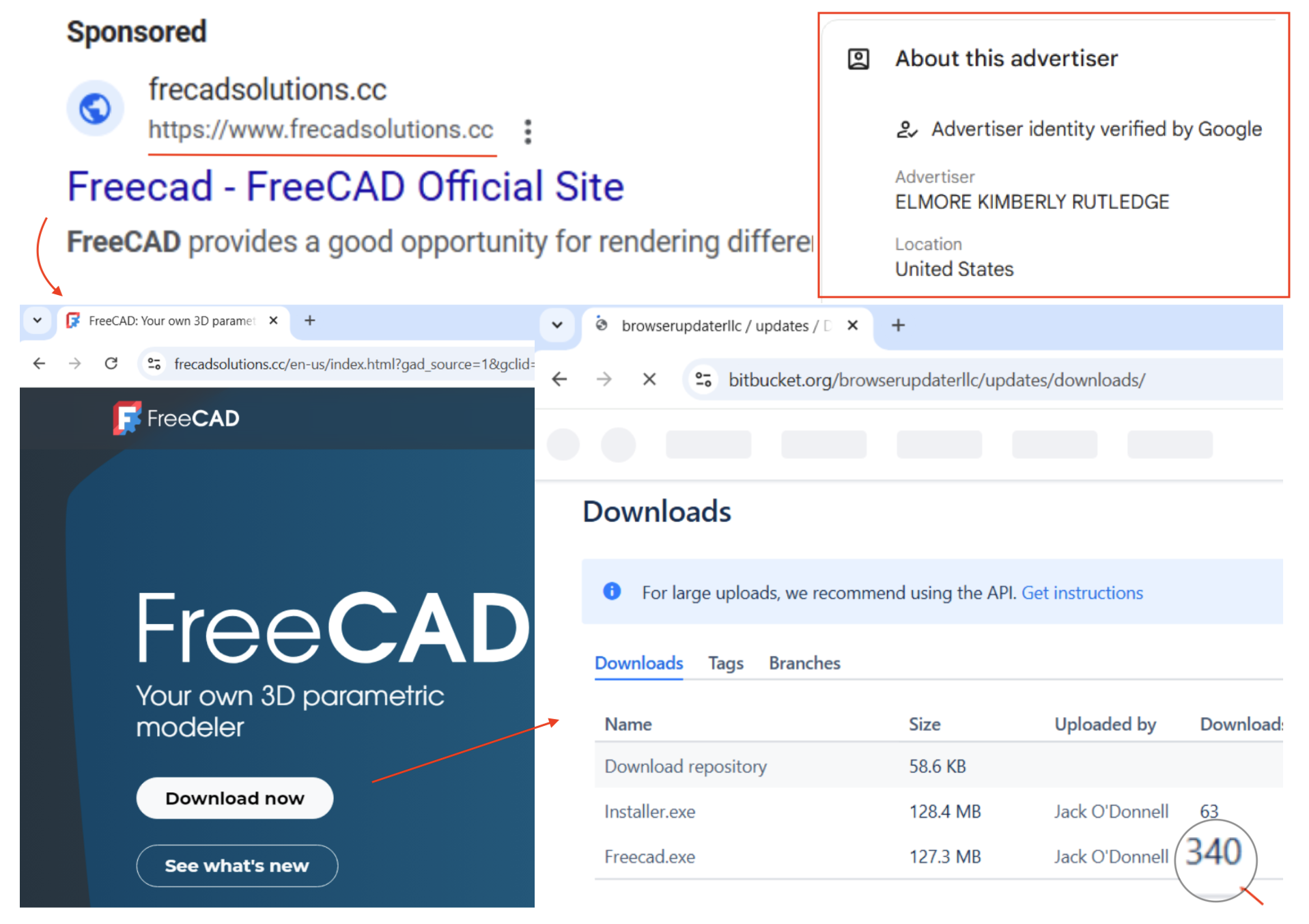
A malvertising campaign was launched using frecadsolutions[.]cc | Source: Silent Push
Silent Push Threat Analysts have revealed a widespread malvertising campaign exploiting Google Ads to target graphic design professionals. This ongoing operation, active since November, utilizes domains hosted on dedicated IP addresses to deliver malicious downloads disguised as legitimate tools for CAD and graphic design software.
Despite the simplicity of identifying and mitigating these threats, the attackers have operated with consistency. Silent Push notes: “Domains have been launched day after day, week after week, since at least November 13, 2024, for malvertising campaigns hosted on two dedicated IP addresses: 185.11.61[.]243 and 185.147.124[.]110.” These campaigns leverage fake domains that mimic legitimate services to trick unsuspecting victims into downloading malware.
The campaigns use Google Search advertising to promote malicious websites, which then redirect users to harmful downloads. For example:
- The first campaign launched on frecadsolutions[.]com, hosted on 185.11.61[.]243 since November 6, 2024.
- Other domains include variations like freecad-solutions[.]net, rhino3dsolutions[.]io, and planner5design[.]net, showcasing subtle changes in domain names to maintain credibility.
Silent Push highlights: “At least ten distinct malvertising campaigns, launched via Google ads, that make use of domains mapped to one of these two IP ranges.”
The analysis revealed a well-organized operation:
- Dedicated IPs: 185.11.61[.]243 and 185.147.124[.]110 host hundreds of domains tied to these campaigns.
- Malicious Tools: Victims are lured with links to download CAD tools or graphic design software, often leveraging legitimate platforms like Bitbucket to host malicious files.
Silent Push states: “Conducting a simple process to look up which IP address is hosting a domain and then investigating that IP address for other similar domains, however, is not a complex task. It’s a beginner pivot.” Yet, Google Ads has seemingly failed to employ such basic checks, allowing the campaign to continue.
The campaign underscores potential gaps in Google’s ad monitoring and threat mitigation processes.
Related Posts:
- Google Products Exploited in Sophisticated Malvertising Scheme
- Beware of Fake AI Photo Editors on Social Media: Malvertising Campaign Targets Credentials
- Evolving Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters
- Silent Skimmer Reemerges: New Tactics Target Payment Gateways