Grafiki
Grafiki is a Django project about Sysmon and graphs, for the time being.
In my opinion EventViewer, Elastic, and even Kibana, are not graphic enough. The current threats are complicated and if attackers think in graphs, defenders also must do it.
This is a proof of concept, the code was not debugged jet but maybe could be useful for someone, I will improve it.
This project started such as EVTX parser to SQL database and this maybe it is the core of the project.
Goals
- Parse Sysmon events from EVTX files and from URL to relational database.
- Parse Elastic Sysmon events to a relational database.
- Easy Elastic filters creation.
- Create graphs from the database using Vis.js.
- Offer filters to easy work with graphs.
- Show events sequentially.
- More
Information
This application can process two types of files.
- Sysmon EVTX files from disk or from a URL.
- Sysmon Filebeat event files from disk or from URL. Also, this application has two types of processing:
- Normal process
- Simple process In a normal process, each process generates one node in graph view, threats are represented in the graph, and also it is represented as a computer node with all its related processes.
In a simple process, processes are grouped by name, and threats are not represented in event 8 for example.
It’s important to keep this in mind because even a simple view sometimes could be useful, other times could be confusing, for example when you have events from more than one computer.
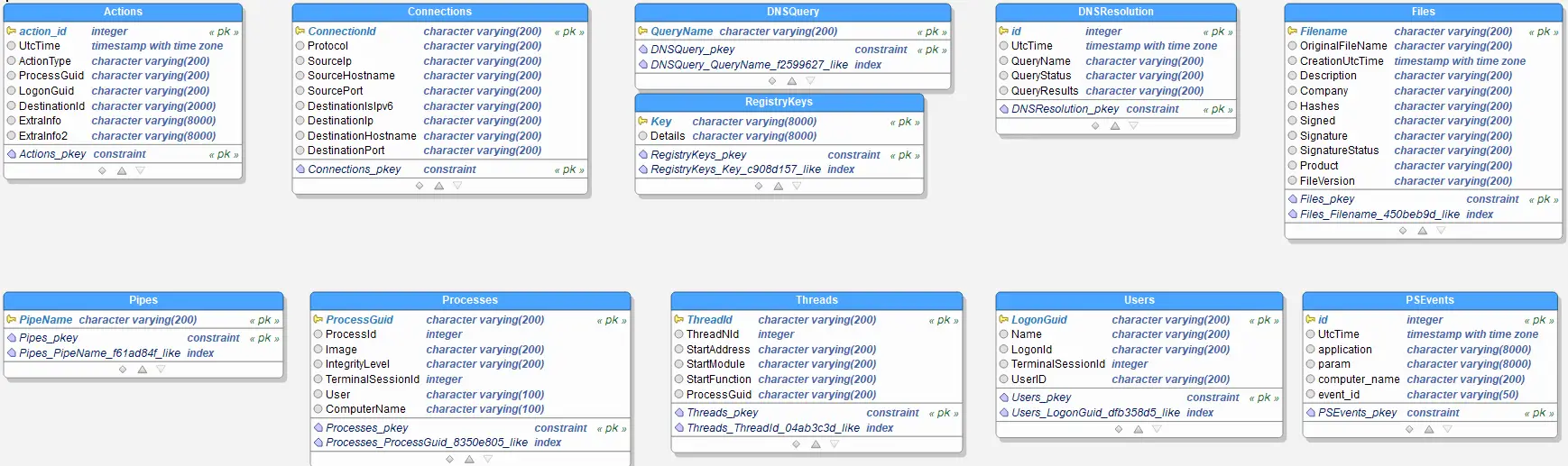
Data schema
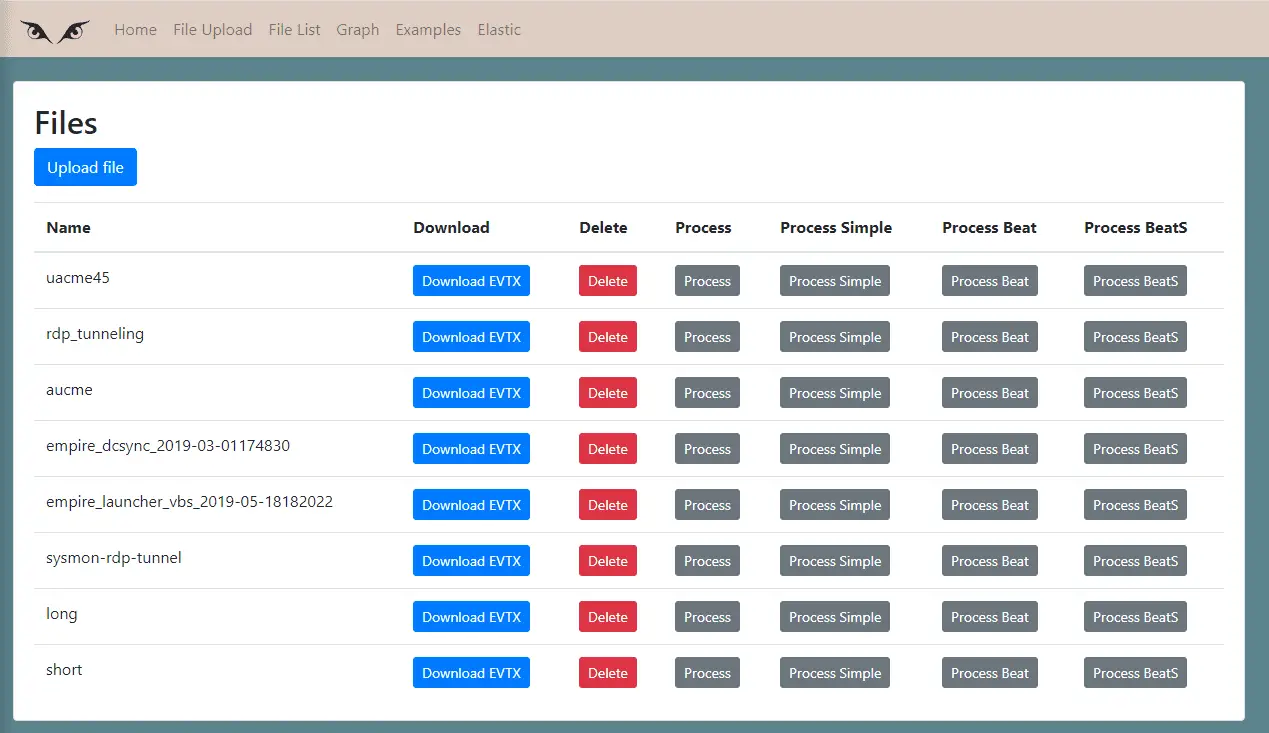
File List
On this page, you can upload evtx files or elastic event files and process them.
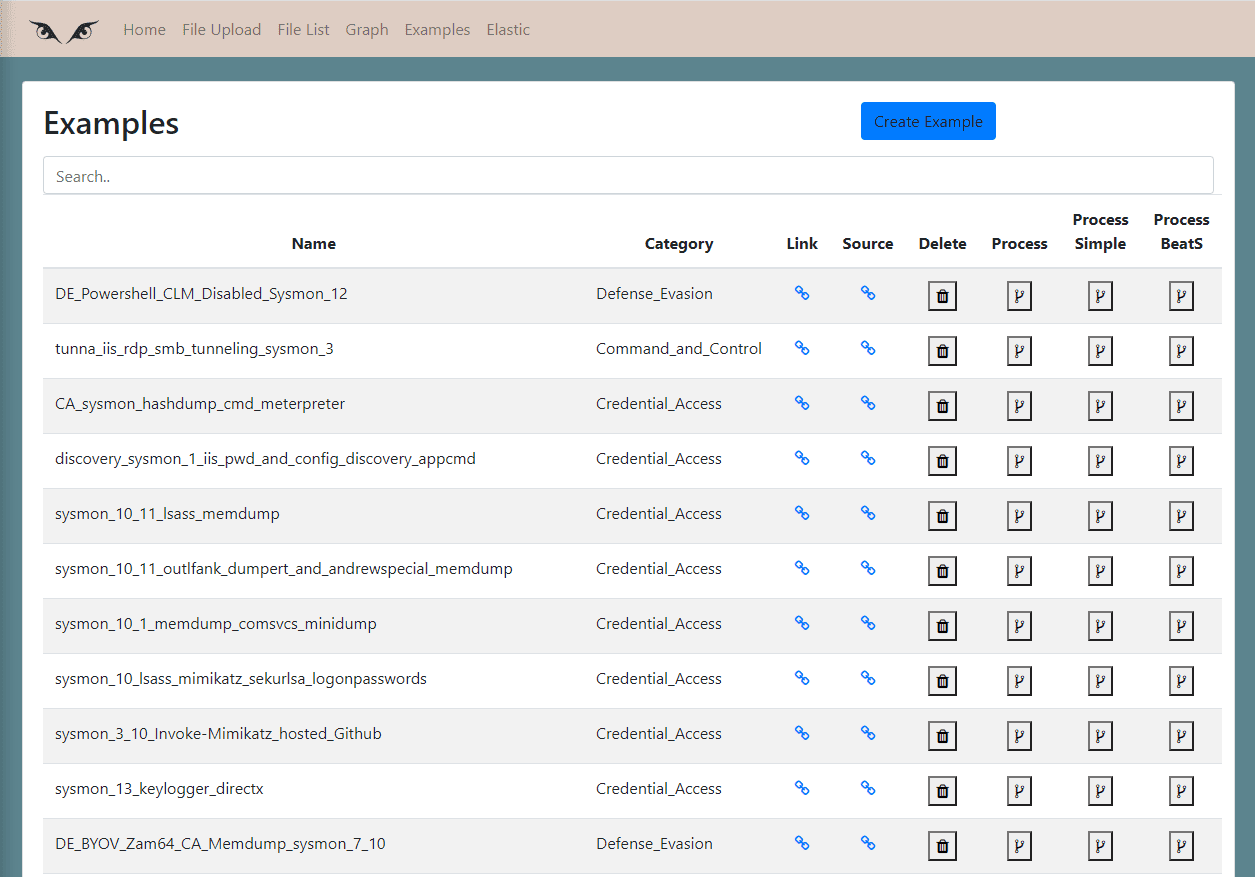
Examples
This page is useful for creating a library of online samples files.
