GDA-android-reversing-Tool v4.10 releases: decompiler written entirely in c++
GDA(GJoy Dex Analysizer)
Most reverse engineers mainly use Java decompiler, commercial Dalvik decompiler Jeb, and smali2java to analyze Android APPs. Java decompiler is based on Java bytecode, including JD, JD-GUI, jadx, and others. smali2java is a decompiler based on the Smali code. They have their own shortcomings, such as the Java decompiler depends on the conversion of dex2jar. For complex, obfuscated or packed apks, there is a problem of translation failure. smali2java decompiles Smali code which should be translated from DEX with apktool, so it increases the difficulty and error rate and decreases the speed of manual analysis. In addition, their interaction is poor, which increases the difficulty of manual analysis. Although the commercial Jeb has better interactivity, it is easy to death when analyzing a large-sized APP with the Multidex, and it is very expensive for me…
Here, a new decompiler based on Dalvik bytecode, GDA(this project started in 2013 and released its first version 1.0 in 2015 at www.gda.com: 9090), is proposed and implemented in C++ language to provide more sophisticated, fast, and convenient decompilation support. GDA is completely self-independent. It supports APK, DEX, ODEX, oat files, and run without installation and Java VM support. GDA only takes up 2M of your disk space, and you can use it in any newly installed windows system and virtual machine system. In addition, GDA has more features as follows:
