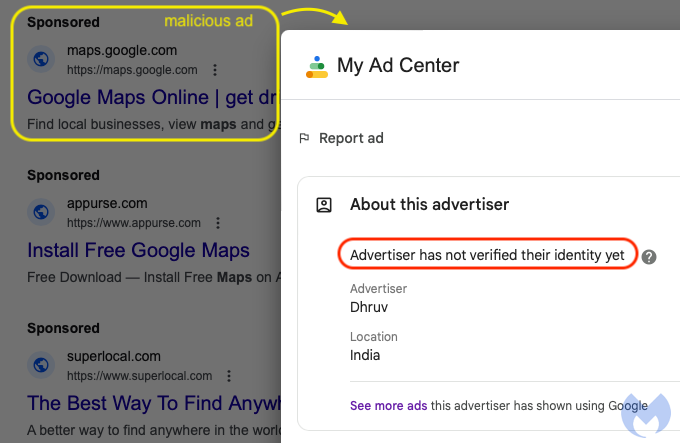
A malicious ad for Google maps from a yet to be verified advertiser account | Image: Malwarebytes Labs
Cybersecurity researchers at Malwarebytes Labs have uncovered a sophisticated malvertising campaign targeting Google users. The scammers have brazenly impersonated Google’s entire product line, using malicious search ads to redirect victims to a fake Google homepage.
The campaign first drew attention when malicious ads for Google Authenticator began circulating, directing unsuspecting users to fake download pages. However, the scammers have since escalated their efforts. The latest attacks involve creating ads that mimic Google’s entire suite of services, from Google Maps to Google Drive, all designed to lure users into visiting a fake Google homepage.
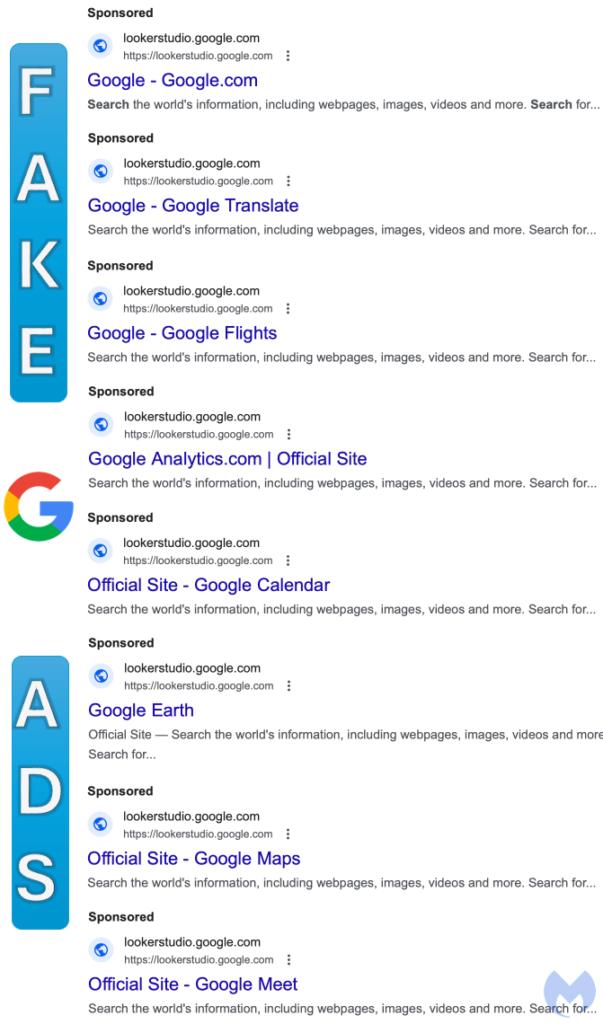
What makes this scheme particularly insidious is the use of Google’s own Looker Studio—a tool intended for creating data dashboards. The scammers abuse this platform to display a dynamically generated image that perfectly mimics the Google homepage. Upon landing on this fake page, users may believe they are still within the safety of Google’s ecosystem, only to have their browser locked by a malicious URL embedded within the image.
The scammers have ingeniously exploited Google’s dynamic keyword insertion feature, which allows advertisers to target specific keywords automatically. In this case, they targeted keywords associated with Google’s various products, ensuring that their fake ads would appear prominently in search results.
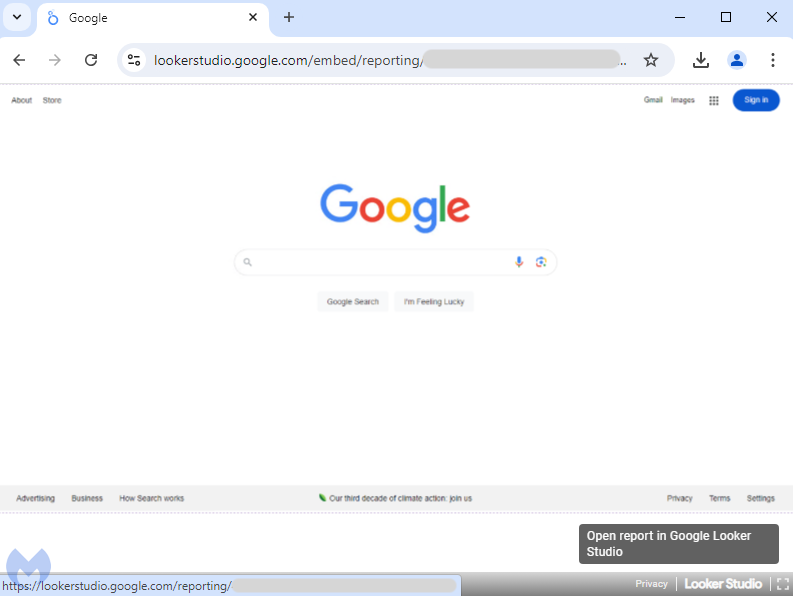
Once a user clicks on one of these ads, they are redirected to what appears to be a legitimate Google product page, with the display URL often showing lookerstudio.google.com—a real Google domain. However, the page is a facade. It’s actually a stretched image designed to look like Google’s search page. Hidden within this image is a hyperlink that, when clicked, opens a new tab with a tech support scam.
The final step in this elaborate scheme involves redirecting victims to a tech support scam page, typically hosted on Microsoft Azure. The page goes full-screen and plays an audio message warning users that their computer is infected. This is designed to induce panic, prompting victims to call a fake support number for assistance. Once connected, victims are persuaded to buy gift cards or provide access to their bank accounts to pay for “repairs.”
The use of Microsoft Azure’s web[.]core[.]windows[.]net domain adds another layer of complexity, as it’s commonly used by legitimate services, making it difficult for security teams to block the malicious URLs.
Malwarebytes Labs has reported these activities to Google, but the incident raises serious concerns about the security of online advertising platforms and the ease with which they can be exploited.
Related Posts:
- Beware of Fake AI Photo Editors on Social Media: Malvertising Campaign Targets Credentials
- Vulnerable Clicks: PikaBot Hijacks Businesses with Malvertising
- Massive Scam Surge: Google Ads Fueling Fraud
- Accidental Malvertising Strikes via Google Dynamic Search Ads