According to an article posted by the technology blog Barkly last week, security researcher Derek Knight (@dvk01uk) has discovered a series of new spam email campaigns using a more novel approach to infect victims. Instead of using Word documents or other types of attachments that are often abused, these activities use Web query files (.iqy)—essentially simple text files that are opened by default in Microsoft Excel for download data from the Internet.
Excel expert Jon Wittwer’s comment on the .iqy file was “basically like having a web browser built into Excel.” The danger is that it can be misused to package powerful utilities into an extremely simple and legal file format, which is not enough to cause anti-virus software to respond. As Derek Knight points out, “These blow past all antiviruses because they have no malicious content.“
In this series of spam e-mail activities discovered by Derek Knight, the .iqy file downloads a PowerShell script that is launched via Microsoft Excel and performs a series of malicious downloads.
The first batch of spam emails using .iqy files was issued on May 25, 2018, from Necurs, the world’s largest spam botnet. Subsequently, a smaller peak was detected on June 5, 2018. Only two days later, on June 7, 2018, Derek Knight found the third wave of activity.
E-mails that appear in all these activities have little and no text. This is a typical type of spam email. For example, in the first wave event, the subject of the mail is “Unpaid invoice [ID: xxxxxxxxx]”, the text is completely free of any content, and it looks like it is from insiders of the target organization.
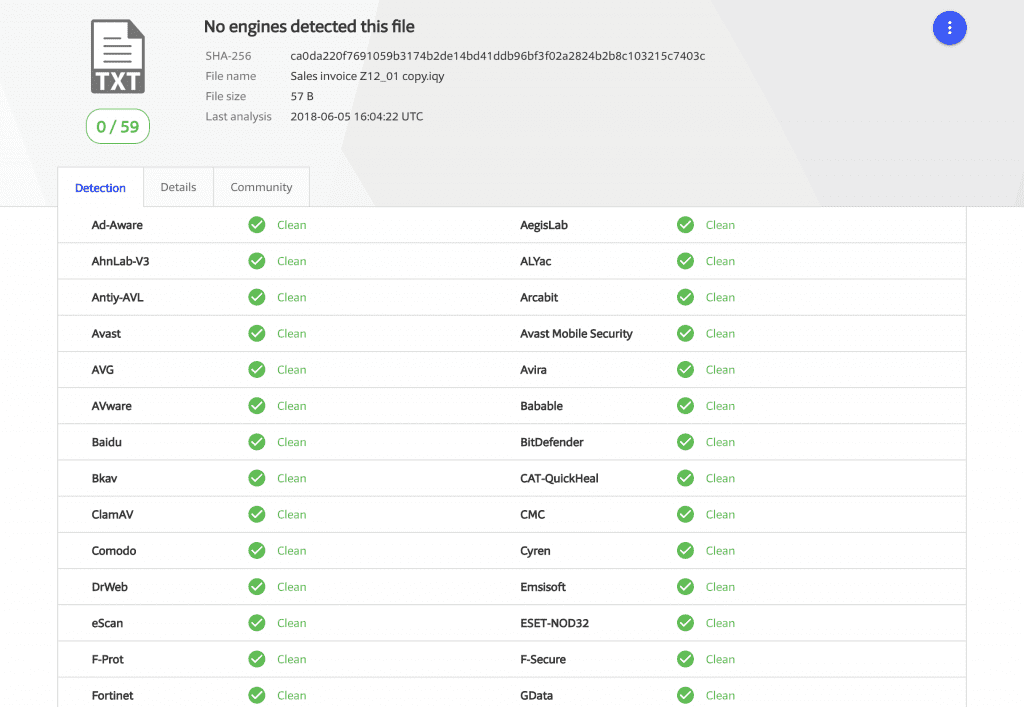
As mentioned earlier, almost all virus-killing software seems to be meaningless in the face of .iqy files. According to VirusTotal, the .iqy file that appeared in the first wave of events was completely undetected on the day. Until Derek Knight announced his findings through Twitter, antivirus software began to be detected in the next day.

When it is opened, the .iqy file is started with Microsoft Excel and attempts to extract data from the internally contained URL. As Jon Wittwer pointed out, the basic form of .iqy files is very simple. For example, opening a .iqy file that appears in a second wave event in Notepad looks like this (just a few lines of text):
A .xls file will be downloaded, which is actually a disguised .exe file. The final payload is Flawed Ammyy, a remote-access Trojan (RAT) discovered by cybersecurity firm Proofpoint.
FlawedAmmyy is built from the source code leaked by the popular remote desktop software Ammyy Admin. It has many features that provide Ammyy Admin. In simple terms, it basically allows the attacker to gain full access to the infected computer, allowing them to steal files and credentials, hijack the computer to send more spam emails, and so on.
We recommend that administrators should adjust firewall and email filtering rules in time to block .iqy files. In addition, unless you need to use .iqy files frequently, it is wise to further set up Windows to always open .iqy files in Notepad.
Source, Image: Barkley