Cisco Talos observed a collaborative effort between the GhostSec and Stormous ransomware groups, conducting double extortion attacks leveraging GhostLocker and StormousX. Their activities were revealed through Telegram communications and the Stormous data leak site.
The Alliance of Cyber Menace

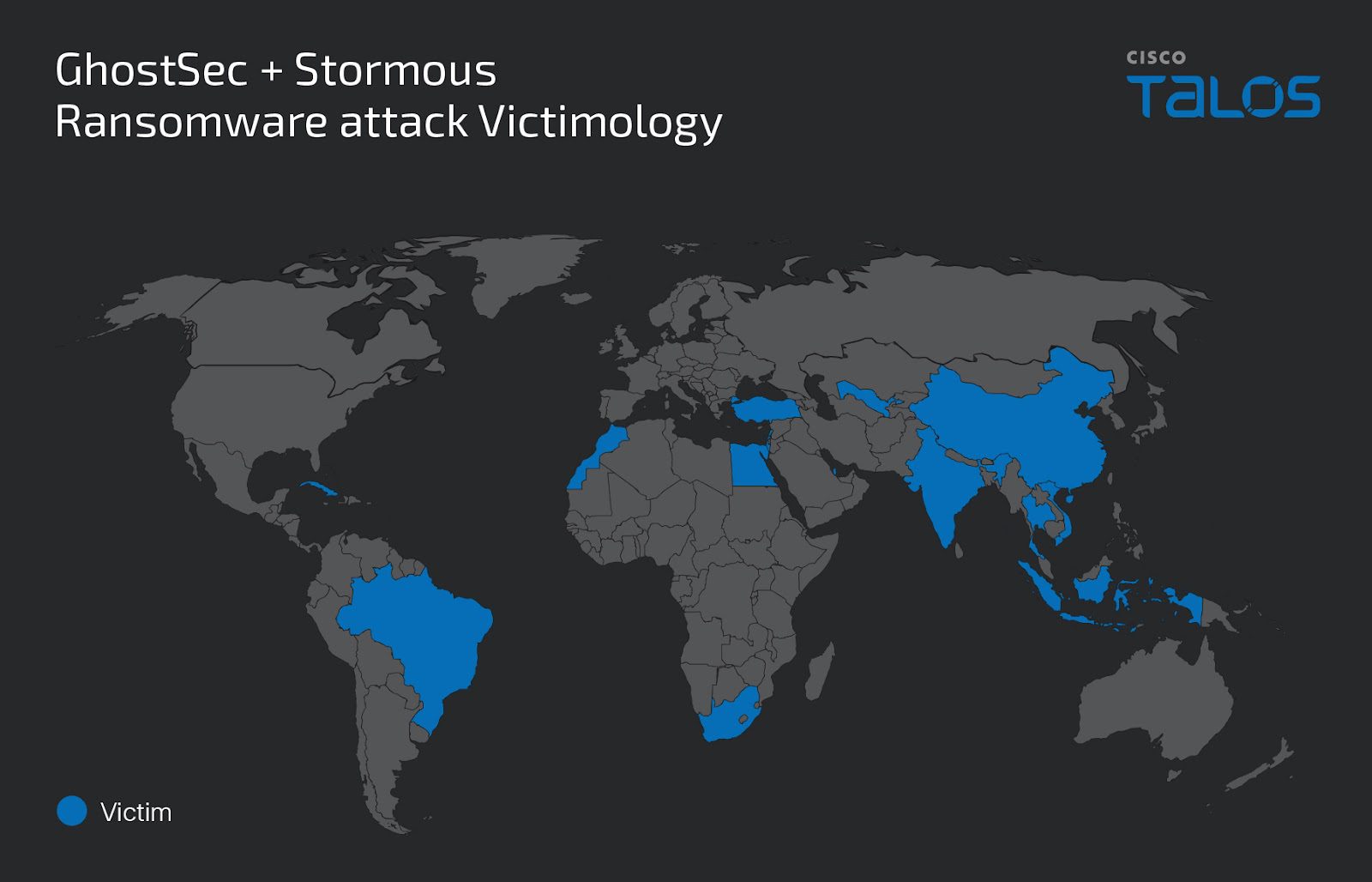
In a series of meticulously orchestrated attacks, the collaboration between GhostSec and Stormous has been at the forefront of a disturbing trend in cybersecurity threats. Utilizing their proprietary ransomware programs, GhostLocker and StormousX, these groups have launched a spree of double extortion attacks. Their reach spans across continents, impacting nations from Cuba to Indonesia, and targeting a diverse range of business verticals.
The operation is distinguished by its broad scope and the deliberate targeting of critical infrastructure and technology companies, including a notable attack on Israel’s Ministry of Defense. Such actions underscore the groups’ sophisticated capabilities and their intent to compromise vital sectors for financial gain.
The GhostSec ransomware group
GhostSec claims affiliation with other notorious groups, forming a coalition that operates under the guise of hacktivism. However, their activities reveal a starkly different motive: financial extortion. Through their cybercriminal endeavors, GhostSec aims to fund further operations, leveraging a variety of tactics from ransomware to denial-of-service attacks to achieve their objectives.
Interestingly, GhostSec’s nomenclature draws an unintended parallel with the Ghost Security Group, a hacktivist entity focused on counterterrorism. This resemblance has led to public confusion, a factor that GhostSec might be exploiting to veil their nefarious activities under a cloak of legitimacy.
