GitHub announced a Python security warning that allows Python users to access dependency graphs and receive alerts when there are security vulnerabilities in the packages that their libraries depend on.
The security warning was first released in October 2017 to track security vulnerabilities in Ruby and JavaScript packages. According to GitHub, millions of vulnerabilities have been discovered since then, driving the release of many patches.
GitHub tracks public security vulnerabilities in Ruby gems, NPM, and Python packages based on MITRE’s Common Vulnerabilities List (CVE). CVE is a list of entries; each entry contains an identification number, a description, and at least one public reference. This is very helpful in motivating administrators to respond quickly, by removing vulnerable dependencies or by migrating to a secure version.
When GitHub receives a newly released vulnerability notification, it scans the public library ( the private library that has been selected for inclusion will also be scanned). When a vulnerability is discovered, a security warning is sent to the owner of the affected library and a user with administrator privileges. By default, users receive an email every week containing security warnings for up to 10 libraries. Users can also choose to receive security alerts via email, daily summary email, web notifications, or the GitHub user interface. Users can adjust the notification frequency on the notification settings page.
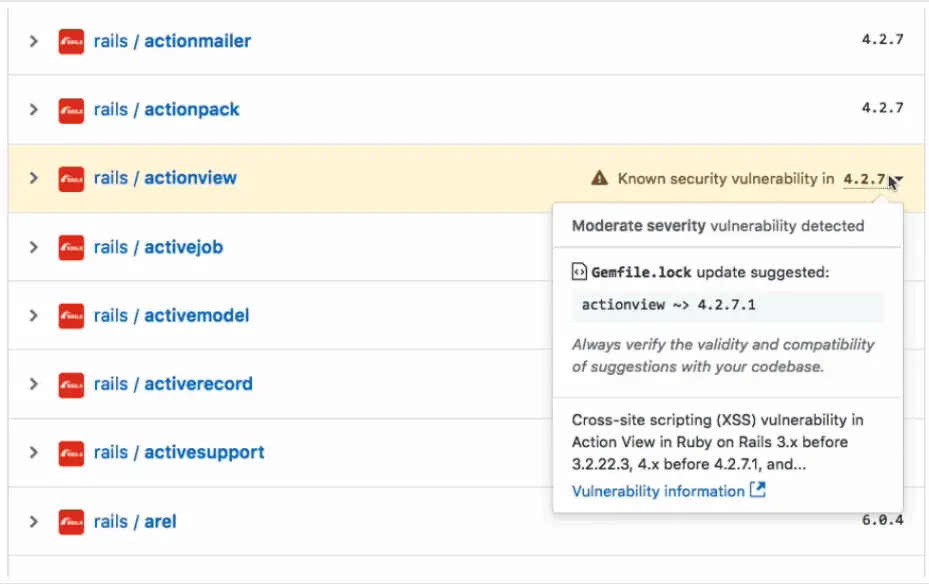
In some cases, GitHub will try to use machine learning to provide fix suggestions for each vulnerability found. Security warnings for vulnerable dependencies include a security level and a link to the project’s affected files, and if available, links to CVE records and fix suggestions. The Common Vulnerability Scoring System(CVSS) defines four possible levels, low, medium, high, and severe.

According to GitHub, in the beginning, security warnings only cover the latest vulnerabilities and add more Python history vulnerabilities in the next few weeks. Also, GitHub will never publicly disclose any vulnerabilities found in the library.
The dependency graph lists all the dependencies of the project, from which the user can see the items affected by the security warning. To view the dependency graph, click Insights in the project and then click Dependency graph.
To use dependency graphs in a Python project, you need to define project dependencies in the requirements.txt or pipfile.lock file. GitHub strongly recommends that users define dependencies in the requirements.txt file.
For more information, check out the GitHub documentation.