Image: wallarm
Recently, the Wallarm Detect team discovered two vulnerabilities in VMware NSX Manager that allowed pre-authenticated attackers to execute code remotely. These vulnerabilities, CVE-2022-31678 and CVE-2021-39144, are still being actively exploited by attackers.
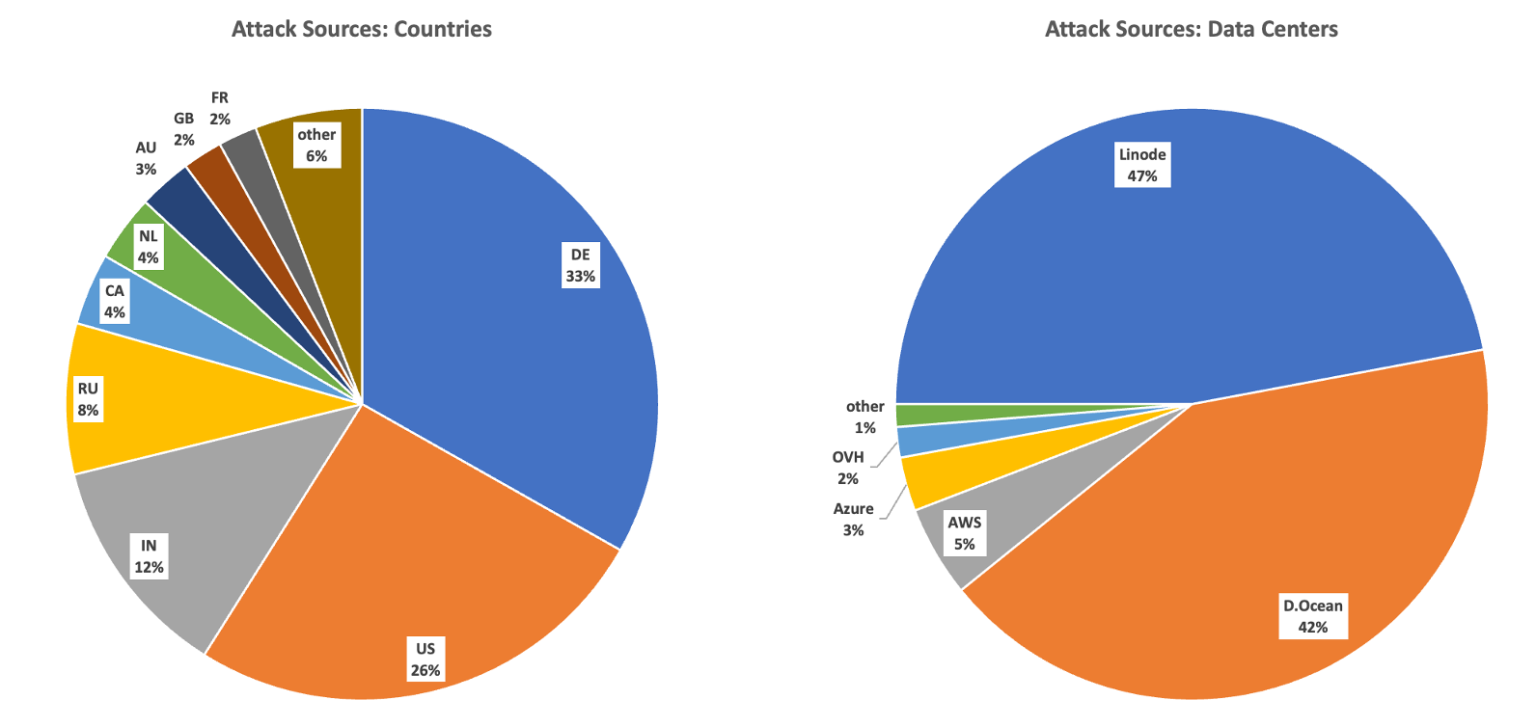
CVE-2022-31678 vulnerability exposes software to XXE attacks, while CVE-2021-39144 impacts the 3rd party library XStream. When combined, these vulnerabilities can lead to high-impact attacks. The Wallarm Detect team observed over 40 thousand attempts to exploit these vulnerabilities over the last 2 months, with over 90% of the attacks coming from well-known data centers like Linode and Digital Ocean.

The CVE-2022-31678 vulnerability allows a remote attacker to obtain sensitive information, caused by improper handling of XML external entity declarations. By sending specially-crafted XML content, a remote attacker could exploit this vulnerability to obtain sensitive information or cause a denial of service condition.
The CVE-2021-39144 vulnerability, on the other hand, allows a remote authenticated attacker to execute arbitrary commands on the system, caused by an unsafe deserialization flaw. By manipulating the processed input stream, an attacker could exploit this vulnerability to execute arbitrary commands on the system.
The impact of these vulnerabilities, if successfully exploited, could be catastrophic. Attackers could execute arbitrary code, steal data, and take control of the network infrastructure. This is a serious threat that could compromise the security and privacy of sensitive information.
The Wallarm Detect team saw the peak in scanning attempts occur in late December when Wallarm was blocking an average of almost 1,750 per day and a maximum of over 4,600 attacks per day. The current rate is about 500 attempts per day, which means that these vulnerabilities are still a threat.
It’s essential to take action to protect your system from these vulnerabilities. VMware has released patches to address these vulnerabilities, and users are advised to apply them as soon as possible. The Wallarm Detect team recommends using a web application firewall to protect your system against these types of attacks.