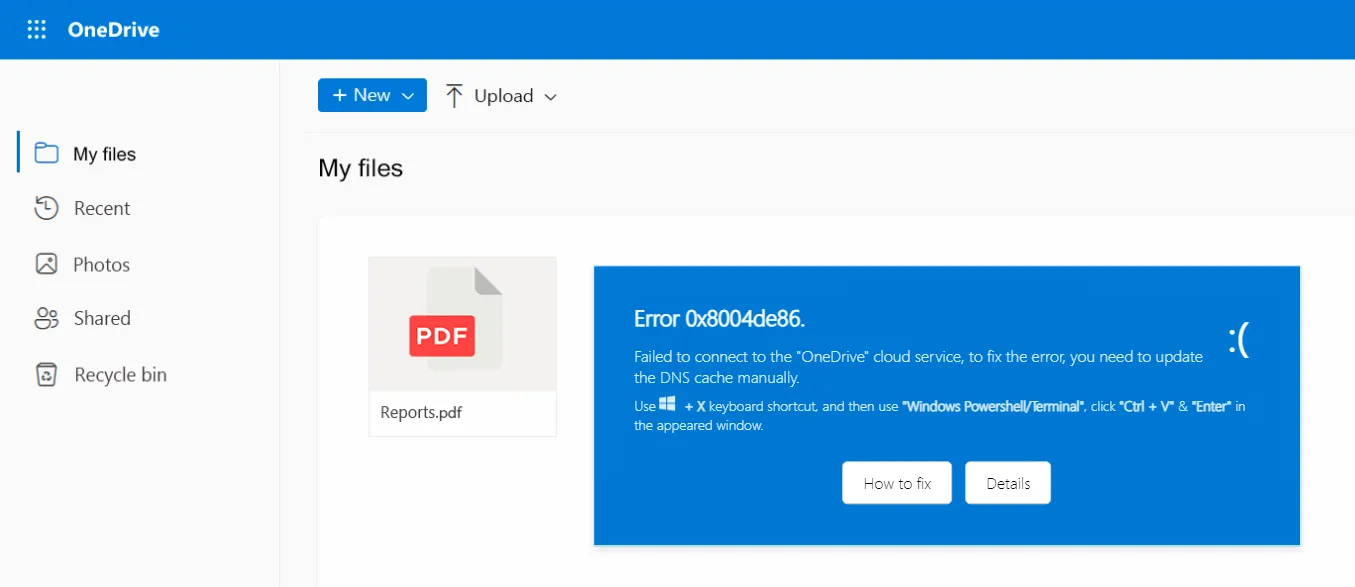
Example ClickFix HTML page being distributed in phishing email attachments | Image: Gen Digital
In a recent analysis by Jan Rubín, Senior Malware Researcher at Gen Digital, a new malware known as Glove Stealer has been identified as a potent information stealer targeting a wide array of browser data and locally installed applications. Written in .NET, Glove Stealer exhibits a focused approach on exfiltrating sensitive data, including cookies, autofill data, cryptocurrency wallets, and 2FA authenticators.
Glove Stealer relies heavily on social engineering tactics to spread. It often appears in phishing campaigns as a seemingly helpful tool, such as ClickFix, which tricks users into thinking they are troubleshooting a system issue. “Tactics like these deceive users into thinking they are helping themselves, but by following the instructions from the attackers, they are actually inadvertently infecting their own devices,” explains Rubín.
The phishing email typically contains an HTML attachment mimicking a fake error message, prompting users to execute a malicious script via PowerShell or a Run prompt. The malware itself is downloaded as an encoded payload from a server, where it ultimately initiates its data-stealing operations.
One of the more advanced capabilities of Glove Stealer is its ability to bypass Google Chrome’s App-Bound encryption, introduced in Chrome version 127. To achieve this, Glove Stealer uses a dedicated module that leverages the IElevator service, a method publicly disclosed in October 2024. The bypass allows Glove Stealer to access otherwise protected Chrome data, including cookies and stored passwords. Rubín explains, “This bypass method involves using an IElevator service,” enabling attackers to retrieve App-Bound keys critical for decrypting protected information.
The module, disguised as zagent.exe, is strategically placed in Chrome’s Program Files directory. This positioning is essential because App-Bound encryption validates the path of the caller process, meaning that Glove Stealer must have local admin privileges to execute this module successfully.
Glove Stealer doesn’t limit itself to Chrome. It also targets other popular browsers like Firefox, Edge, Brave, and even cryptocurrency-focused browsers like CryptoTab. The malware systematically terminates browser processes and then collects data in an organized structure, saving it in folders named Cookies, Autofill, OTP, and Wallets. This method allows attackers to capture a comprehensive snapshot of the victim’s online activities and sensitive information.
With its reach extending to over 280 browser extensions and 80 locally installed applications, Glove Stealer’s targets include cryptocurrency wallet extensions, 2FA tools like Google Authenticator and LastPass, and email clients such as Thunderbird.
After collecting the data, Glove Stealer organizes it within a unique directory path based on the victim’s recent files, tagged with an MD5 hash generated from the device’s name and serial number. Once the data collection is complete, it’s packed and encrypted using 3DES encryption in ECB mode. This encrypted package is then sent to a command-and-control (C&C) server as a Base64-encoded file, adding an additional layer of concealment to the exfiltration process.
As Rubín concludes, “Glove Stealer is capable of stealing various kind of information from many browsers, including Chrome, Firefox, Edge, Brave and others” signaling the need for heightened awareness and strong security practices.
Related Posts:
- Malicious Chrome Extension Infects Over 100,000 Users
- Chrome will no longer flag HTTPS pages as secure sites