credential harvesting form. Harvested credentials are encrypted using AES before being sent to the attacker-controlled server.
The Gabagool campaign has already affected numerous organizations, particularly targeting industries like finance and government. Its use of advanced evasion techniques and trusted platforms has made it a dangerous threat.
Related Posts:
- HTTP/2 Rapid Reset Attack: HTTP/2 Zero-Day Vulnerability Rocks Cybersecurity World
- Researchers Uncovers Sophisticated Phishing Campaigns Leveraging Cloudflare Workers