
Security researchers at Malwarebytes have uncovered a troubling new tactic by cybercriminals. They’re using malicious ads disguised as legitimate software downloads on Google Search to infect the computers of unsuspecting system administrators.
The Trap
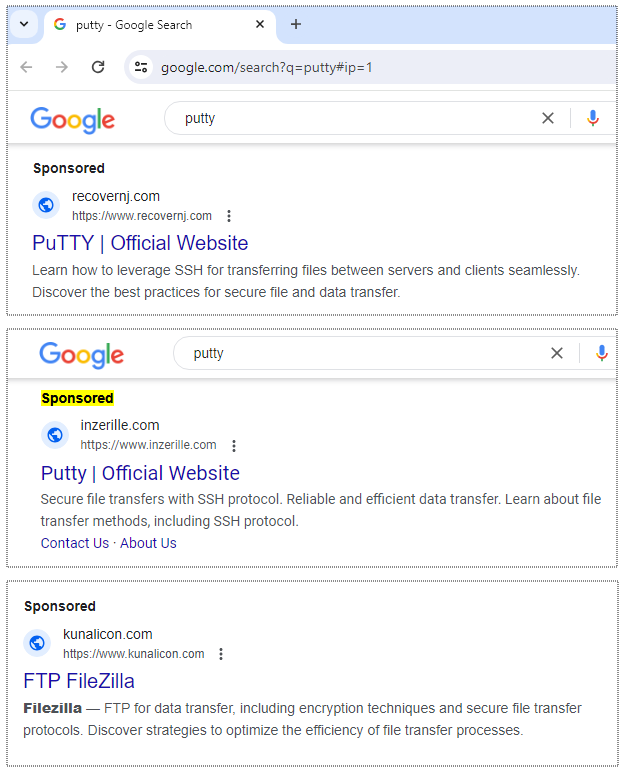
The campaign ingeniously begins with the display of fraudulent ads, masquerading as sponsored search results on Google. These ads, carefully crafted to capture the attention of IT administrators, promise legitimate downloads of PuTTY and FileZilla.
How It Works

- The Fake Download: Clicking on a malicious ad redirects the victim to a convincing copycat website designed to mimic the official software page.
- The Trojan Horse: The downloadable “installer” file secretly contains the Nitrogen malware, ready to infect the user’s system.
- The Real Danger: Once executed, Nitrogen gives hackers a foothold within the victim’s network, where they can steal data and deploy devastating ransomware like BlackCat/ALPHV.
The final act of this deceptive play involves the download and execution of a fraudulent installer. Nitrogen leverages DLL sideloading, a technique wherein a legitimate executable is abused to launch a malicious DLL. This campaign sees the benign setup.exe from the Python Software Foundation repurposed to sideload python311.dll, unveiling Nitrogen’s malevolent payload. This meticulous approach not only facilitates initial network access for the attackers but also sets the stage for subsequent data theft and ransomware deployment, with BlackCat/ALPHV lying in wait.
What’s Being Done (and What’s Not)
Malwarebytes researchers have alerted Google about this campaign, but so far, the malicious ads remain active. This highlights the risks inherent in targeted advertising and the need for heightened vigilance from users.
Recommendations
- Educate Your Staff: Raise awareness of malvertising threats. Emphasize that software downloads should only be done from trusted sources.
- Block Malicious Networks: Protect endpoints by using group policies to restrict web traffic from known advertising networks.
- Stay Alert: Monitor for unusual system behavior that could indicate compromise following any unexpected downloads or odd searches.