
According to Datadog Security Labs, a cybercriminal group known as MUT-1244 has launched a sophisticated attack campaign that successfully compromised not only regular users but also other hackers and security professionals. This year-long operation resulted in the theft of a staggering 390,000 WordPress credentials, along with sensitive data like private SSH keys and AWS access credentials.
MUT-1244 specifically set its sights on security researchers, penetration testers, red teamers, and even other cybercriminals. These individuals, who typically use compromised tools to test login credentials, unwittingly became the victims themselves. The attackers cleverly disguised exploits as proof-of-concept demonstrations in fake GitHub repositories, exploiting known vulnerabilities. They even went so far as to send phishing emails with fake “kernel updates” that promised enhanced processor performance but actually delivered malware.
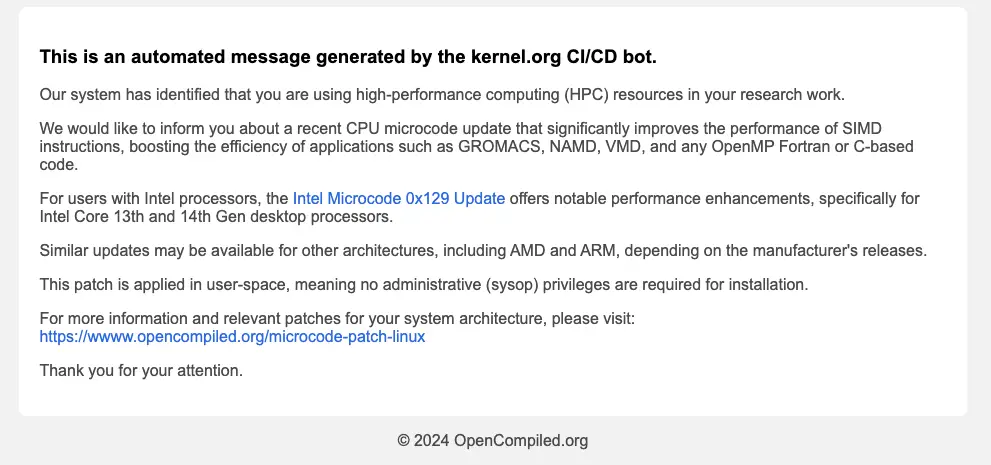
Adding to the deception, these malicious repositories were incredibly convincing. Their names were automatically included in feeds from reputable sources like Feedly Threat Intelligence and Vulnmon, lending them an air of legitimacy. This tactic successfully tricked numerous cybersecurity professionals and hackers into downloading infected files, believing they were acquiring useful code for their work.
MUT-1244 employed a variety of methods to distribute their malicious files through GitHub, including:
- Infected configuration files for software compilation
- Malicious PDFs
- Python-based droppers
- Compromised npm packages embedded as project dependencies
Once deployed, the malware acted as both a cryptocurrency miner and a backdoor, allowing MUT-1244 to steal sensitive data like private SSH keys, AWS credentials, environment variables, and the contents of critical directories.
Stolen data was then transferred to Dropbox and file.io using a second-stage payload hosted on an external platform. Disturbingly, the payload contained hardcoded credentials for these platforms, giving the attackers easy access to the exfiltrated information.
