Ghidra EVM Module: Ghidra module for reverse engineering smart contracts
Ghidra EVM Module
In the last few years, attacks on deployed smart contracts in the Ethereum blockchain have ended up in a significant amount of stolen funds due to programming mistakes. Since smart contracts, once compiled and deployed, are complex to modify and update different practitioners have suggested the importance of reviewing their security in the blockchain where only Ethereum Virtual Machine (EVM) bytecode is available. In this respect, reverse engineering through disassemble and decompilation can be effective.
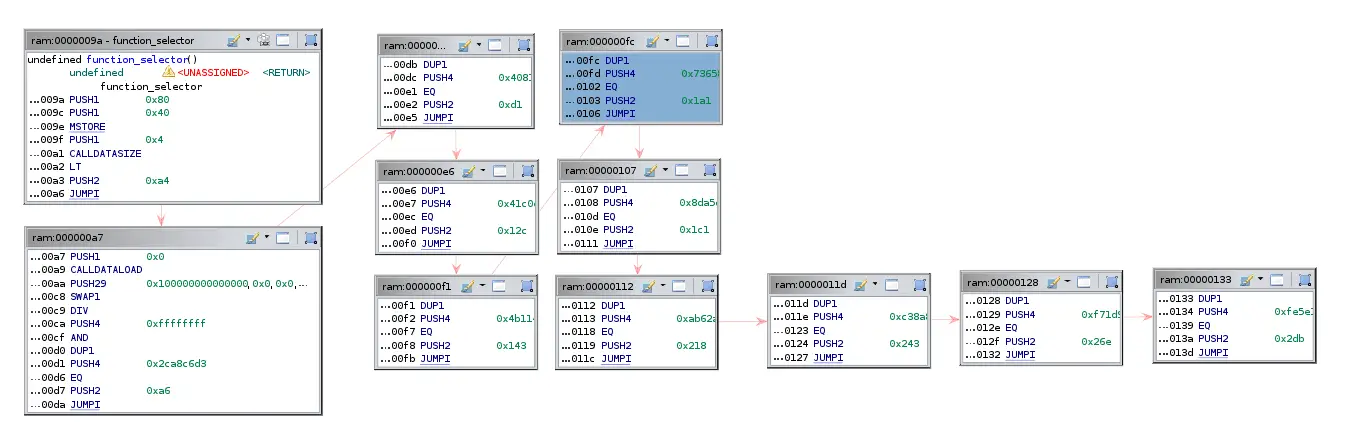
ghidra-EVM is a Ghidra module for reverse engineering smart contracts. It can be used to download Ethereum Virtual Machine (EVM) bytecode from the Ethereum blockchain and disassemble and decompile the smart contract. Further, it can analyze creation code, find contract methods and locate insecure instructions.
It comprises a processor module, custom loader, and plugin(s) that disassembles Ethereum VM (EVM) bytecode and generates a control-flow graph (CFG) of a smart contract.
The last version uses the Ghidra 9.1.2 API. It relies on the crytic evm_cfg_builder library to assist Ghidra in the CFG generation process.
Ghidra-evm consists of:
- A loader that reads byte and hex code from .evm and .evm_h files respectively (See examples).
- The SLEIGH definition of the EVM instruction set taking into account the Ghidra core limitations (See Notes).
- A helper script that uses evm_cfg_builder and ghidra_bridge in order to assist ghidra in generating the CFG and exploring the functional properties of a smart contract.
- A collection of scripts that help to reverse engineering different aspects of a smart contract:
| Script | Description |
|---|---|
| search_codecopy.py | When analyzing creation code in a smart contract we can only see the _dispatcher function that uses CODECOPY in order to write the run time code into memory. This script looks for useful CODECOPY instructions and finds the smart contract methods hidden in the runtime part of the contract. |
| search_dangerous_instructions.py | Instructions such as CALL, CALLCODE, SELFDESTRUCT, and DELEGATECALL can sometimes be abused to transfer funds to another contract. This script finds them and creates a label for each occurrence. |
| load_external_contract.py | Downloads smart contract byte code from the blockchain into a .evm_h file that can be loaded into ghidra-evm |
Install & Use
Copyright (C) 2020 adelapie





