Image: ThreatFabric
ThreatFabric reveals a new tactic allowing fraudsters to anonymously drain stolen credit cards linked to mobile wallets.
A new and concerning trend in financial cybercrime has surfaced, dubbed “Ghost Tap” by researchers at ThreatFabric. This tactic allows criminals to remotely and anonymously cash out stolen credit cards linked to mobile payment services like Apple Pay and Google Pay by relaying Near Field Communication (NFC) signals.
“During our recent investigations, ThreatFabric analysts came across a new cash-out tactic being actively used by the threat actors as well as promoted on underground forums,” reveals the report. This tactic involves using readily available tools to bridge the gap between a compromised device and a point-of-sale (POS) terminal, effectively turning contactless payments into a ghost story for victims.
How Ghost Tap Works
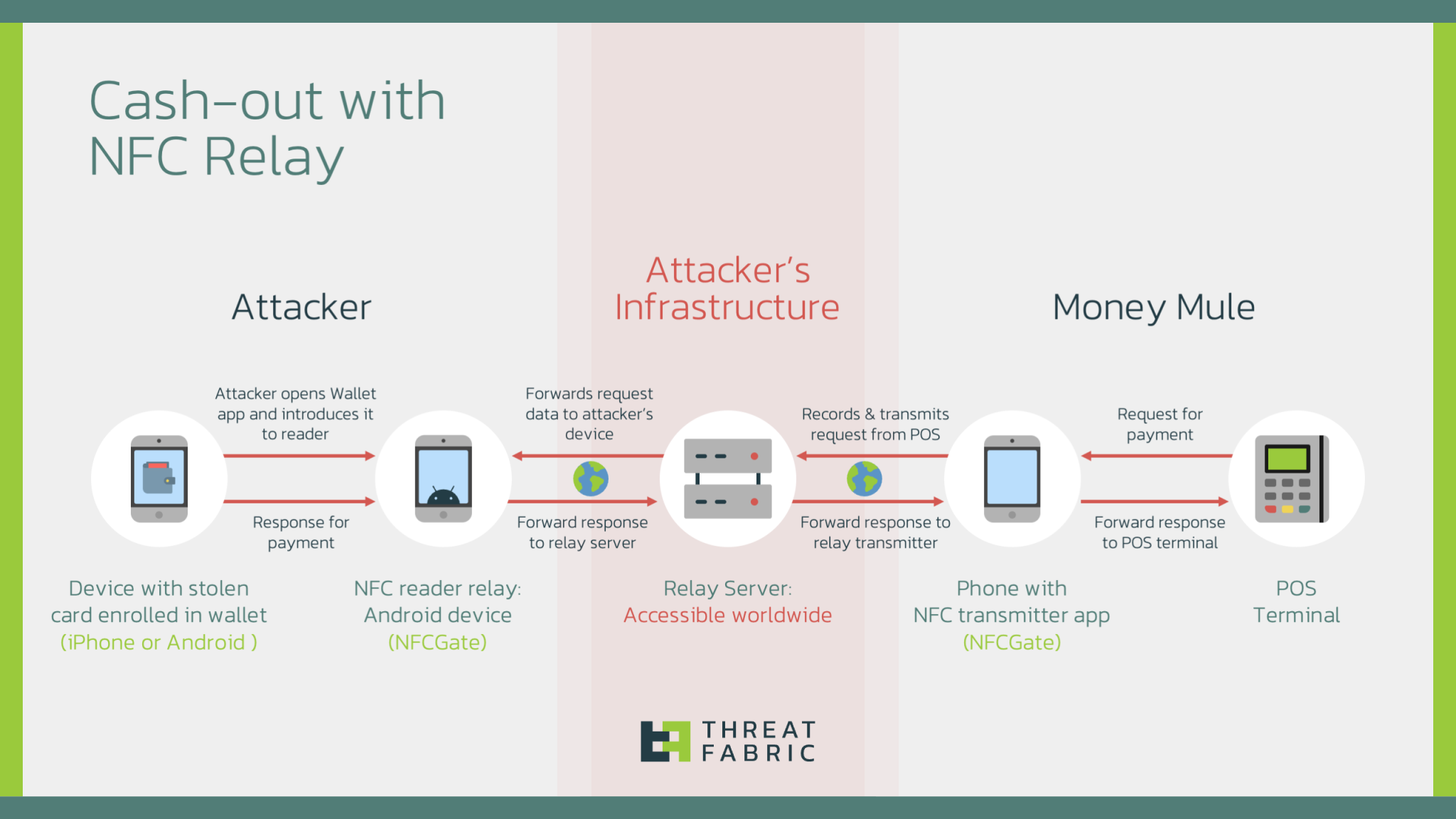
The scheme involves three key players:
- The Attacker: Possesses the stolen credit card details and a device enrolled with the compromised card in a mobile wallet.
- The Mule: An individual who physically interacts with the POS terminal at a retail location to make fraudulent purchases.
- The Relay: A server and software like NFCGate, which facilitates the communication between the attacker’s device and the mule’s device, relaying the NFC signals necessary for the transaction.
“The cybercriminal with stolen card can be far away from the location (even different country) where the card will be used as well as use the same card in multiple locations within short period of time,” explains the report, highlighting the increased anonymity and scalability this tactic offers.
Challenges for Detection and Prevention
Ghost Tap presents a significant challenge for financial institutions because it bypasses traditional fraud detection mechanisms. The transactions appear to originate from the legitimate user’s device, often involve small amounts to avoid suspicion, and can be conducted across geographically disparate locations, making it difficult to track and identify fraudulent activity.
“The challenge to detect Ghost Tap arises because of the several reasons: The transactions appear to come from the same device… The amounts spent with one transaction can be rather low… The device with linked card might be put in ‘airplane’ mode, making it more complicated to identify the location,” states the report.
Mitigation Strategies
ThreatFabric recommends that financial organizations adopt proactive measures to counter this emerging threat. These include:
- Enhanced Monitoring: Closely monitor for suspicious events like cards linked to new devices, especially when paired with known mobile malware infections on customer devices.
- Location-Based Analysis: Analyze transaction patterns for inconsistencies between the device’s location and the payment location.
- Behavioral Biometrics: Implement behavioral biometrics to detect anomalies in user behavior that could indicate account compromise.