Github-Hunter: sensitive information searching on Github
Github-Hunter
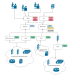
This tool is for sensitive information searching on Github.

Installation
Requirements
- Python 3.x
1.git clone https://github.com/Hell0W0rld0/Github-Hunter.git
2.cd Github-Hunter
3.pip install virtualenv
4.virtualenv –python=/usr/local/bin/python3 env
5.source venv/bin/activate
6.pip install -r requirements
Settings
Before using it, you must change parameters in info.ini.example, then change filename(just delete .example)
Example
Keyword and Payloads
The keyword is the main keyword, such as your company name, email, etc.
The payloads searching is based on the main keyword’s results. You can customize your payloads, the more you add, the more sensitive information will be found.
Run
python GithubHunter.py
You will receive a .csv file and emails when application complete.
CSV file includes repositories’ url、user、upload data、filename which are the best match of the main keyword.
The emails will be sent contain urls which certainly include sensitive information.
Source: https://github.com/Hell0W0rld0/