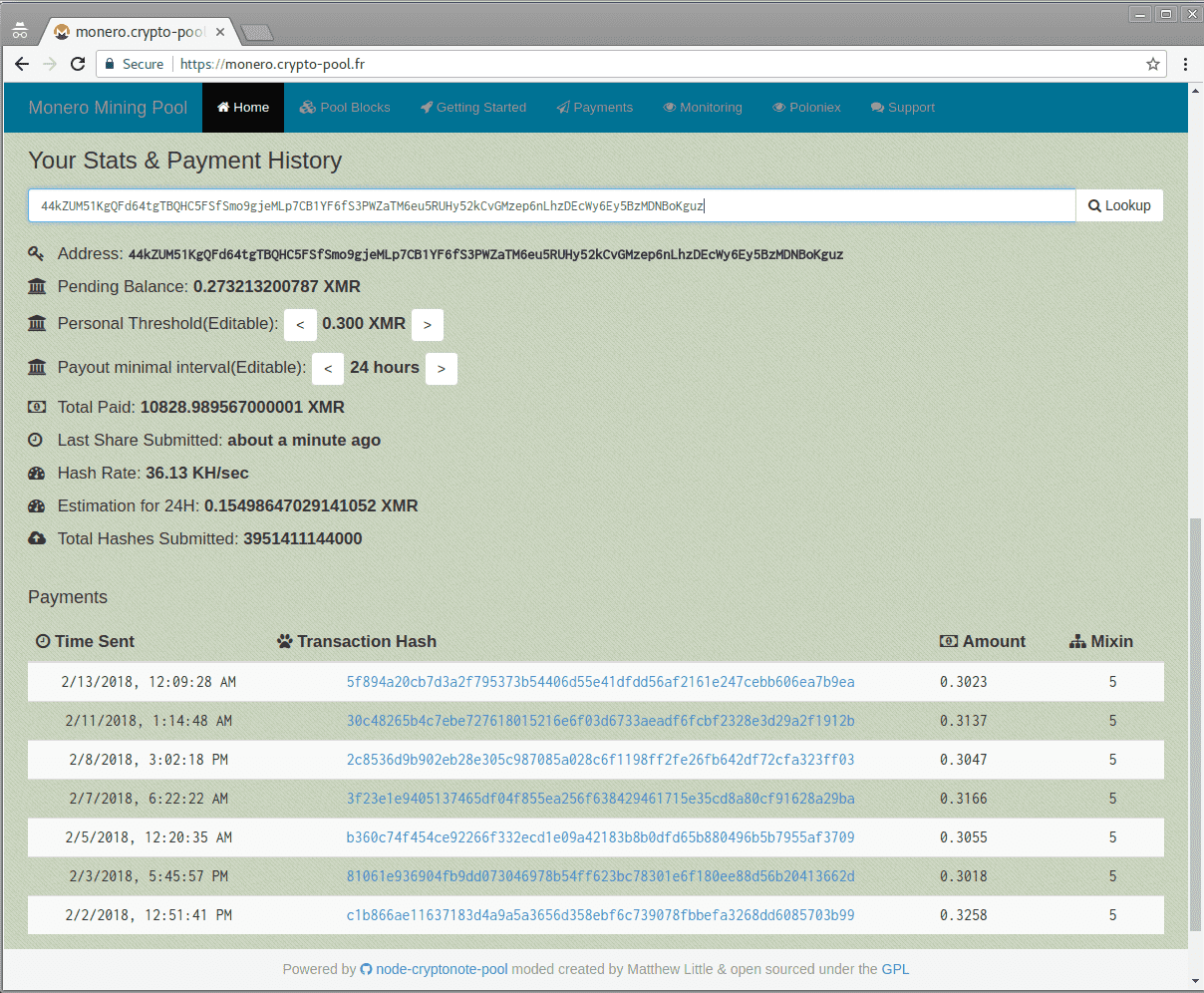
Recently, researchers from checkpoint discovered one of the biggest mining, Jenkins Miner. Attackers use software integration platform Jenkins remote code execution vulnerability (CVE-2017-1000353) to install Monero mining malware and make $3 million by mining Monero.
Check Point said:
“The operation uses a hybridization of a Remote Access Trojan (RAT) and XMRig miner over the past months to target victims around the globe. The miner is capable of running on many platforms and Windows versions, and it seems like most of the victims so far are personal computers. With every campaign, the malware has gone through several updates and the mining pool used to transfer the profits is also changed.”
Over the past 18 months, the hackers have accumulated 10,800 Monero, which is currently worth $3,436,776.

Jenkins remote code execution vulnerability (CVE-2017-1000353) was published in April 2017. “Jenkins versions 2.56 and earlier, as well as 2.46.1 LTS and earlier, are vulnerable to an unauthenticated remote code execution. An unauthenticated remote code execution vulnerability allowed attackers to transfer a serialized Java `SignedObject` object to the Jenkins CLI, that would be deserialized using a new `ObjectInputStream`, bypassing the existing blacklist-based protection mechanism. We’re fixing this issue by adding `SignedObject` to the blacklist. ”
According to CheckPoint, the JenkinsMiner attack involves sending two “subsequent requests to the CLI interface” so the “crypto-miner operator exploits the known CVE-2017-1000353 vulnerability in the Jenkins Java deserialization implementation. The vulnerability is due to lack of validation of the serialized object, which allows any serialized object to be accepted.”
JenkinsMiner mining malware download IP from China, linked to the organization as “Huaian e-government information center.” Despite the existence of multiple mining pools, the attack uses only one wallet. Check Point explained:
“Although the attack is well operated and maintained, and many mining-pools are used to collect the profits out of the infected machines, it seems that the operator uses only one wallet for all deposits and does not change it from one campaign to the next. So far, $3 million has been mined.”
IoC
Domain and IP:
- 222[.]184[.]79[.]11
- 183[.]136[.]202[.]244
- btc[.]poolbt[.]com
- shell[.]poolbt[.]com
- xmr[.]btgirl[.]com[.]cn
- btc[.]btgirl[.]com[.]cn
File:
- 0bb4503cc52530ddadb102fa4010fb4d89af88aca846d4b16f601d0702134246
- 06f8eda46fd6bdc11b8ec4d18a0f0afbf3d47f82cea8363d342975896582a715
- f0430130a2f3549b1aeff0a9fb2246f68f585a7c1d312c7be385a1cf5f37e70d
- c87d294cb0384cb56f4829d58cdd3f53572d3f95c2133a9b1da5f5bc1710f22f
- f750d6da918a5f2f2c442a339821ffebcad4b61e4ca1684bac0e7df98416a794
- 3002551eebaf486d77a2b81d87db553ad8632bb132553e306395c5da589171fe
- 213a23219ff89c412f92aa1fdf7152178a81514014ee1cc4ffee97e725ee63a3
- ff8c97cd55523cbdceef80407269d35bbf78abcbf807426c12d9debe1ce498d9
- 2beaa23907c40cfcb705844f4f515ff81a788abe1aed2c8d23626d9d735968ae
- b22fa98c3ee99222c4e827a9745f206ccf7cd40530459a92f183e148b0df5ce9
Source: csoonline, via checkpoint