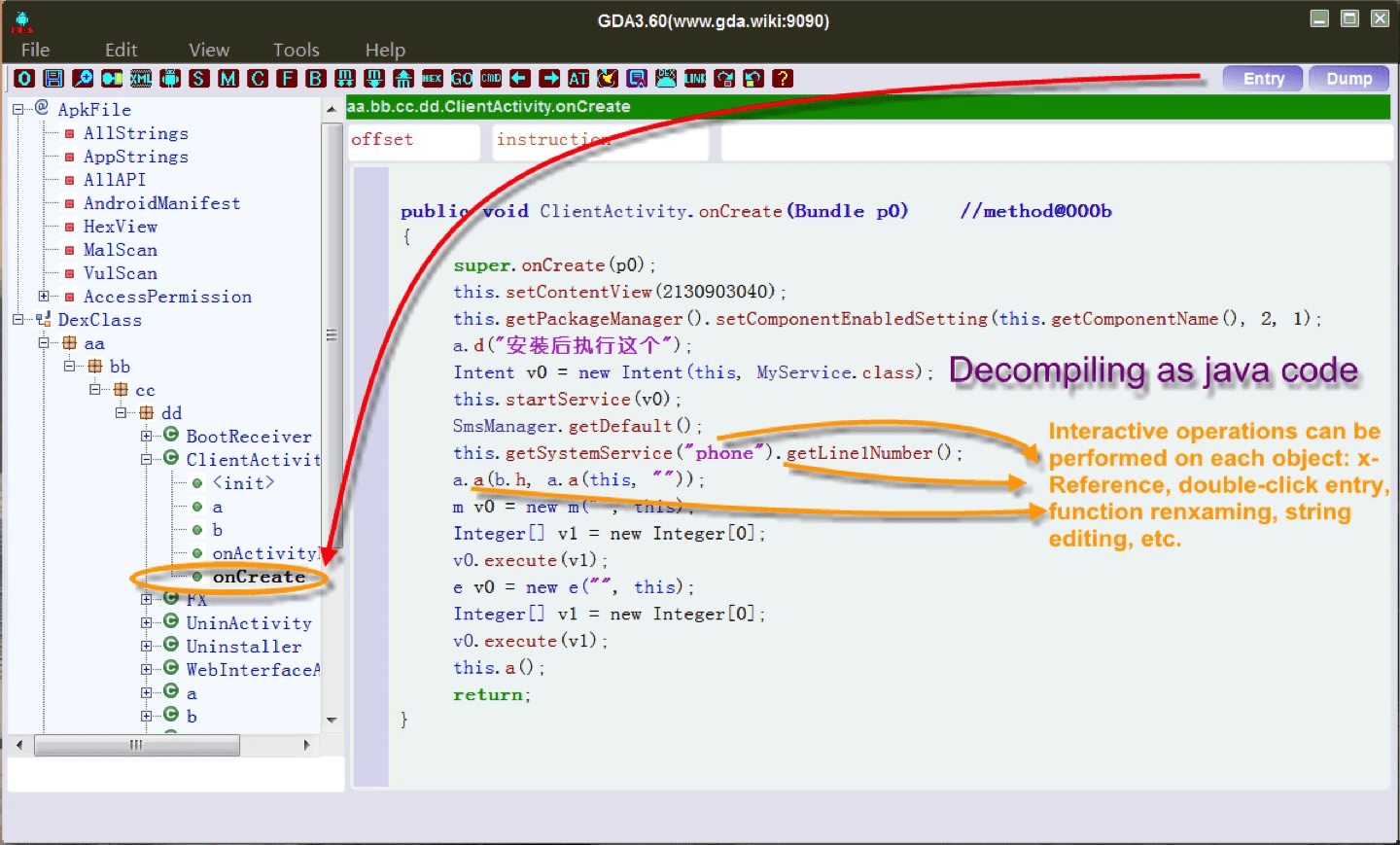
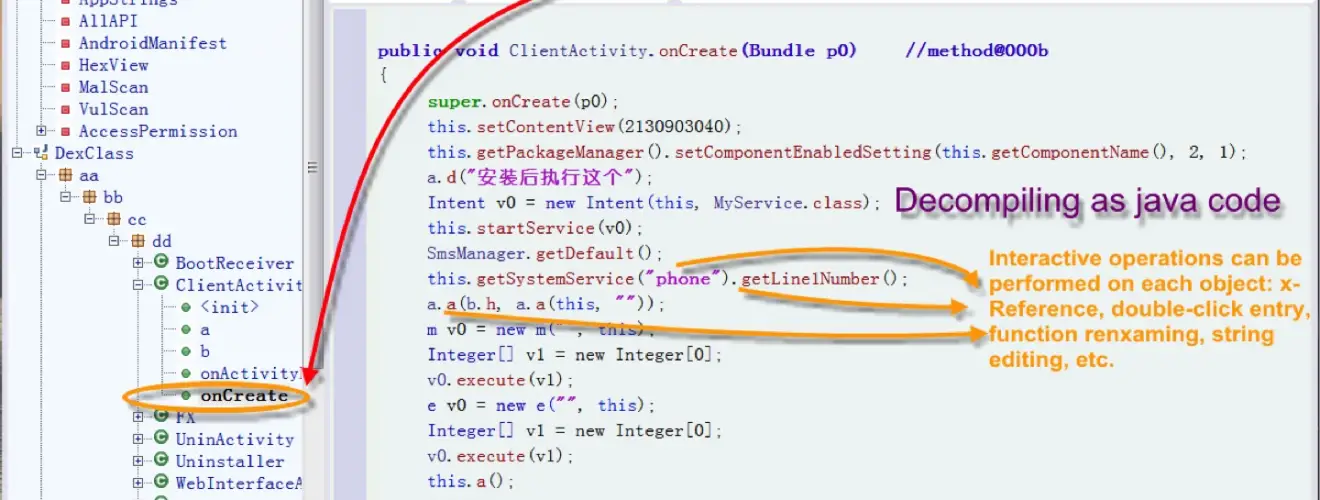
Interactive operation:
1.cross-references for strings, classes, methods and fields;
2.searching for strings, classes methods and fields;
3.comments for java code;
4.rename for methods,fields and classes;
5.save the analysis results in gda db file.
…
Utilities for Assisted Analysis:
1.extracting DEX from ODEX;
2.extracting DEX from OAT;
3.XML Decoder;
4.algorithm tool;
5.device memory dump;
…
New features:
1.Brand new dalvik decompiler in c++ with friendly GUI;
2.Support python script
3.packers Recognition;
4.Multi-DEX supporting;
5.making and loading signature of the method
6.Malicious Behavior Scanning by API chains;
7.taint analysis to preview the behavior of variables;
8.taint analysis to trace the path of variables;
9.de-obfuscate;
10.API view with x-ref;
11.Association of permissions with modules;
…
Changelog v4.10
- Fix the issue of incorrect method icons in search results.
- Fix the bug of null search result in binary search.
- Optimize the preview of binary search results.
- Fix the issue of incorrect position of top button.
- Enhanced XML decoding capabilities.
- Fix the issue of multithreading deadlock.
Download & Use
Copyright [2019] [charles2gan/gjden/GANJIE]