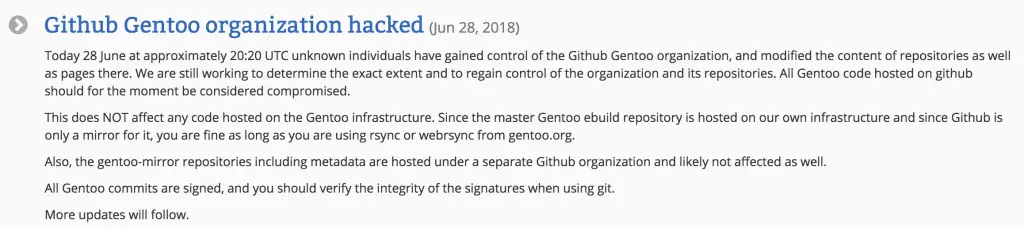
On the evening of June 28, UTC, Gentoo Linux’s Github repository was hacked and successfully took control of the organisation at 20:20. The attacker tampered with the contents of the repository and the page and replaced the files in portage and musl-dev trees with malicious ebuild files in an attempt to delete all files on the repository.
At 21:10 the same day, an official announcement was posted on the Gentoo official website that an unknown individual had gained control of the Github Gentoo organisation. Attempts are being made to confirm the exact scope of the affected area and to regain control of the organisation and its repository. All current Gentoo code hosted on Github is considered risky.
 After that, Gentoo developer Francisco Blas Izquierdo Riera sent an alert email on the mailing list, stressing that although malicious code should not run directly, GitHub has removed the Gentoo organisation, but don’t use it from the mirrored repository until the problem is resolved.
After that, Gentoo developer Francisco Blas Izquierdo Riera sent an alert email on the mailing list, stressing that although malicious code should not run directly, GitHub has removed the Gentoo organisation, but don’t use it from the mirrored repository until the problem is resolved.
On June 29th, Gentoo’s official website released some announcements to explain the progress of the incident: the repository has restored to a functional state, and the related settings have restored. Currently, it is necessary to wait for GitHub official to check and undo unauthorized PR changes in the repository and unlock the Github Gentoo organization and re-add all previous members to the organization. As of press time, the incident has not yet been resolved.