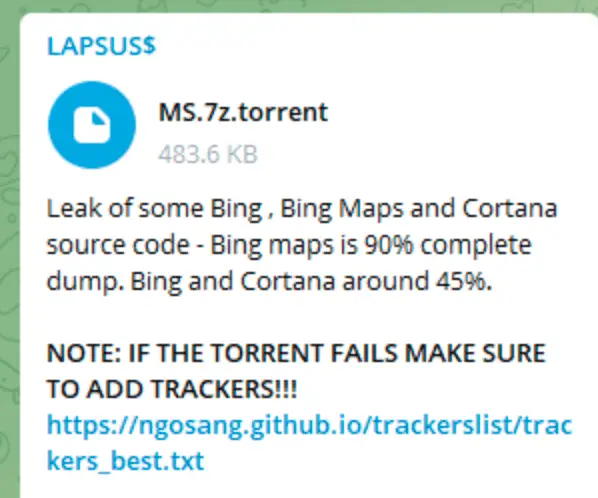
The South American hacker group LAPSUS is continuing to do things. The latest victim is Microsoft. At present, hackers have leaked some of Microsoft’s product source code. Previously, the hacker group launched attacks on well-known technology giants such as Nvidia, Samsung, and Vodafone, and some of them have been released online after stealing a large amount of confidential data. The attack against Microsoft mainly steals the development environment of Microsoft engineers, involving product lines including Bing source code, and Microsoft Cortana. After preliminary verification that these data are true, Microsoft has also released news that an investigation is underway, but Microsoft has not yet confirmed the authenticity of the news.
The Microsoft data leaked by the hacker mainly involves product lines of Microsoft Bing Search, Bing Maps, and Microsoft Cortana, which continues to operate only in the US market. Among them, about 90% of the dump logs of the Bing map product line were leaked, and about 45% of the dump logs of the Bing search and Microsoft Cortana product lines were leaked.

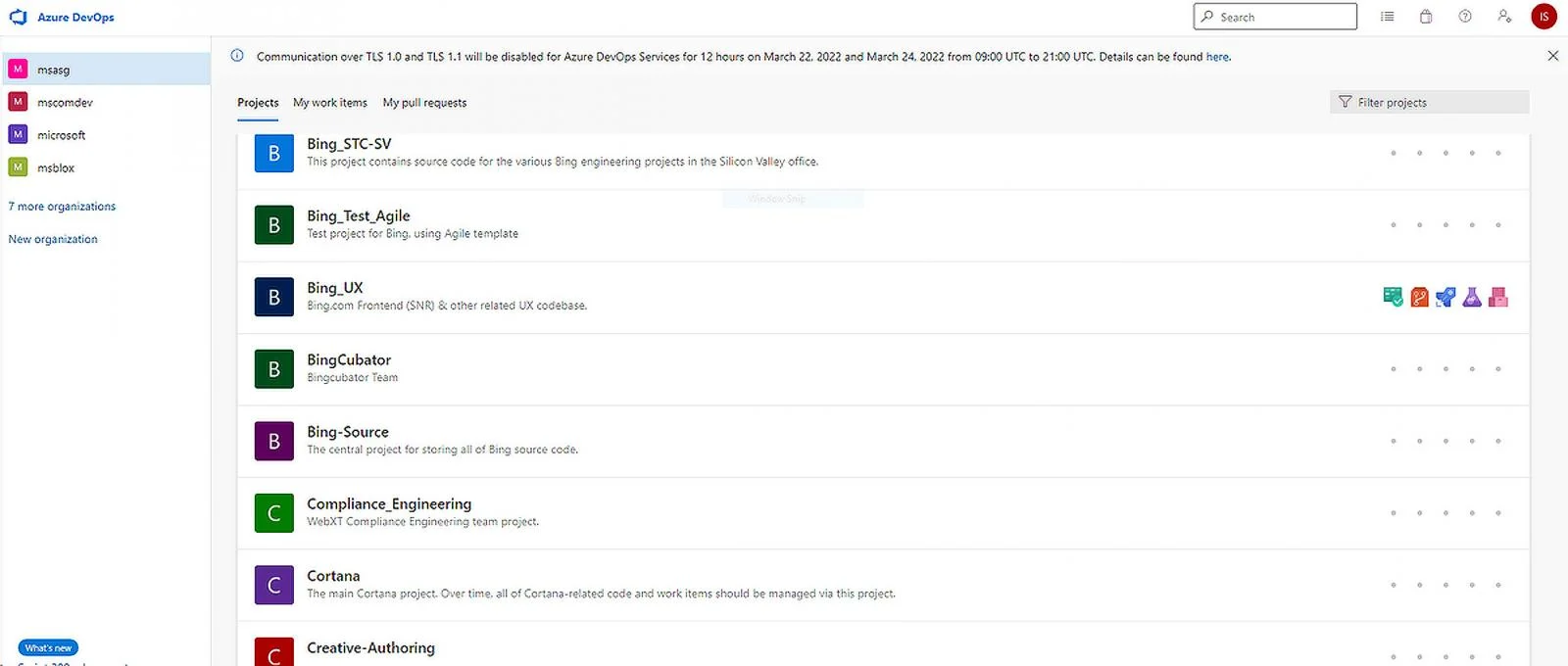
From the screenshots released by the hacker, it can be seen that the daily code submission and communication of Microsoft engineers should be included in the leaked data, even the design team. Microsoft simply responded to the matter, saying that we already know the relevant news and are investigating, and Microsoft will then estimate that the data does not affect security.
LAPSUS behaves a little differently in the era of ransomware, as the group only steals data without deploying any ransomware. Typically, today’s hacker groups deploy ransomware to encrypt victims’ data while stealing confidential data to increase bargaining power with victims. The current practice of this South American hacker group is to steal data, release some of the data, demand a ransom, and release the data if the victim does not pay the ransom. This attack on Microsoft and leaked data should have used up the value of the relevant servers and accounts because the screenshots released contain login information.
Via: bleepingcomputer