GWTMap: map the attack surface of Google Web Toolkit based applications
GWTMap
GWTMap is a tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to facilitate the extraction of any service method endpoints buried within a modern GWT application’s obfuscated client-side code and attempt to generate example GWT-RPC requests payloads to interact with them.
More information can be found here.
Install
git clone https://github.com/FSecureLABS/GWTMap.git
cd GWTMap
pip3 install -r requirements.txt
Use
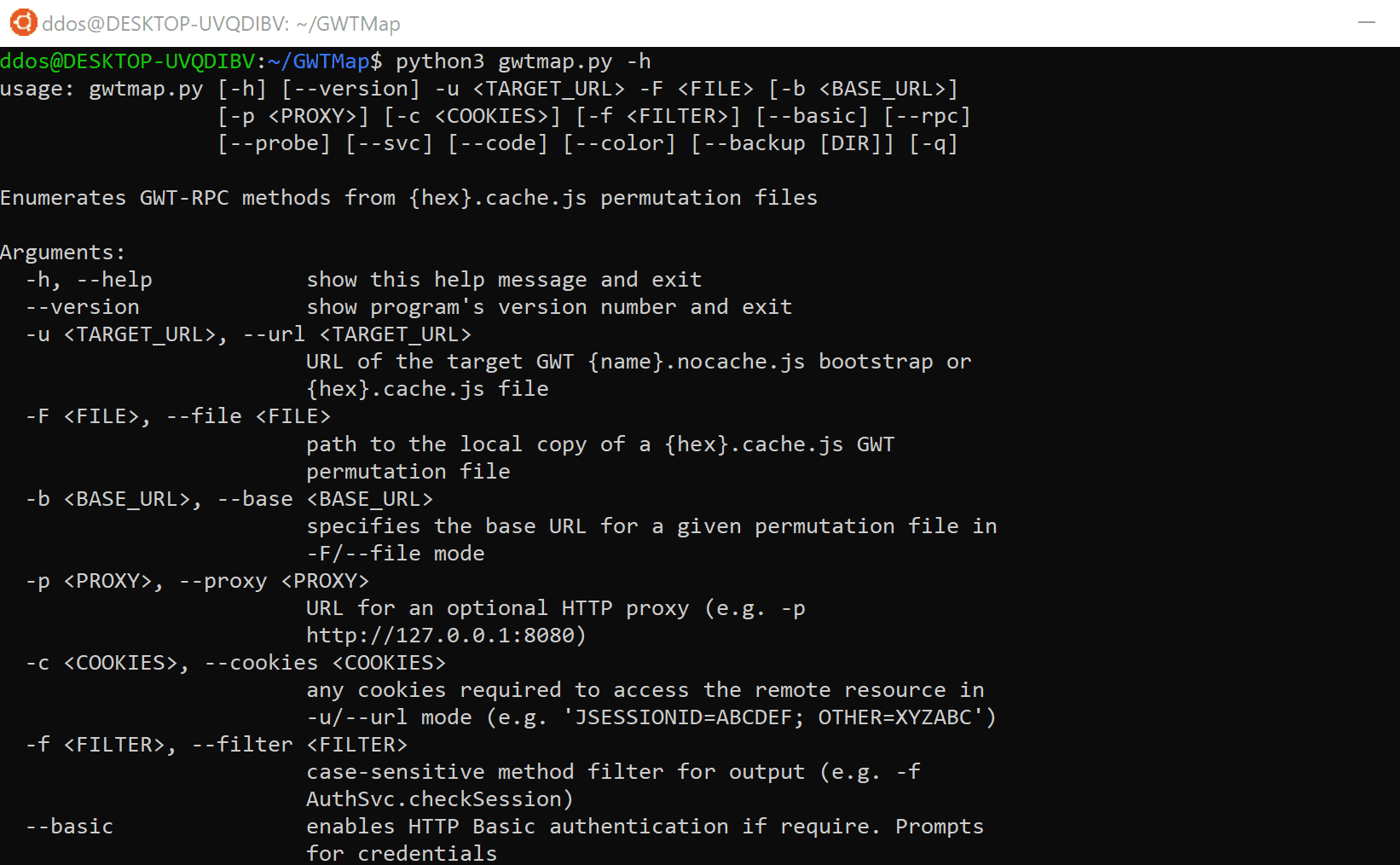
Usage
Enumerate the methods of a remote application via its bootstrap file and create a local backup of the code (selects permutation at random):
./gwtmap.py -u http://192.168.22.120/olympian/olympian.nocache.js --backup
Enumerate the methods of a remote application via a specific code permutation
