GHunt
GHunt is an OSINT tool to extract information from any Google Account using an email.
It can currently extract:
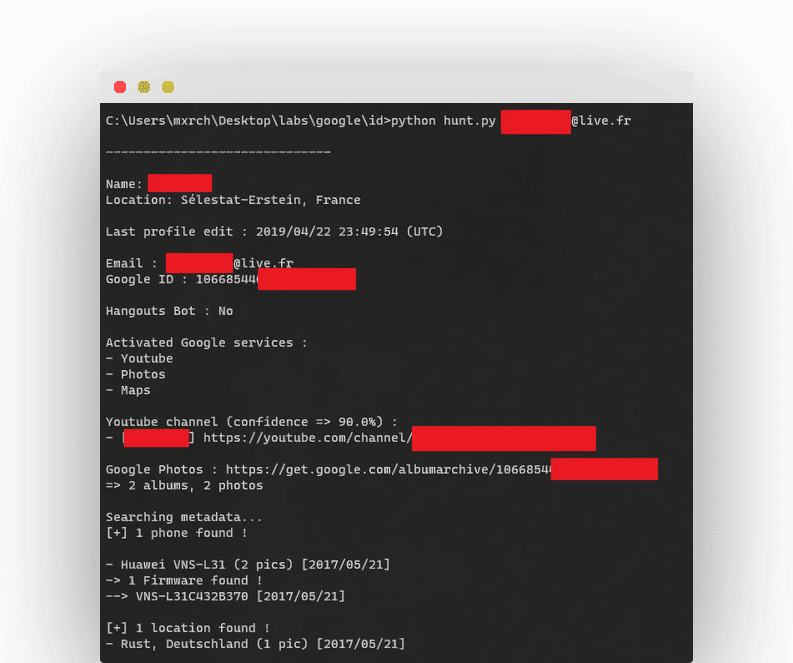
- Owner’s name
- The last time the profile was edited
- Google ID
- If the account is a Hangouts Bot
- Activated Google services (YouTube, Photos, Maps, News360, Hangouts, etc.)
- Possible YouTube channel
- Possible other usernames
- Public photos (P)
- Phones models (P)
- Phones firmwares (P)
- Installed Softwares (P)
- Google Maps reviews (M)
- Possible physical location (M)
- Events from Google Calendar (C)
The features marked with a (P) require the target account to have the default setting of Allow the people you share content with to download your photos and videos on the Google AlbumArchive, or if the target has ever used Picasa linked to their Google account.
More info here.
Those marked with a (M) require the Google Maps reviews of the target to be public (they are by default).
Those marked with a (C) requires user to have Google Calendar set on public (default it is closed)
Changelog v2.1
NO MORE COOKIES! This is the biggest change. The authentication is now done through the OAuth token.
I was inspired by the hackers that recently abused the accounts.google.com/oauth/multilogin to generate cookies from a Chrome Desktop token. I adapted this feature to generate cookies on-the-fly, but from an Android master token.
So, it should fix all the known issues for the GHunt’s login step, and improve long-term stability.
All of these changes are compatible with the current GHunt Companion extension.
Other improvements
- Auto check for updates at launch.
- Replaced
triobyasyncio. - Replaced
setup.pybypyproject.toml
Install & Use
Copyright (C) 2022 mxrch