gdbfuzz: Fuzzing Embedded Systems using Hardware Breakpoints
GDBFuzz: Debugger-Driven Fuzzing
This is the companion code for the paper: ‘Fuzzing Embedded Systems using Debugger Interfaces’. A preprint of the paper can be found here. The code allows the users to reproduce and extend the results reported in the paper. Please cite the above paper when reporting, reproducing, or extending the results.

Purpose of the project
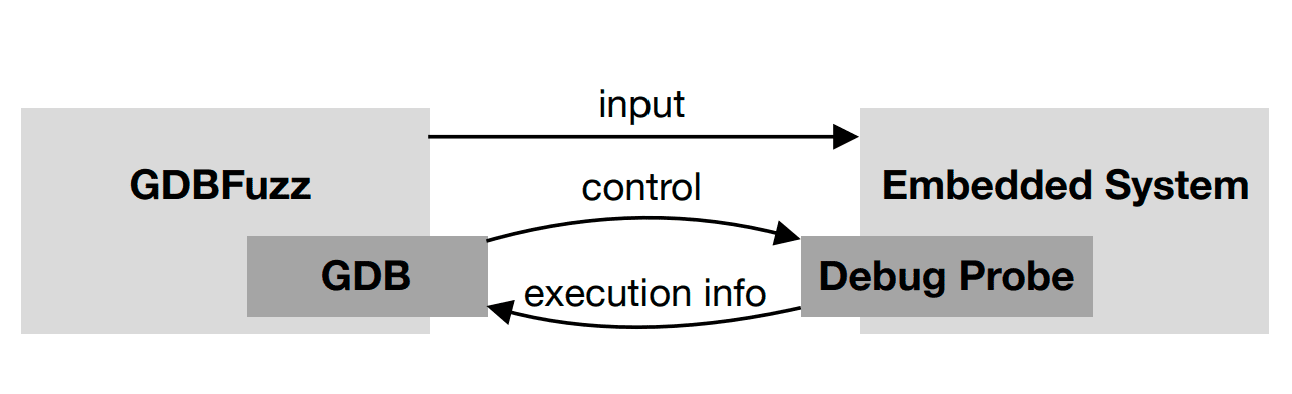
The idea of GDBFuzz is to leverage hardware breakpoints from microcontrollers as feedback for coverage-guided fuzzing. Therefore, GDB is used as a generic interface to enable broad applicability. For binary analysis of the firmware, Ghidra is used. The code contains a benchmark setup for evaluating the method. Additionally, example firmware files are included.
Our evaluation is split in two parts.
- GDBFuzz on its intended setup, directly on the hardware.
- GDBFuzz in an emulated environment to allow independent analysis and comparisons of the results.
GDBFuzz can work with any GDB server and therefore most debug probes for microcontrollers.
GDBFuzz on Linux user programs
For fuzzing on Linux user applications, GDBFuzz leverages the standard LLVMFuzzOneInput entrypoint that is used by almost all fuzzers like AFL, AFL++, libFuzzer,… In benchmark/benchSUTs/GDBFuzz_wrapper/common There is a wrapper that can be used to compile any compliant fuzz harness into a standalone program that fetches input via a named pipe at /tmp/fromGDBFuzz. This allows to simulation of an embedded device that consumes data via a well-defined input interface and therefore runs GDBFuzz on any application. For convenience, we created a script in benchmark/benchSUTs that compiles all programs from our evaluation with our wrapper as explained later.
Install & Use
Copyright (C) 2023 boschresearch