./gwtmap.py -u http://192.168.22.120/olympian/C39AB19B83398A76A21E0CD04EC9B14C.cache.js
Enumerate the methods whilst routing traffic through an HTTP proxy:
./gwtmap.py -u http://192.168.22.120/olympian/olympian.nocache.js --backup -p http://127.0.0.1:8080
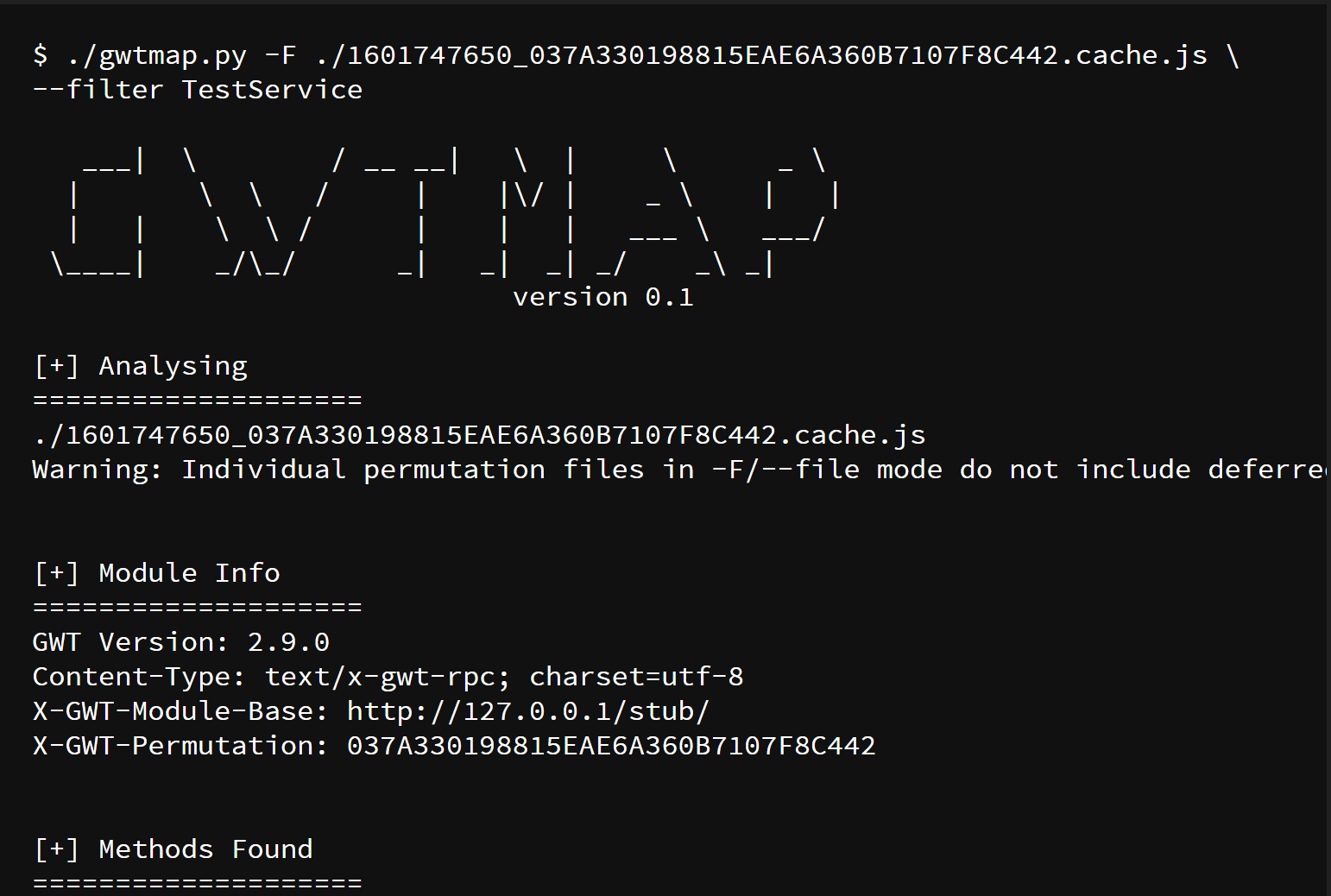
Enumerate the methods of a local copy (a file) of any given permutation:
./gwtmap.py -F test_data/olympian/C39AB19B83398A76A21E0CD04EC9B14C.cache.js
Filter output to a specific service or method:
./gwtmap.py -u http://192.168.22.120/olympian/olympian.nocache.js --filter AuthenticationService.login
Generate RPC payloads for all methods of the filtered service, with colored output
Automatically test (probe) the generate RPC request for the filtered service method
Copyright (c) 2020, F-Secure
Source: https://github.com/FSecureLABS/