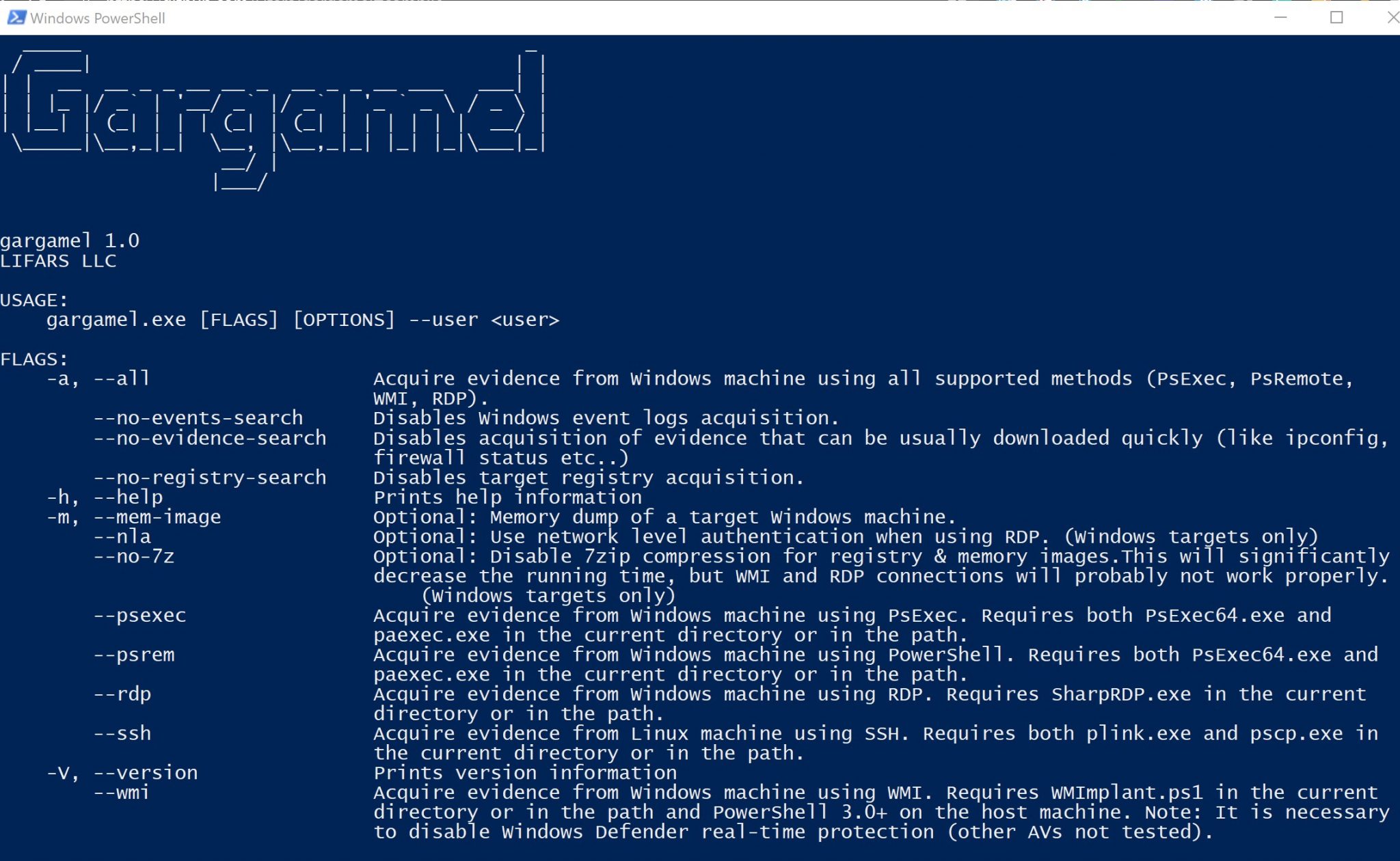
Gargamel
Right now, this app works only on Windows and the target computer must use Windows or Linux.
Make sure to have the following programs in the same directory as Gargamel.
- psexec, download
- paexec, an open-source alternative to PsExec, download
- winpmem, an open-source memory image tool, download.
