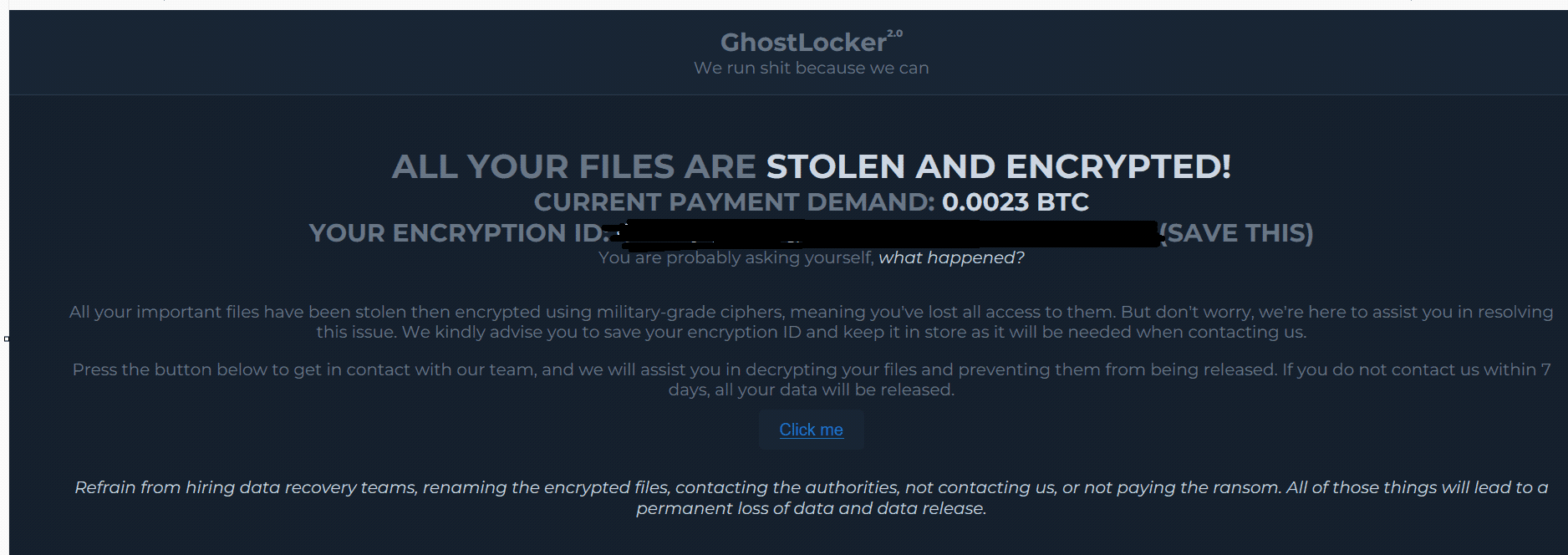
Ransomware note
A new technical analysis by Seqrite cybersecurity researchers has revealed alarming upgrades to the GhostLocker ransomware. This notorious Ransomware-as-a-Service (RaaS) framework, operated by the hacktivist group GhostSec, has undergone a significant evolution. Its new iteration, GhostLocker 2.0, poses an even more severe threat to businesses and individuals worldwide.
The Evolution of GhostLocker
First launched in October 2023, GhostLocker quickly gained popularity among cybercriminals. Its RaaS model allows even less-skilled threat actors to purchase and deploy the ransomware for attacks. A recent, successful collaboration with the Stormous ransomware group has further bolstered GhostLocker’s reach and resources.

GhostLocker 2.0 builds upon the original version, demonstrating the active development and sophistication of this threat. Key upgrades include:
- Programming Shift: GhostLocker 2.0 is now written in the Golang programming language, making it potentially more difficult to analyze and detect.
- Enhanced Exfiltration: Before encrypting files, the ransomware now exfiltrates sensitive data to the attackers’ control servers. This enables double extortion tactics where victims are pressured to pay ransoms to prevent both the release of their data and the restoration of their systems.
- Expanded Global Reach: Seqrite’s analysis reveals GhostLocker 2.0 campaigns impacting countries like Brazil, India, China, South Africa, Egypt, Turkey, and many others.
Technical Breakdown
Variant 1: The Python Progenitor
Variant 1 of Ghost Locker establishes its persistence stealthily by embedding itself into the Windows Startup folder. It identifies all drives on the victim’s machine to prepare for the encryption process and creates a unique 32-byte ID for each infected system. This ID, along with other crucial data such as the victim’s IP address and infection details, is compiled into a JSON file and communicated to the C2 (Command and Control) server.
Encryption is achieved using the AES algorithm with a 256-bit key length, ensuring strong encryption of the victim’s files. Post-encryption, the ransomware deploys a ransom note directly on the user’s desktop, intensifying the urgency for the victim to comply.
Variant 2: The Golang Advance
The evolution to Golang in variant 2 underscores a significant technical leap. This variant shares core functionalities with its predecessor but with notable enhancements:
- Connectivity Dependency: It requires a successful connection to its new C2 server to execute, reflecting a more network-dependent architecture.
- Exfiltration Tactics: Targeting primarily office document formats like .docx and .xlsx, this variant uploads the files to the C2 server before encrypting them, suggesting a dual focus on data theft and ransom.
- Process Termination: To evade detection, it terminates specific processes and services defined by the threat actor, showcasing an adaptive approach to maintaining stealth.
Global Impact and Security Implications
The widespread impact of Ghost Locker 2.0 across multiple continents underscores the global threat posed by sophisticated ransomware operations. Countries with significant digital infrastructure, such as India and China, are particularly vulnerable due to the high volume of potential high-value targets.
This evolution of ransomware highlights the necessity for robust cybersecurity measures. Organizations must adopt advanced threat detection and response strategies to mitigate the risks posed by ransomware variants like Ghost Locker. Regular data backups, employee training on phishing and other common attack vectors, and a strong security posture are essential to defend against these evolving cyber threats.