When you create an example, you put the url to the file, and when you process it, the application downloads the event file and processes it.
Elastic
On this page, you can create searches to your Elastic instance and create a graph of the result. You can create filters about:
- The hostname of the host machine.
- Sysmon event ID
- SourceIP
- DestinationIP
- DestinationIP Type (Internal or External)
- UserAccount
- Process Name All these filters can be inclusive or exclusive and can contain a group of values separated by commas.
You can create more than one filter and all of the created filters uses “AND” as a logical operator between each other.
On this page, you can include Powershell Scripting Logging events in the results.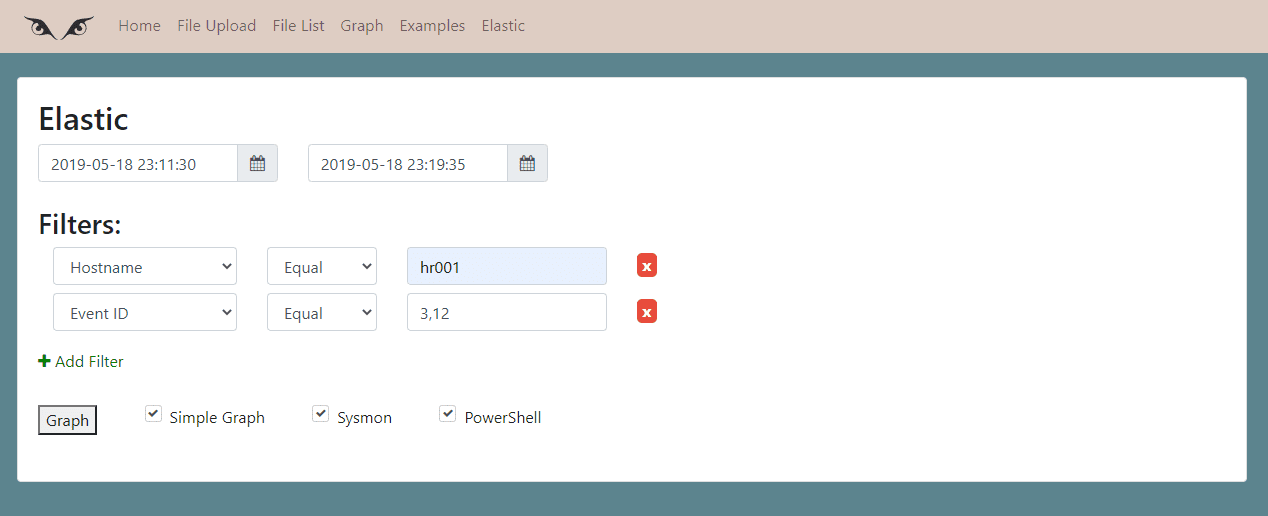
Graph
The graph page is the core of this application and its research interface of it.