- Download the newest executable and rename it to winpmem.exe
- plink and pscp, an open-source CLI SSH/SCP clients, download
- SharpRDP, an open-source command executor using RDP, download
- WMImplant, as an open-source PowerShell WMI command executor, download
- 7za.exe, a standalone console version of 7zip archiver, download
Note: We need both the psexec and paexec. Although both applications are supposed to be functionally equivalent they actually both have different behavior under some circumstances.
Unleashing the power of Gargamel
Gargamel needs to be launched from an elevated terminal to be fully functional. Currently, it does not support the UAC dialog nor any kind of notification when running with limited privileges. When running with limited user privileges, then some operations like target memory dumping will not work.
Basic example
Assume you want to connect to a computer with the following parameters:
- address 192.168.42.47
- username
Jano - password
nbusr123
The following command will acquire firewall state, network state, logged users, running processes, active network connections, registry, system & application event logs using the PsExec method. Evidence will be stored in the testResults directory relative to the location of Gargamel.
gargamel.exe -c 192.168.42.47 -u Jano --psexec -o testResults
Gargamel will ask you for the password of the remote user, in our example the password isnbusr123. Note that the password will be hidden when typing.
It is also possible to specify the password directly as a program argument.
gargamel.exe -c 192.168.42.47 -u Jano --psexec -p nbusr123 -o testResults
Domain example
Assume you want to connect to a computer in a domain with the following parameters:
- domain
WORKSPACE - computer name
JanovPC - username
Jano - password
nbusr123
The following command will acquire firewall state, network state, logged users, running processes, active network connections, registry, system & application event logs using the PsExec method.
gargamel.exe -c JanovPC -u Jano -d WORKSPACE --psexec -o testResults
Or to skip password prompting specify the password directly.
gargamel.exe -c JanovPC -u Jano -d WORKSPACE –psexec -p nbusr123 -o testResults
Other connection methods
PsExec is one of the 5 supported connection methods. You can replace the –psexec with the following options:
--psexec--psrem, if PowerShell remoting is configured on the target machine.--rdp, if RDP is enabled on the target machine.--wmi.--ssh, if the target machine uses Linux.
It is possible to use several methods at once. For example to use both PsExec and RDP one can use the following command.
gargamel.exe -c 192.168.42.47 -u Jano --psexec --rdp -o testResults
There is also a special switch –all that is equal to specifying –psexec –rdp –psrem –wmi.
Note: Launch parameters are order-agnostic, i.e. it does not matter in which order the parameters are specified.
Acquire memory
To acquire also memory dump, then simply add the -m flag to the program parameters, i.e.
gargamel.exe -c 192.168.42.47 -u Jano --psexec -o testResults -m
If you wish to acquire ONLY the memory dump without other evidence then use the following command.
gargamel.exe -c 192.168.42.47 -u Jano –psexec -o testResults -m –no-events-search –no-evidence-search –no-registry-search
This functionality is available only for Windows targets.
Run custom commands
Gargamel may run custom Windows CMD or Linux shell commands on the remote machine.
First, create a file custom-commands.txt with the following content.
# Will be run using any method
ipconfig
# Will run only when launching with at least one of --all, --psexec, --wmi methods
:psexec:wmi ipconfig -all
Results of the above commands will be stored in the directory specified by -o option.
To run the above commands written in custom-commands.txt use the -e switch, i.e.
gargamel.exe -c 192.168.42.47 -u Jano --psexec -o testResults -e custom-commands.txt
Download custom files
Gargamel is able to download remote files.
First, create a file custom-files.txt with the following content.
C:\Users\Public\sss*
C:\Users\Jano\danove.pdf
# This line and the next one will be ignored
# C:\Users\Jano\somBajecny.pptx
Note: Wildcards * and ? are supported but currently only in filenames, not parent directories, i.e. C:\Users\J*\danove.pdf will most likely not work.
Results of the above commands will be stored in the directory specified by -o option.
To run the above commands written in custom-files.txt use the -s switch, i.e.
gargamel.exe -c 192.168.42.47 -u Jano --psexec -o testResults -s custom-files.txt
Changelog v1.1
- Better shared directory support & local mode support
Download
Copyright (C) 2020 LIFARS LLC