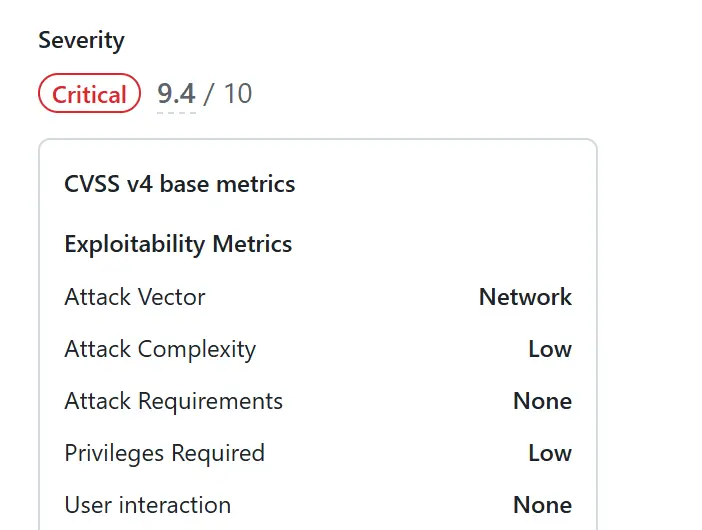
Open-source CI/CD platform GoCD has released an urgent security update to address a critical vulnerability, CVE-2024-56320 (CVSS 9.4), that could allow malicious authenticated users to escalate their privileges to administrator level.
The vulnerability, identified in GoCD versions prior to 24.5.0, stems from “improper authorization of access to the admin ‘Configuration XML’ UI feature, and its associated API.” This flaw could enable attackers to gain unauthorized access to sensitive information and potentially take complete control of the GoCD system.
According to the official security advisory, “a malicious insider/existing authenticated GoCD user with an existing GoCD user account could abuse this vulnerability to access information intended only for GoCD admins, or to escalate their privileges to that of a GoCD admin in a persistent manner.”
The GoCD project emphasizes that this vulnerability cannot be exploited without prior authentication. “It is not possible for this vulnerability to be abused prior to authentication/login,” the advisory states.
Immediate Action Recommended
Users are strongly urged to update to GoCD version 24.5.0, which includes the necessary patch to remediate this vulnerability.
For those unable to immediately upgrade, the GoCD project suggests implementing temporary mitigation measures:
- Block access to vulnerable paths: Utilize a reverse proxy, web application firewall (WAF), or similar security mechanism to block external access to paths with the /go/rails/ prefix. “Blocking this route causes no loss of functionality,” assures the advisory.
- Reduce the user base: Limit access to GoCD to a smaller group of trusted users. This may involve temporarily disabling plugins like the “guest-login-plugin,” which allows limited anonymous access.
Organizations using GoCD are urged to take immediate action to protect their CI/CD pipelines from potential compromise.