On the other pages, you select your data and these pages send you to the graph page, if you go directly to the graph page, nothing will be there or the last data searched for you.
On this page are two tabs, one for sysmon and the other for Powershell events.
There are two types of elements, nodes, and edges. Nodes represent entities such as process, file, or registry key and edges represent actions such as create, delete or connect.

Sysmon
We are at the core.
This part uses the information in the database to create graphs about the events analyzed.
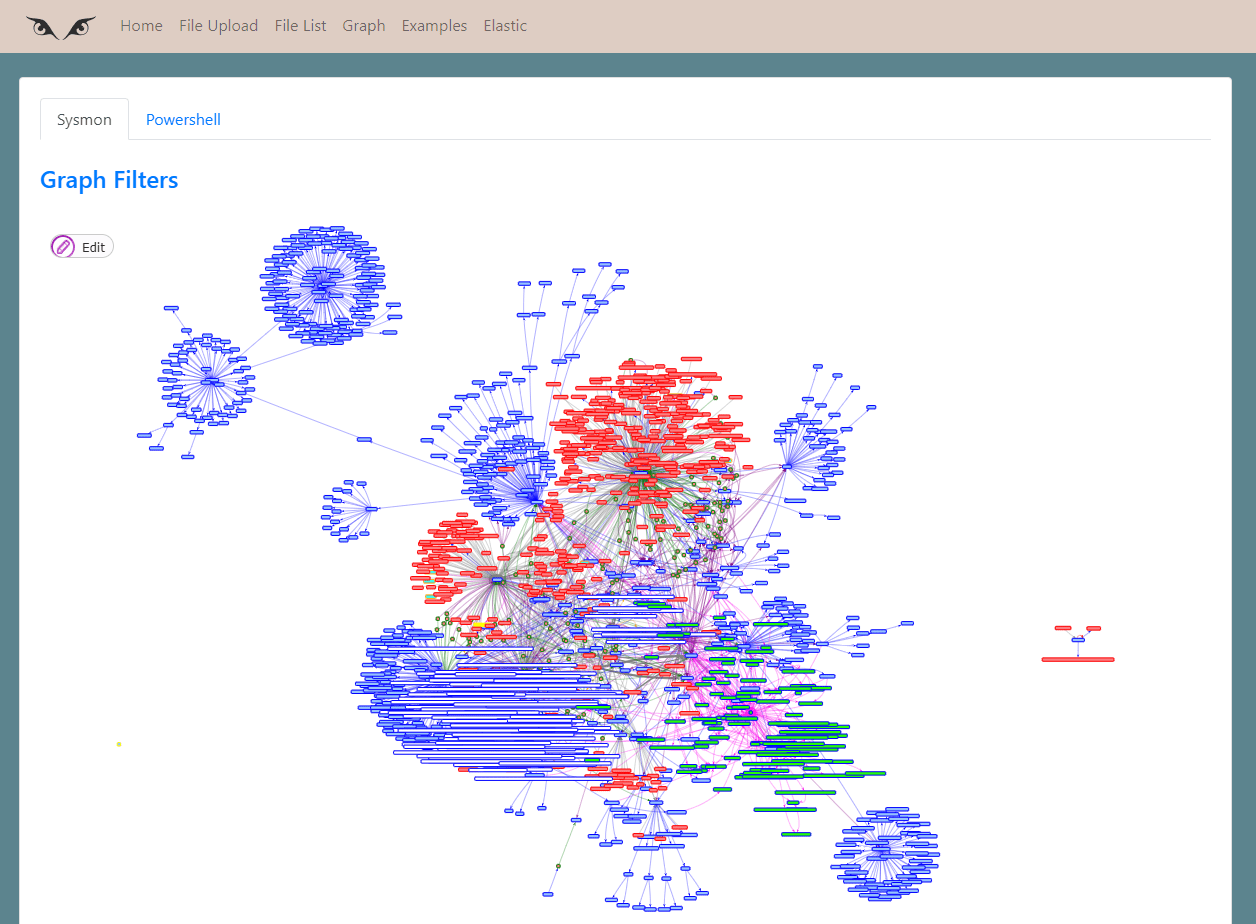
You can navigate in the graph, watching about process creation, named pipes connected … but there is usually too much information to work comfortably.