The Evolution of GhostLocker
In a significant development, GhostSec unveiled GhostLocker, a ransomware-as-a-service (RaaS) platform, heralding a new action in their operations. This move was closely followed by Stormous adopting GhostLocker for their campaigns, marking a deepening of their partnership. This collaboration not only amplifies their threat potential but also showcases their ability to innovate and adapt in the ever-changing cyber threat landscape.
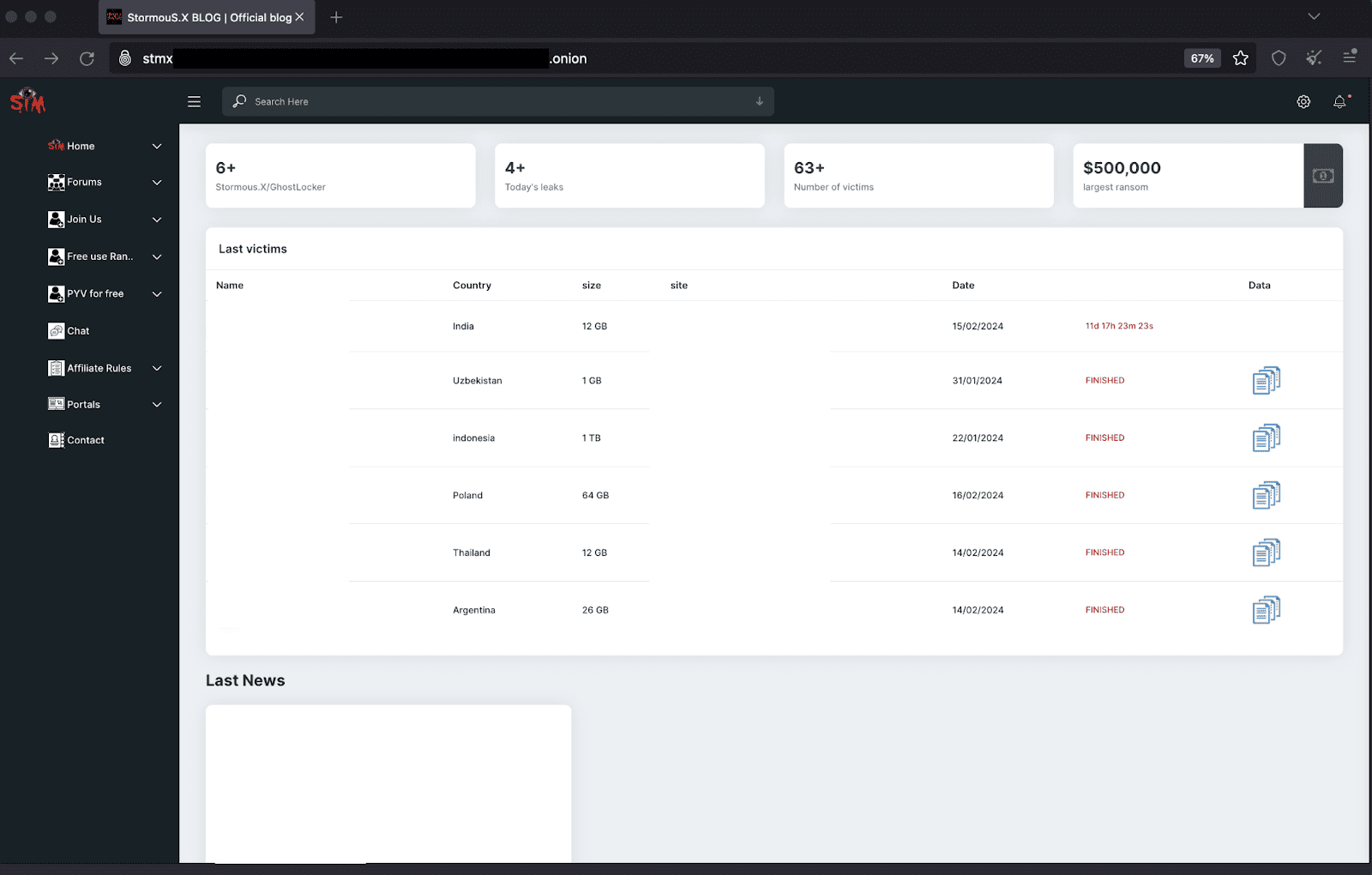
The RaaS model has democratized the process of launching ransomware attacks, offering paid and free services to affiliates. This approach has expanded their reach and impact, as evidenced by their new official blog on the TOR network, which serves as a hub for affiliates and a showcase of their conquests.
GhostLocker 2.0: A New Threat on the Horizon
With the announcement of GhostLocker 2.0, GhostSec signaled their commitment to evolving their tools and tactics. This new variant, boasting enhancements and a streamlined operation, represents a significant evolution from its predecessor. The ransomware not only establishes persistence on infected machines but also exfiltrates and encrypts critical files, leaving a ransom note that serves as a reminder of the attack.
Beyond Ransomware: Expanding the Arsenal
GhostSec’s repertoire extends beyond ransomware, with tools designed to compromise and exploit websites. The GhostSec Deep Scan toolset and GhostPresser, a WordPress hacking tool, indicate a strategic expansion of their capabilities, targeting the presence of businesses and organizations.
The Challenge of Evolving Threats
The GhostSec/Stormous alliance is a stark example of the sophisticated, ever-evolving threats faced by businesses. Vigilance, proactive security measures, and continuous adaptation are vital for staying ahead of these determined adversaries.