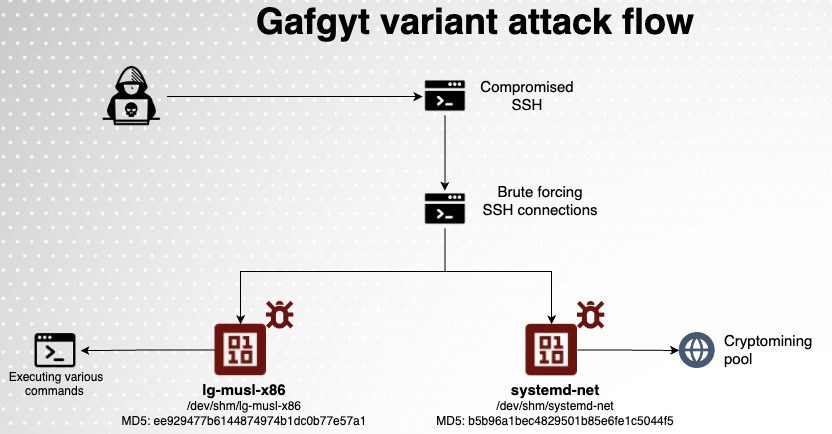
Gafgyt attack flow | Image: Aqua Nautilus
Researchers at Aqua Nautilus have identified a new variant of the Gafgyt botnet that represents a significant evolution in malware targeting strategies. Originally known for infecting IoT devices to conduct DDoS attacks, the latest variant of Gafgyt now sets its sights on more robust cloud-native environments, exploiting GPU power to mine cryptocurrency.
Gafgyt, also known as Bashlite or Lizkebab, has been a persistent threat since its emergence in 2014, primarily attacking IoT devices with weak or default credentials. However, the recent discovery by Aqua Nautilus marks a notable shift in its operational focus. The new variant not only continues its traditional brute-force attacks on vulnerable SSH services but also leverages advanced computational power from GPUs in cloud-native environments to mine Monero cryptocurrency.
The attack begins with a brute-force assault on SSH servers with weak passwords. Once access is gained, the malware drops two key binaries into memory:
- ld-musl-x86: Identified as a Gafgyt SSH scanner, this Go-compiled ELF binary is designed to search for exposed SSH and Telnet services, generating IP addresses and ports, and conducting brute-force attacks. It cleverly masquerades as a legitimate system component, leveraging the lightweight musl libc implementation often found in cloud-native environments.
- systemd-net: This binary is an XMRIG cryptominer, specifically configured to exploit GPU power using CUDA and OpenCL flags. By focusing on machines with significant GPU capabilities, the malware can mine cryptocurrency more efficiently, representing a shift from Gafgyt’s historical reliance on IoT devices with limited computational resources.
Aqua Nautilus researchers have highlighted the growing threat this variant poses to cloud-native environments. The malware’s ability to exploit powerful cloud servers, typically running services such as Hadoop, AWS, Azure, and Ansible, is a stark contrast to its earlier focus on IoT devices. The inclusion of usernames like “admin,” “app,” and “devops” in the brute-force configuration file underscores its broader targeting strategy, aiming at a wide array of Linux systems in both general-purpose and specialized cloud environments.
The binaries dropped by this Gafgyt variant are designed to evade detection by masquerading as legitimate Linux system components. The use of names like ld-musl-x86 and systemd-net reflects a sophisticated approach to blending in with the environment, making the malware harder to detect and remove.
Furthermore, the malware conducts system checks to ensure that the target machine is not a honeypot, which suggests a more selective infection strategy. This tactic not only maximizes the effectiveness of the attack but also minimizes the risk of early detection by cybersecurity researchers.
For detailed technical analysis related to this Gafgyt botnet variant, visit the Aqua Nautilus research blog.
Related Posts:
- Openfire Bug (CVE-2023-32315) Exploited to Deploy Kinsing Malware and Cryptominer
- Google Formally Integrates Kubernetes Engine and GPU Services
- ThreatMapper: Comprehensive Threat Management for Cloud-Native Environments