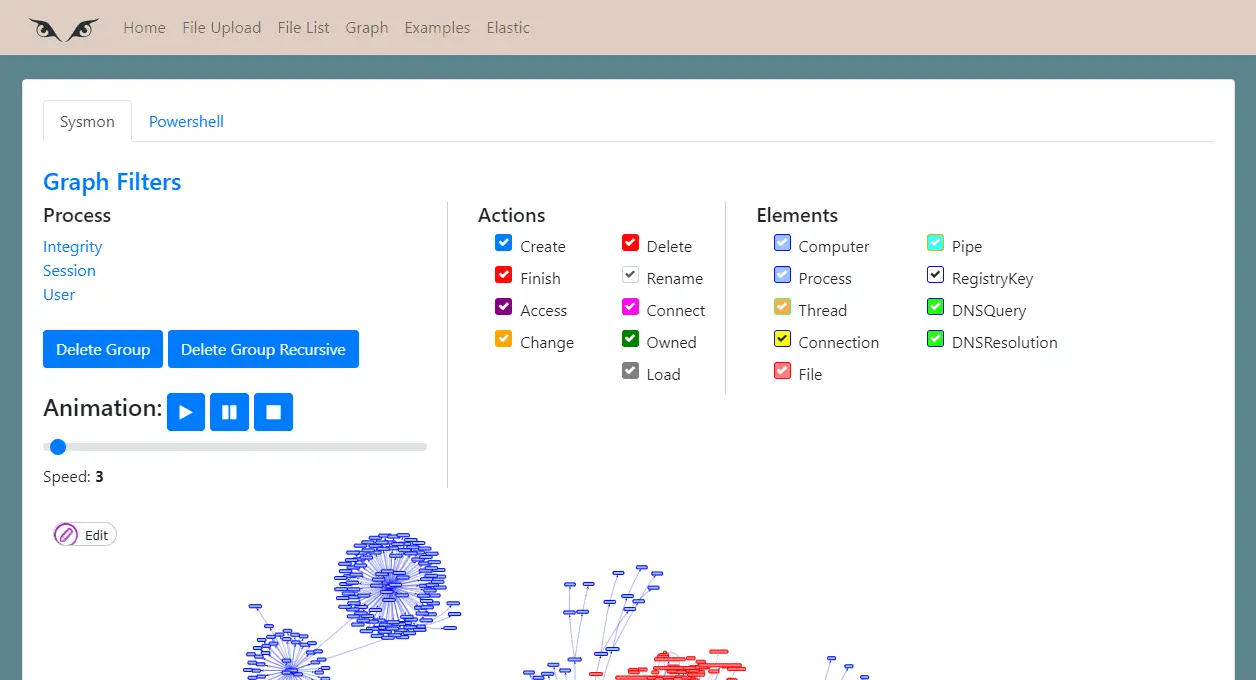
Inside the tab are a hidden section about graph filters.
Filters
 In this area, you can work with graph filtering data.
In this area, you can work with graph filtering data.
You can filter nodes by these entities:
- Computer
- Process
- Threat
- Connection (IP)
- File
- Pipe
- Registry Key
- DNS Query
- DNS Resolution
You can filter process nodes also by:
- Process integrity
- Process session
- User
Also, you can filter edges by these actions:
- Create
- Finish
- Access
- Change
- Delete
- Rename
- Connect
- Owned (belongs to)
- Load
Animations
One great feature is creating animations about the data in the graph, this is very useful for example in Parent PID Spoofing or when some user in a computer executes commands remotely.

Delete groups
When a graph has too much information, is possible to delete one node, one edge, a group of nodes, or a group of nodes recursively.
