Hackers exploit CVE-2023-38831 zero-day vulnerability in WinRAR
In the digital age, few tools have garnered the universal familiarity of WinRAR. With over 500 million users across the globe, this unassuming compression tool is as ubiquitous as it gets. It’s almost a rite of passage—download a file, and there’s a good chance it’ll be opened with WinRAR. But as the old adage goes, “With great power comes great responsibility.” The popularity of WinRAR makes it a tantalizing target for cyber adversaries.
Enter the sinister world of DarkMe malware. On a seemingly ordinary day, July 10, 2023, Group-IB Threat Intelligence was deep in its investigative trenches, tracking the spread of this malware. To their alarm, they unearthed a hitherto unknown vulnerability, tracked as CVE-2023-38831, in WinRAR’s processing of ZIP files. This wasn’t a mere chink in the armor; it was a gaping hole that had already been exploited since April of that year.
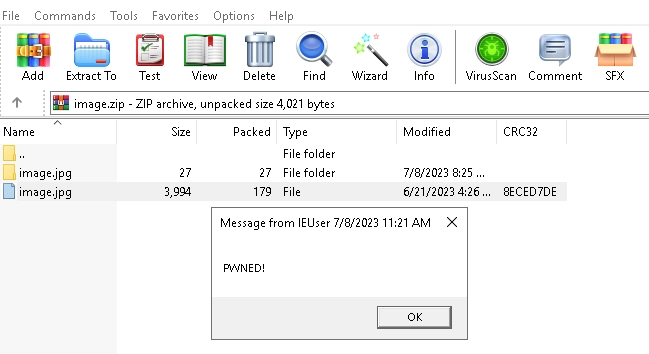
What made this discovery particularly chilling was the implications of the vulnerability. Crafty cybercriminals had been circulating weaponized ZIP archives on trading forums, masquerading as benign files. These were no ordinary files; they were Trojan horses. When unwary users extracted and executed these files, they unwittingly activated malware that paved the way for threat actors to make unauthorized withdrawals from broker accounts.

Image: Group-IB
Diving deeper into the mechanics of this cyber sleight of hand, it’s apparent that the attackers exploited a vulnerability allowing them to ‘spoof’ file extensions. In layman’s terms, they could hide nefarious code under the guise of familiar file types like ‘.jpg’ or ‘.txt’. To the unsuspecting user, the ZIP archive seemed innocuous—a standard image file paired with a similarly named folder. But lurking beneath this facade was a script, poised and ready to strike. A single click on this decoy file would trigger the subsequent stages of the attack, manipulating WinRAR’s functions, and bypassing the expected image, leading to the execution of a concealed batch file.
The burning question: Who’s the puppet master behind these strings? While the exact identities remain veiled in secrecy, Group-IB did note the use of the DarkMe trojan—a malicious code previously associated with the “Evilnum” threat group. Infamous for their financial motivations, Evilnum (or “TA4563” for those in the know) has haunted the UK and Europe’s digital corridors since 2018, with a penchant for targeting financial establishments and online trading platforms. However, pinning them down as the sole culprits behind this WinRAR exploit remains elusive.
In a commendable act of cyber responsibility, Group-IB immediately looped in RARLAB, WinRAR’s parent company, upon discovering this vulnerability. Joining forces, they tackled the issue head-on, and by August 2, a fortified version of WinRAR (6.23) was released, patching the CVE-2023-38831 security oversight.
Users are strongly advised to update to this version to ensure they’re shielded from potential exploits that might leverage this vulnerability.
In the meantime, it is important to be aware of the risks associated with this vulnerability and to take steps to protect yourself from attack. Here are a few tips:
- Do not open unsolicited or suspicious emails, especially if they contain attachments.
- Be careful about what websites you visit and what links you click on.
- Keep your software up to date with the latest security patches.
- Use a firewall and antivirus software to protect your computer from malware.





