
A team of researchers from the CISPA Helmholtz Center for Information Security has disclosed a critical vulnerability, named GhostWrite, affecting T-Head XuanTie C910 and C920 RISC-V CPUs. This hardware-level flaw enables unprivileged attackers to bypass security measures and gain full control over affected devices, posing a significant risk to the security and integrity of numerous systems.
RISC-V has been hailed as a revolutionary open Instruction Set Architecture (ISA), offering a free and flexible alternative to the dominant x86 and ARM ISAs, which are controlled by a select few companies. This openness has spurred rapid innovation and widespread adoption, with RISC-V processors being deployed in everything from cloud servers to personal computers. However, the discovery of GhostWrite raises serious concerns about the security of this promising architecture.
GhostWrite is a direct CPU bug that resides within the vector extension of the T-Head XuanTie C910 and C920 processors. Unlike other well-known vulnerabilities that rely on side-channel or transient-execution attacks, GhostWrite operates through faulty instructions embedded in the hardware. These instructions interact directly with physical memory, bypassing the virtual memory protections that are typically enforced by the operating system and hardware.
This flaw allows even unprivileged users to write to any memory location, completely ignoring the security and isolation features designed to protect the system. The attack is not only highly reliable and deterministic but also takes only microseconds to execute, making it a potent tool in the hands of malicious actors.
One of the most concerning aspects of GhostWrite is its ability to hijack hardware devices that use memory-mapped input/output (MMIO). This means that an attacker could potentially take control of network cards, storage devices, or other critical components, further amplifying the potential damage.
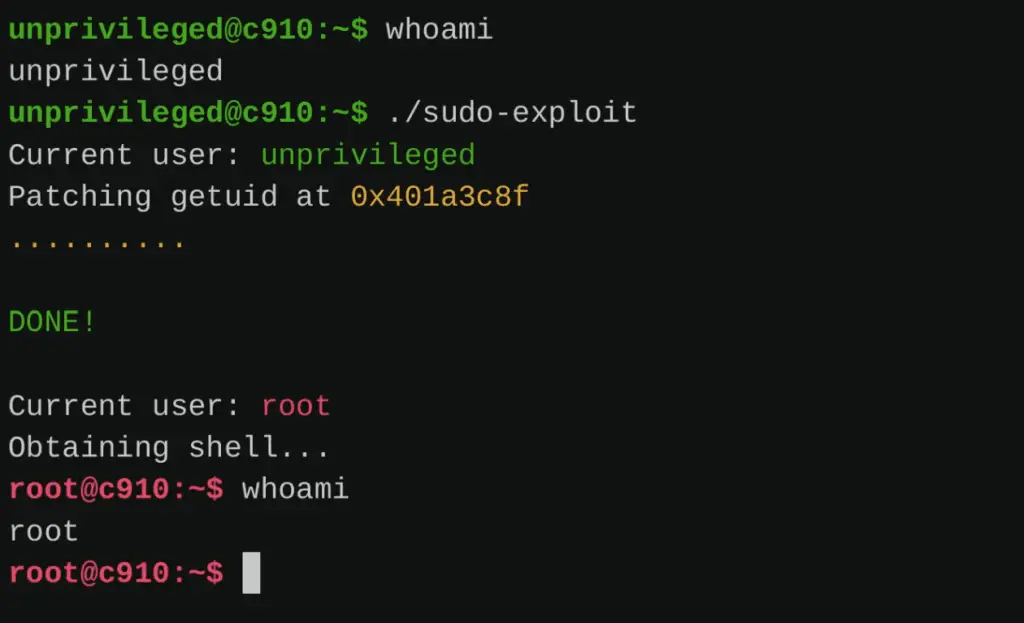
The research team demonstrated the devastating potential of GhostWrite with two proof-of-concept exploits. In the first, they used GhostWrite to modify the kernel’s getuid syscall, which checks a user’s ID to determine access permissions. By altering this function, the exploit granted root access without the need for a password, effectively giving the attacker full control over the system.
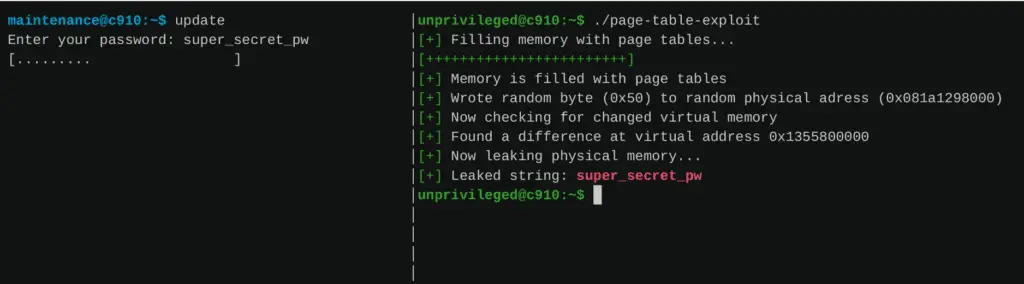
The second exploit showcased GhostWrite’s ability to leak sensitive information from memory. The researchers simulated a scenario in which an administrator enters a secret password into a trusted prompt. Using GhostWrite, they filled the system’s physical memory with page tables, which allowed them to modify these tables and read the secret password directly from physical memory—demonstrating the vulnerability’s capability to compromise even the most secure operations.
GhostWrite’s impact is far-reaching, affecting a wide array of devices that use the T-Head XuanTie C910 and C920 CPUs. These include:
- Scaleway Elastic Metal RV1, bare-metal C910 cloud instances
- Milk-V Pioneer, a 64-core desktop/server
- Lichee Cluster 4A, a compute cluster
- Lichee Book 4A, a laptop
- Lichee Console 4A, a tiny laptop
- Lichee Pocket 4A, a gaming console
- Sipeed Lichee Pi 4A, a single-board computer (SBC)
- Milk-V Meles, an SBC
- BeagleV-Ahead, an SBC
Given the severity of GhostWrite, the only effective mitigation is to disable the vulnerable vector extension entirely. However, this comes at a significant cost, as it effectively disables around 50% of the CPU’s functionality, severely impacting performance and capabilities.
For now, vendors and users of affected devices are urged to take immediate action by disabling the vector extension and staying informed about any further developments or patches.
Update on August, 18th: This attack is tracked as CVE-2024-44067.
Related Posts:
- Intel: CPUs affected by the vulnerabilities will be fully repaired by the end of January
- Google, Samsung, and Qualcomm Support Open Source RISC V Processor