Cybersecurity researcher Brutecat has uncovered two security vulnerabilities in YouTube platform. Despite Google’s assurances regarding user privacy protection, an attacker could link these two vulnerabilities together to directly obtain the Gmail address associated with a YouTube channel’s creator.
Once the Gmail address is acquired, threat actors could impersonate Google or YouTube to launch phishing campaigns against content creators, leading to a cascade of security threats—including the hijacking of large YouTube accounts and the dissemination of phishing websites.
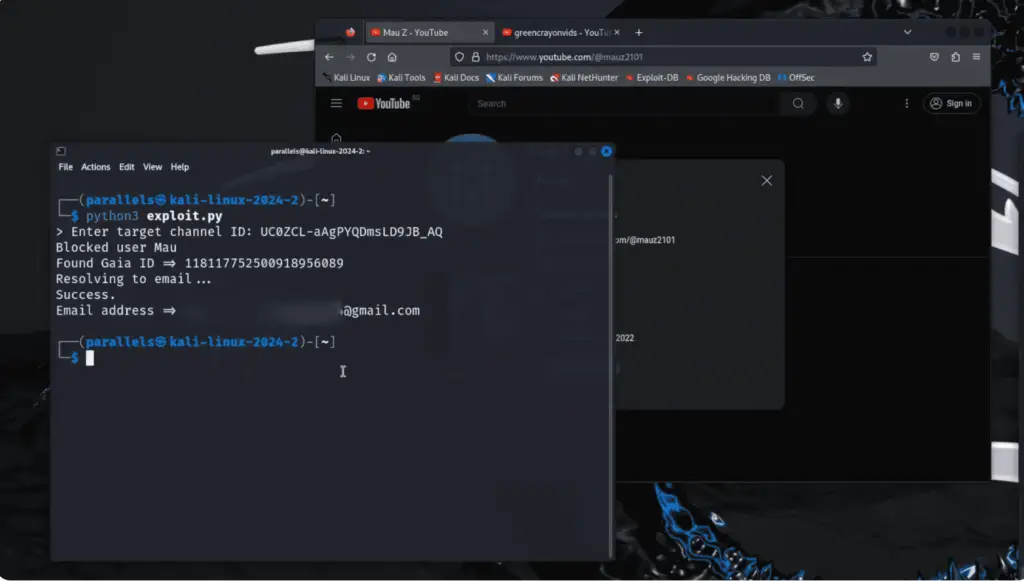
The initial discovery stemmed from an analysis of Google’s People API, where researchers identified a flaw in the user-blocking functionality on YouTube. This mechanism relies on an obscured Gaia ID, a unique identifier used by Google’s account management system across all its services. According to Google’s support documentation, when a user blocks another individual on YouTube, the restriction extends to other Google services as well. This means that the action is not merely blocking a YouTube account, but rather the underlying Gaia ID.
There have been several instances where vulnerabilities allowed the conversion of Gaia IDs into email addresses. Researchers speculated that similar flaws might still persist in Google’s older or lesser-known products.
Their hypothesis was soon validated. During their investigation, they discovered a linking mechanism in Google Pixel Recorder’s web version, a voice recording application pre-installed on Pixel devices. By sharing a Pixel Recorder audio file with a Gaia ID and examining the web requests, researchers found that the target’s email address was inadvertently exposed.
Ordinarily, such an action would trigger a sharing notification to the target user (e.g., an alert about the shared recording). However, the researchers devised a workaround by employing a Python script to generate an exceedingly long file name—approximately 2.5 million characters in length. This anomalously large filename caused Google’s system to fail to send the notification, allowing the email exposure to remain undetected.
Upon confirming the exploitability of the vulnerability, the researchers promptly reported it to Google, which later acknowledged the issue. Google initially awarded them a bug bounty of $3,133, but after a reassessment of the vulnerability’s potential impact, the severity rating was upgraded, leading to an additional reward of $7,500. In total, the researcher received $10,633 for their discovery.
Google has since patched the vulnerability, ensuring that such an exploit is no longer possible.
Related Posts:
- A Critical Security Flaw in Check Point Gaia Portal
- Beware of Instagram Influencer Scams: McAfee Labs Exposes New Threat
- Cryptocurrency Malware: The Hidden Threat Lurking on YouTube