Delete group of notes works by selecting one node and the application will delete all de nodes that parent is the selected node.
Delete group recursively works also selecting a node but the application will go through nodes deleting until finish this tree branch. If the branch has a lot of information, this will take a long time.
Graph Settings
At the bottom of the screen, it’s possible to change the physics of the graph.
When a graph has a lot of information could be useful to disable physics in order to stabilize the graph.
You can play whit physics, it’s funny.
Powershell logging
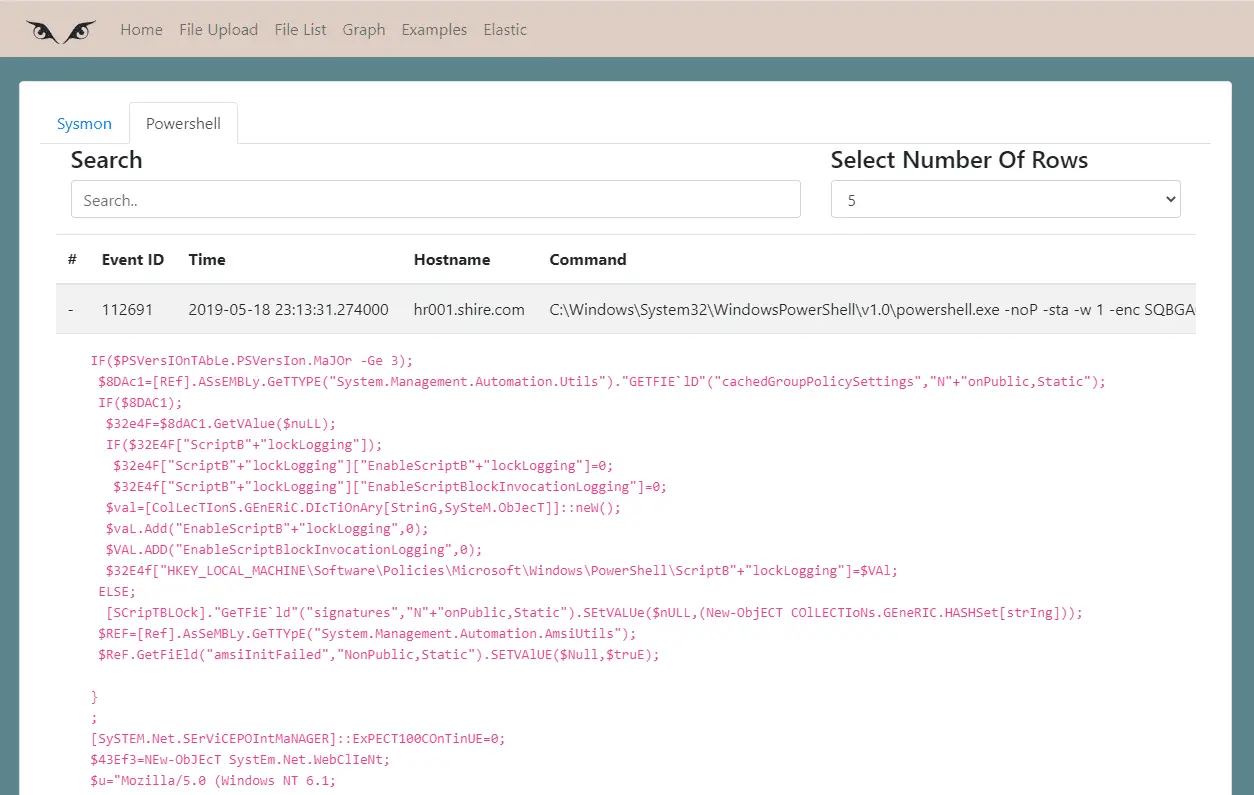
In Powershell, the tab is possible to analyze powershell commands.
Commands are shown in an accordion and inside each row, if the command contains a base64 command, it will be decoded and parsed.
You can search in all events for encoded o decoded parts of the command.
Install
git clone https://github.com/lucky-luk3/Grafiki.git
cd Grafiki
chmod +x setup.sh
sudo ./setup.sh
— wait —
cd grafiki
python3 manage.py runserverIn your browser go to http://127.0.0.1:8000/
Copyright (C) 2022 lucky-luk3