gotestwaf v0.4.8 releases: test different web application firewalls (WAF) for detection logic and bypasses
Go Test WAF
GoTestWAF is a tool for API and OWASP attack simulation, that supports a wide range of API protocols including REST, GraphQL, gRPC, WebSockets, SOAP, XMLRPC, and others.
It was designed to evaluate web application security solutions, such as API security proxies, Web Application Firewalls, IPS, API gateways, and others.
How it works
It is a 3-steps requests generation process that multiplies the amount of payloads to encoders and placeholders. Let’s say you defined 2 payloads, 3 encoders (Base64, JSON, and URLencode), and 1 placeholder (HTTP GET variable). In this case, the tool will send 2x3x1 = 6 requests in a testcase.
Payload
The payload string you wanna send. Like <script>alert(111)</script> or something more sophisticated. There are no macroses like so far, but it’s in our TODO list. Since it’s a YAML string, use binary encoding if you wanna https://yaml.org/type/binary.html
Encoder
Data encoder the tool should apply to the payload. Base64, JSON Unicode (\u0027 instead of ‘), etc.
Placeholder
A place inside HTTP request where encoded payload should be. Like URL parameter, URI, POST form parameter, or JSON POST body.
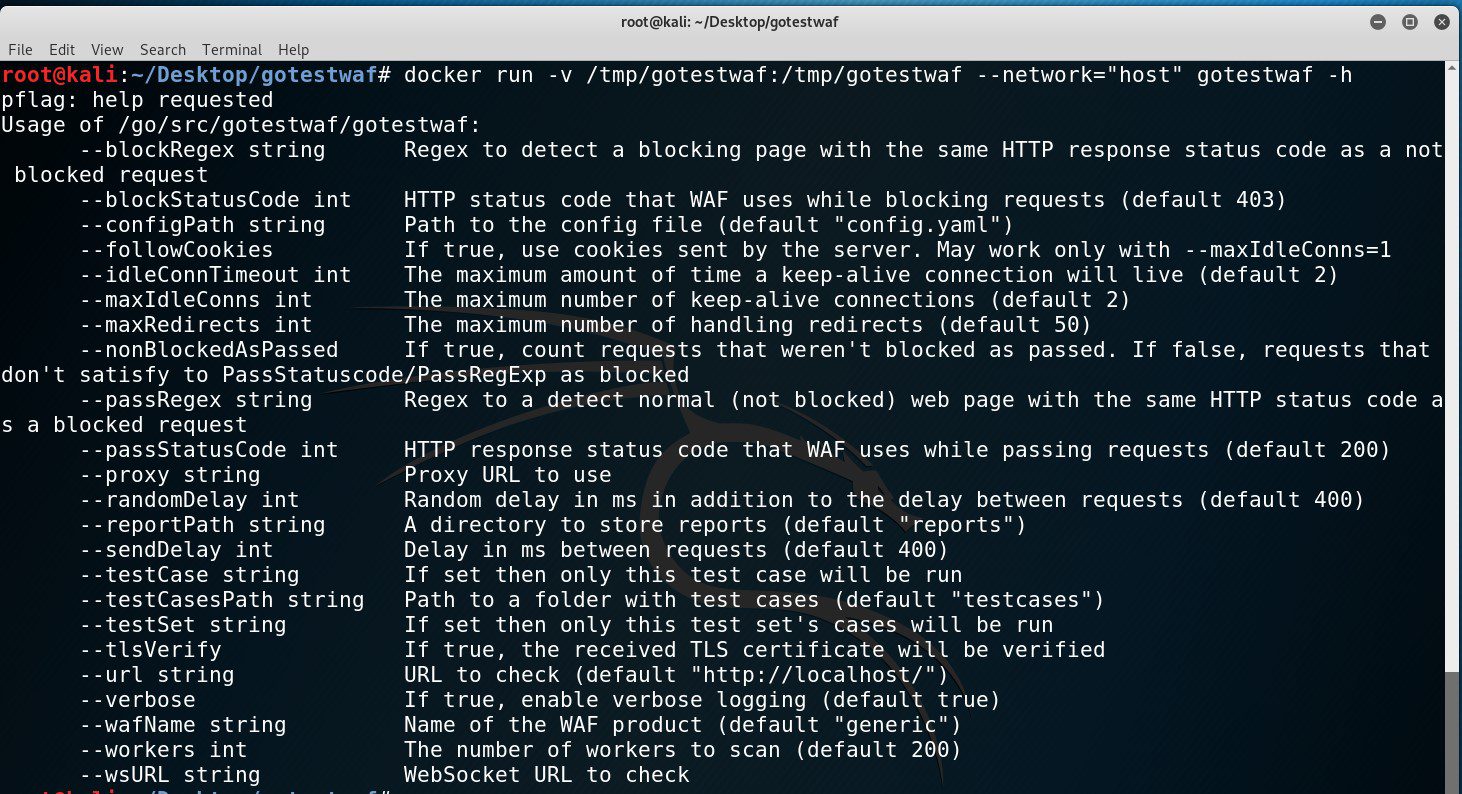
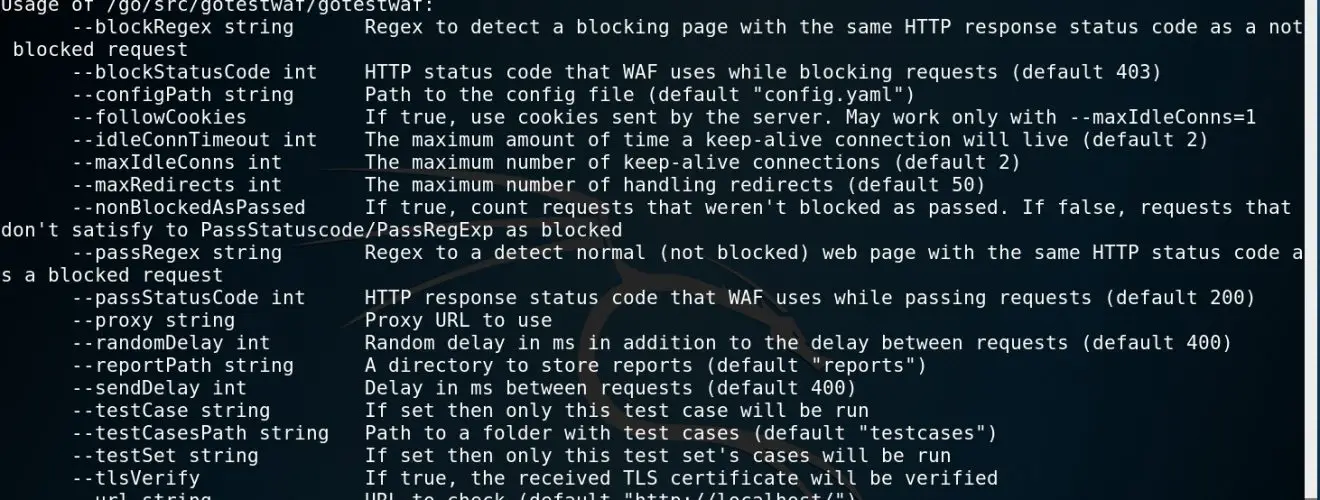
Install & Use
Copyright (c) 2020 Wallarm