Gatekeeper Bypass: Malicious Apps Could Slip Through macOS Defenses
A new report from Unit 42 researchers has uncovered significant weaknesses in macOS’s Gatekeeper security mechanism, which could allow malicious applications to bypass Apple’s verification process and execute harmful code on users’ systems. Gatekeeper is designed to ensure that only trusted software runs on macOS devices by validating applications downloaded from outside the App Store. However, the report highlights several third-party utilities and Apple’s own command-line tools that fail to enforce a critical quarantine attribute, thus exposing users to potential threats.
Gatekeeper relies on a metadata attribute, known as com.apple.quarantine, that is applied to files downloaded from the internet. This attribute triggers Gatekeeper to check and verify the file’s safety before allowing it to execute. Unfortunately, researchers found that many third-party utilities do not properly propagate this quarantine attribute, allowing files to slip through Gatekeeper’s protections.
According to the report, “certain third-party utilities and applications pertaining to archiving, virtualization, and Apple’s native command-line tools do not enforce the quarantine attribute”, leaving the system vulnerable to unverified and potentially malicious files.
Unit 42 researchers identified several categories of applications where files were not inheriting the quarantine attribute. These include archiving utilities, virtualization software, and native macOS command-line tools. Notably, popular archiving applications such as iZip, Archiver, BetterZip, and WinRAR were all found to bypass Gatekeeper by not applying the quarantine attribute to extracted files. This means that malicious files within archived formats such as ZIP, TAR, and 7Z could be executed without undergoing Gatekeeper’s security checks.
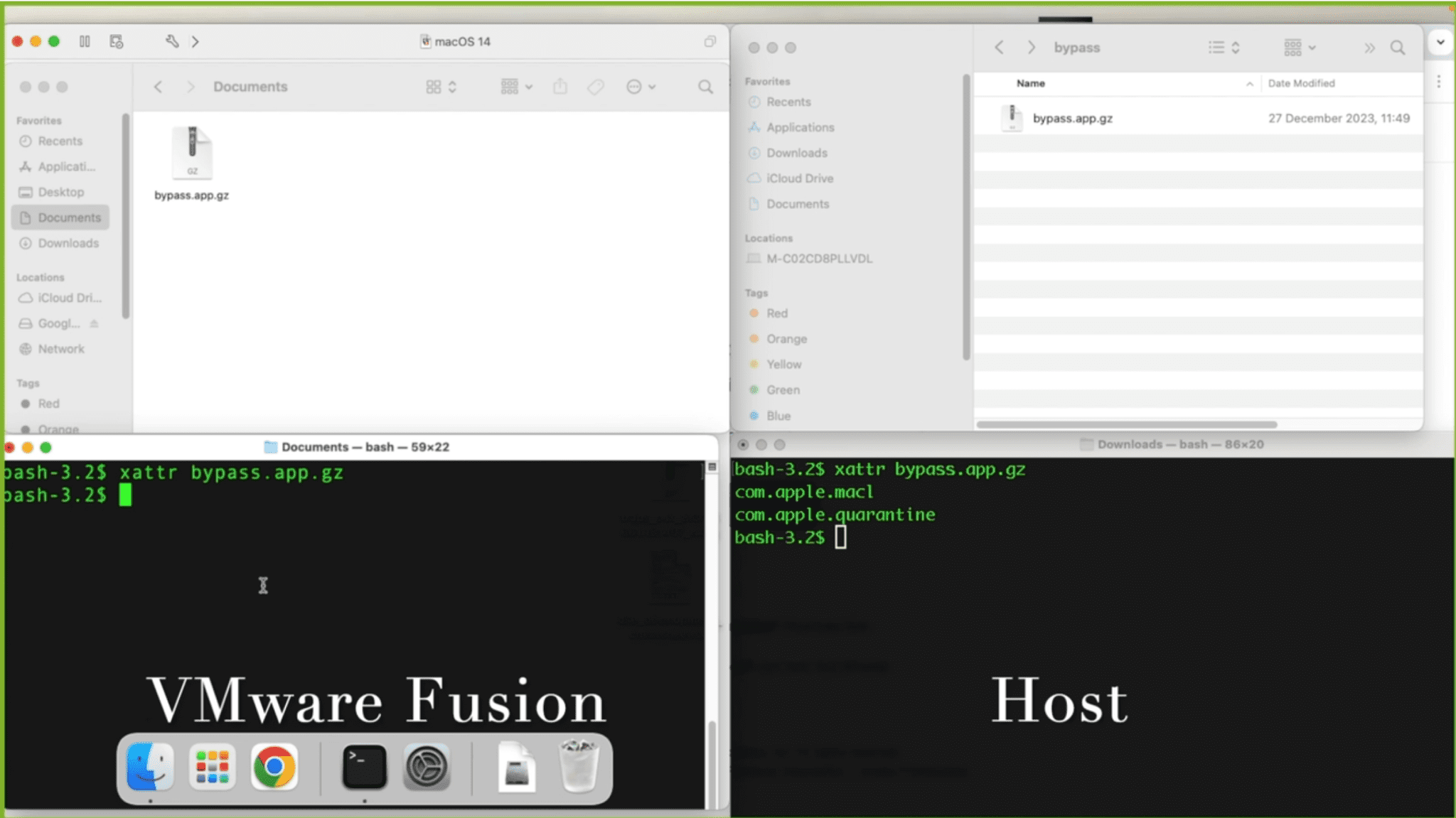
In addition, VMware Fusion, a popular virtualization tool, was found to drop the quarantine attribute when copying files from the host to a guest virtual machine. The report states, “the quarantine extended attribute will be dropped from the copied file,” allowing files transferred into the virtual machine to bypass Gatekeeper entirely.
Shockingly, even Apple’s own native command-line tools, such as curl and SCP, fail to enforce the quarantine attribute. This is particularly concerning because these tools are frequently used in automated processes, making them a prime target for attackers looking to deliver malicious payloads without triggering Gatekeeper’s defenses.
The report highlights that “files unarchived by Unix-based command-line unarchiving tools such as Unzip and tar won’t inherit the quarantine extended attribute,” further exposing macOS users to risk.
Upon discovering these vulnerabilities, Unit 42 researchers reached out to the affected developers. Several developers have already responded with fixes. For instance, BetterZip confirmed that they have “been quarantining extracted apps and executables since version 5,” with additional updates to address nested archives. Similarly, iZip acknowledged the issue and plans to release version 4.6, which will set the quarantine attributes correctly.
While Apple has patched past Gatekeeper bypasses, the report emphasizes that Apple’s reliance on third-party developers to implement the quarantine attribute introduces inherent weaknesses. “Gatekeeper’s design relies heavily on the implementation of third-party developers to comply with its security standards,” the report notes. This reliance has allowed vulnerabilities to persist, despite Gatekeeper’s critical role in macOS security.
To mitigate the risks, Unit 42 urges organizations to adopt multi-layered security approaches. By combining Gatekeeper with other security measures, such as endpoint protection and network monitoring, users can better defend against threats that exploit these bypasses.





