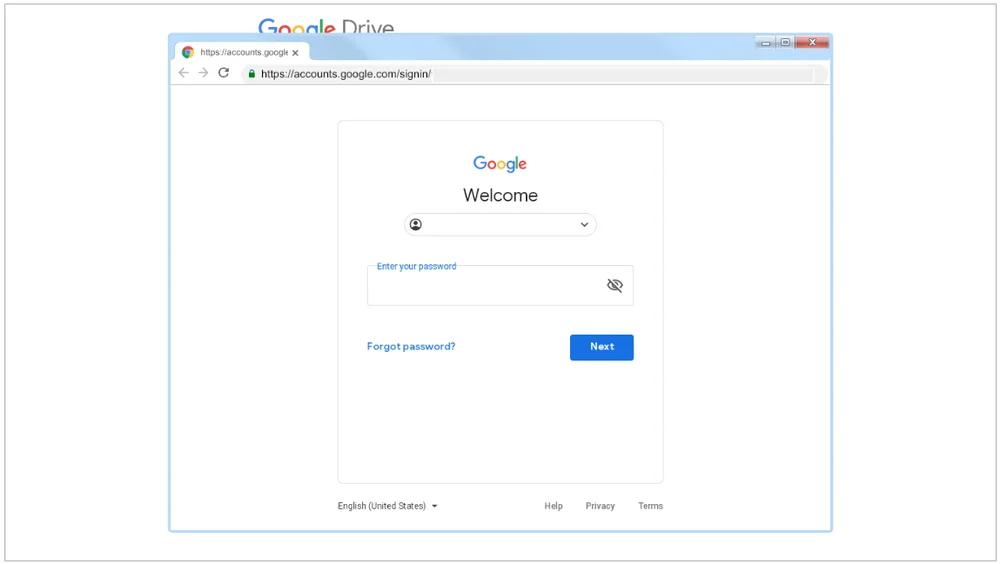
ARCHIPELAGO “browser-in-the-browser” phishing page
Google’s Threat Analysis Group (TAG) at Google has been tracking North Korean government-backed hacking activities for over a decade. In a follow-up to Mandiant’s report on APT43, TAG shares its observations on this actor, known as ARCHIPELAGO, and highlights the measures taken by Google to protect users from this group and other state-sponsored attackers.
Since 2012, TAG has been tracking ARCHIPELAGO, a group known for targeting individuals with expertise in North Korea policy issues, such as sanctions, human rights, and non-proliferation. Their targets include government and military personnel, think tanks, policymakers, academics, and researchers in South Korea, the US, and beyond. To protect users, TAG continuously improves Google’s products based on its research on threat actors like ARCHIPELAGO.

ARCHIPELAGO is known for its persistent and targeted phishing campaigns. They often pose as media outlets or think tanks, inviting North Korea experts to participate in interviews or information requests. The phishing emails contain malicious links, which when clicked, lead to phishing sites that record keystrokes and credentials. ARCHIPELAGO also invests time in building rapport with targets, sometimes corresponding with them for weeks before sending a malicious link or file.
Over the years, ARCHIPELAGO has shifted its phishing tactics. They previously used typical phishing messages posing as Google Account security alerts but have evolved to use more sophisticated methods. Recent campaigns have involved sending benign PDF files hosted on OneDrive, which contain phishing links. These tactics are likely aimed at evading detection by antivirus services.
While ARCHIPELAGO initially focused on traditional credential phishing, they have increasingly incorporated malware into their operations. They often password-protect their malware and share the password with recipients in phishing emails to evade antivirus scanning. They have also experimented with novel malware delivery techniques, such as encoding malicious payloads in file names hosted on Google Drive.
ARCHIPELAGO has used malicious Chrome extensions in combination with phishing and malware campaigns. Early versions of these extensions, such as STOLEN PENCIL, were designed to steal usernames, passwords, and browser cookies. More recently, ARCHIPELAGO has attempted to install a new malicious Chrome extension known as SHARPEXT, which can parse emails from active Gmail or AOL Mail tabs and exfiltrate them to attacker-controlled systems.
The activities of ARCHIPELAGO, a North Korea-linked cyber espionage group, underscore the importance of staying vigilant in the face of state-sponsored cyber threats. By understanding the tactics and techniques used by such actors, organizations can implement more effective security measures and protect their users and systems from cyberattacks.