GCPGoat: A Damn Vulnerable GCP Infrastructure
Compromising an organization’s cloud infrastructure is like sitting on a gold mine for attackers. And sometimes, a simple misconfiguration or a vulnerability in web applications, is all an attacker needs to compromise the entire infrastructure. Since the cloud is relatively new, many developers are not fully aware of the threatscape and they end up deploying a vulnerable cloud infrastructure.
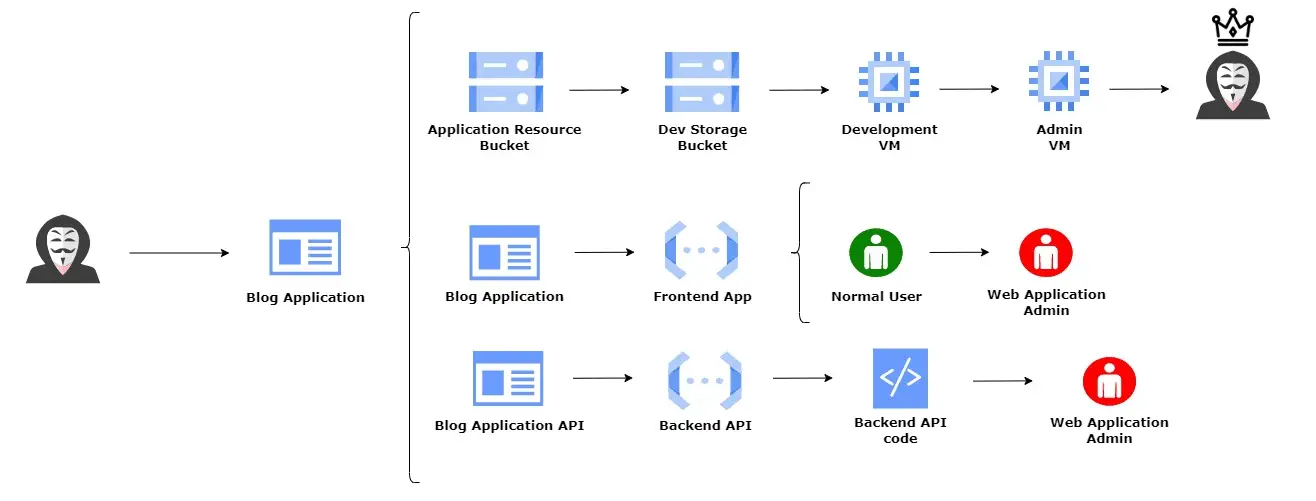
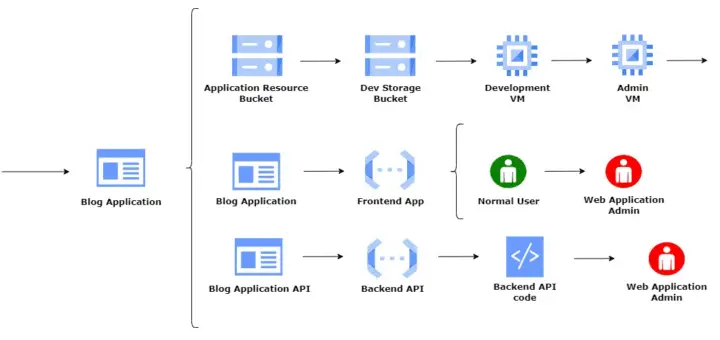
GCPGoat is vulnerable by design infrastructure on GCP featuring the latest released OWASP Top 10 web application security risks (2021) and other misconfiguration based on services such as IAM, Storage Bucket, Cloud Functions, and Compute Engine. GCPGoat mimics real-world infrastructure but with added vulnerabilities. It features multiple escalation paths and is focused on a black-box approach.
GCPGoat uses IaC (Terraform) to deploy the vulnerable cloud infrastructure on the user’s GCP account. This gives the user complete control over code, infrastructure, and environment. Using GCPGoat, the user can learn/practice:
- Cloud Pentesting/Red-teaming
- Auditing IaC
- Secure Coding
- Detection and mitigation
The project will be divided into modules and each module will be a separate web application, powered by varied tech stacks and development practices. It will leverage IaC through terraform to ease the deployment process.
Vulnerabilities
The project is scheduled to encompass all significant vulnerabilities including the OWASP TOP 10 2021, and popular cloud misconfigurations. Currently, the project contains the following vulnerabilities/misconfigurations.
- XSS
- Insecure Direct Object reference
- Server Side Request Forgery on Cloud Function
- Sensitive Data Exposure and Password Reset
- Storage Bucket Misconfigurations
- IAM Privilege Escalations
Install & Use
Copyright (c) 2022 INE