Attack chain | Image: TrendMicro
A recent discovery by cybersecurity researchers at Trend Micro has unveiled a sophisticated new attack vector targeting Atlassian Confluence servers, leveraging the critical CVE-2023-22527 vulnerability. This insidious campaign employs the ‘Godzilla’ backdoor, a Chinese-developed, fileless malware known for its ability to operate in-memory, effectively evading traditional security solutions.
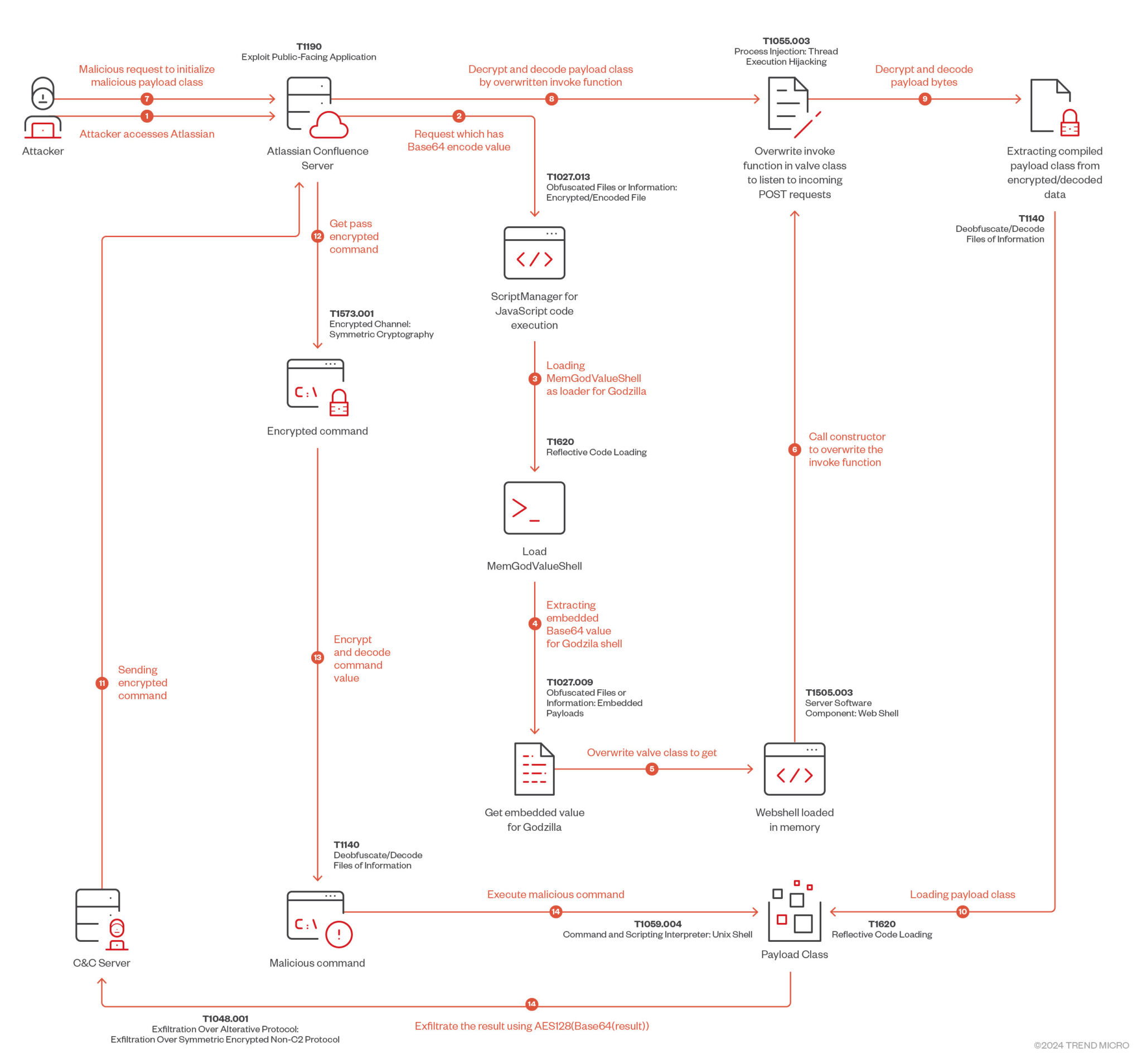
The attack initiates with the exploitation of the CVE-2023-22527 vulnerability, which, if left unaddressed, allows remote code execution on vulnerable Confluence Data Center and Server instances. Following successful exploitation, a malicious loader is deployed onto the compromised server. This loader, acting as a conduit for further malicious activity, subsequently injects the stealthy Godzilla webshell into the server’s memory.
The Godzilla backdoor, a creation of a Chinese threat actor known as “BeichenDream,” distinguishes itself through its fileless operation and use of Advanced Encryption Standard (AES) to cloak its network communications. This makes it particularly challenging to detect using conventional signature-based antivirus solutions or even some machine learning-based defenses.
The attack chain showcases a clever blend of techniques designed to bypass security measures and establish a persistent foothold within the target environment. It involves intricate object linking chains to bypass OGNL template restrictions, dynamic class loading to execute malicious code directly in memory, and the injection of a custom valve into the Tomcat pipeline to create a backdoor for ongoing access.
At the core of the Godzilla backdoor is the GodzillaValue class, which extends ValveBase, a custom Tomcat valve. This class is equipped with various methods for encryption, decryption, and base64 encoding, all designed to ensure the persistence and stealth of the malware. The class uses AES-128 encryption with a hardcoded key and password for its cryptographic operations, making it a formidable tool for attackers.
The GodzillaValue class waits for further instructions from the attackers, indicating that it is part of a broader strategy, possibly aimed at creating a botnet network. This assumption is supported by the presence of commands that can be executed remotely, provided they are encrypted with the correct key. The attackers have designed this backdoor to remain idle until it receives the next stage of the attack payload, highlighting the meticulous planning behind this campaign.
Successful exploitation of this vulnerability can have severe consequences for organizations. Attackers can gain complete control over the compromised Confluence server, potentially leading to data exfiltration, unauthorized access to sensitive information, and even further lateral movement within the network.
The widespread exploitation of CVE-2023-22527 underscores the urgent need for organizations to proactively address this vulnerability.
Related Posts:
- A Stealthy Godzilla Webshell: A New Threat Targeting Apache ActiveMQ
- Cryptojacking Campaign Exploits Atlassian Confluence CVE-2023-22527 Vulnerability
- CVE-2023-22527 (CVSS 10): Critical RCE Flaw in Confluence Data Center and Server
- Researchers Published Technical Details for Atlassian Confluence RCE (CVE-2023-22527)