HaboMalHunter: Habo Malware Analysis System
HaboMalHunter is a sub-project of Habo Malware Analysis System (https://habo.qq.com), which can be used for automated malware analysis and security assessment on the Linux system. The tool helps security analyst extracting the static and dynamic features from malware effectively and efficiently. The generated report provides significant information about process, file I/O, network and system calls.
Features
The tool can be used for the static and dynamic analysis of ELF files on the Linux x86/x64 platform.
Static analysis
- Basic Information: md5, name, file type, size, and SSDEEP.
- SO Files Dependency: SO files information (only applied to dynamically linked files).
- Strings Information.
- ELF Header and Entry Point.
- IP and PORTS
- ELF Segment, Section, and Hash.
- Source File Names.
Dynamic analysis
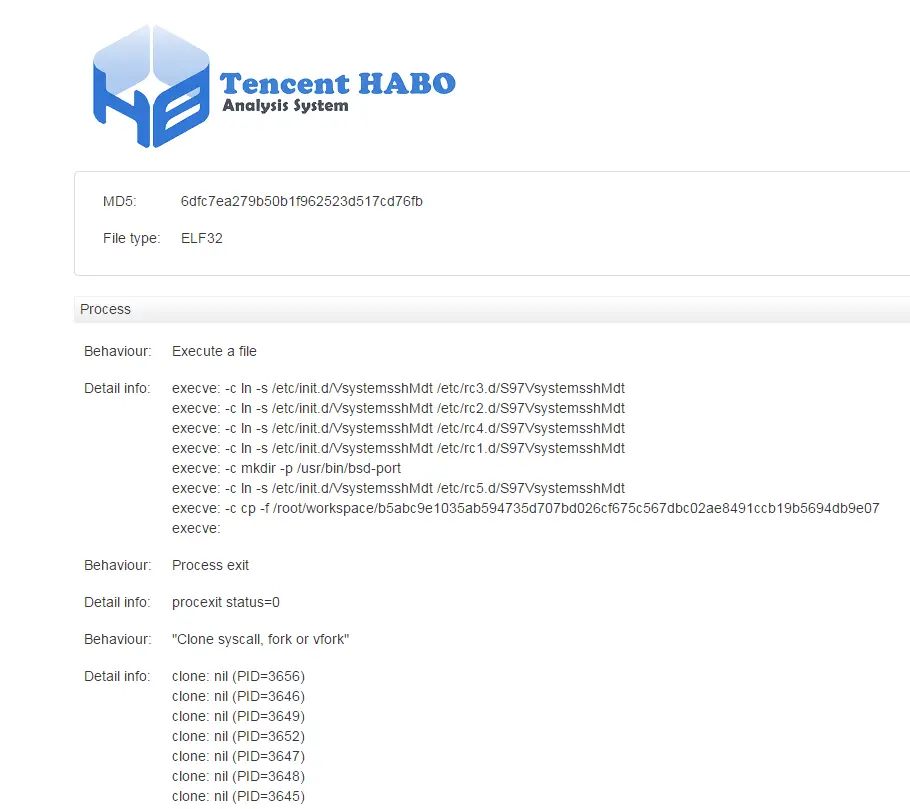
- Starting and Termination: Time Stamps and Elapsed Time.
- Processes Information: clone, execve and exit etc.
- File I/O: open, read, write and delete etc.
- Network: TCP, UDP, HTTP, and HTTPS etc.
- Typical Malicious Actions: self-deletion, modification, and lock.
- API Information: getpid, system, dup and other libc functions.
- syscall sequences.
Demo
1.Setup Environment
The tool will run on the VirtualBox 5.1 with Ubuntu 14.04 LTS.
in order to install third-party software, please execute the following command after obtaining the code:
root# cd ./util/update_image
root# bash update_image.sh
2.Get Source Code
git clone https://github.com/Tencent/HaboMalHunter.git
3.Compile
Firstly, please upload the source code to the VM. Execute the following command with root permission under the /root directory.
cp -ra /media/sf_Source/* .
The command will compile and package the source code, and then will generate two zip files.
bash package.sh
4.Analysis
using ./test/bin/read.32.elf to make a test. The second command will copy report and log outside the VM.
python AnalyzeControl.py -v -l ./test/bin/read.32.elf
cp ./log/output.zip /media/sf_Source/
Among the result, output.static is static analysis result, output.dynamic is dynamic analysis result, and system.log is runtime log. Users can also upload samples to the Habo Malware Analysis System (https://habo.qq.com) to get a brief report.
Copyright (C) 2017 THL A29 Limited, a Tencent company. All rights reserved.
Source: https://github.com/Tencent/










