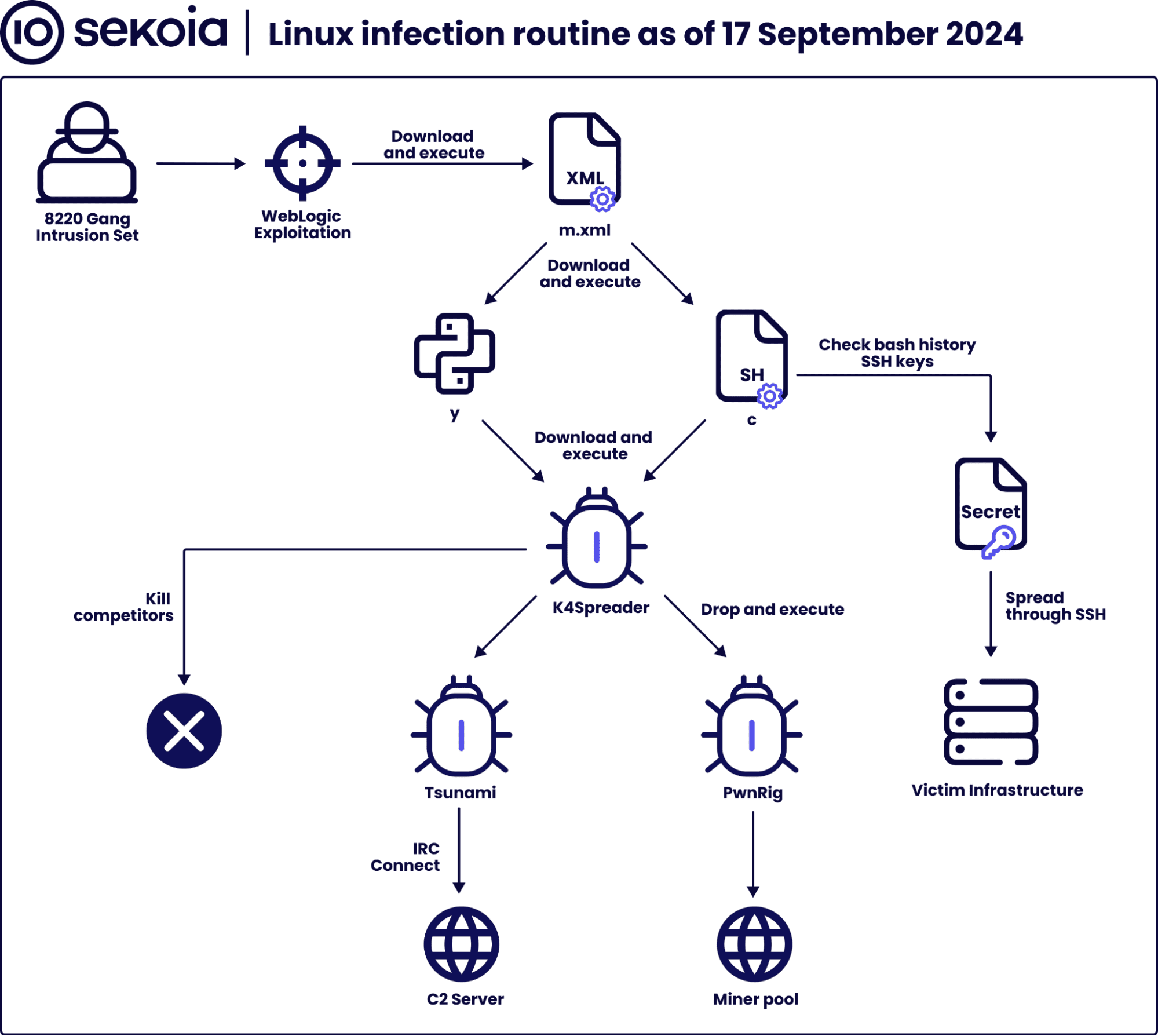
Linux infection routine | Image: Sekoia’s Threat Detection & Research (TDR) team
The notorious 8220 Gang, a China-based intrusion set first identified in 2018, continues to expand its arsenal with two new malware variants, Hadooken and K4Spreader, both of which were recently identified in a new report from Sekoia’s Threat Detection & Research (TDR) team. These sophisticated malware strains target vulnerable cloud environments, primarily to hijack system resources for cryptomining.
The 8220 Gang is taking advantage of well-known vulnerabilities, such as CVE-2017-10271 and CVE-2020-14883, in Oracle WebLogic servers to infect both Windows and Linux systems. Sekoia’s honeypot revealed an attack chain that involved the use of these vulnerabilities to deploy scripts, including K4Spreader and the Tsunami backdoor, while also delivering cryptominers to affected systems. This intrusion mirrors a similar attack chain identified by AquaSec, in which the Hadooken malware was deployed on WebLogic servers using comparable tactics.
K4Spreader, a Go-based malware, and Hadooken share similarities in their infection routines and payloads. Once deployed, both variants attempt to disable cloud protection tools, terminate competing cryptominers, and spread laterally within networks using SSH brute force techniques. The ultimate goal is to establish persistence and deploy cryptominers that siphon resources from compromised cloud servers to mine Monero cryptocurrency.
Tsunami, a Linux-based malware used primarily for Distributed Denial of Service (DDoS) attacks, is also a key component of both infection chains. The malware enables remote control of infected machines, allowing them to be used in botnet operations. The attackers leverage Internet Relay Chat (IRC) as a command-and-control (C2) protocol, linking several compromised servers to coordinate their activities.
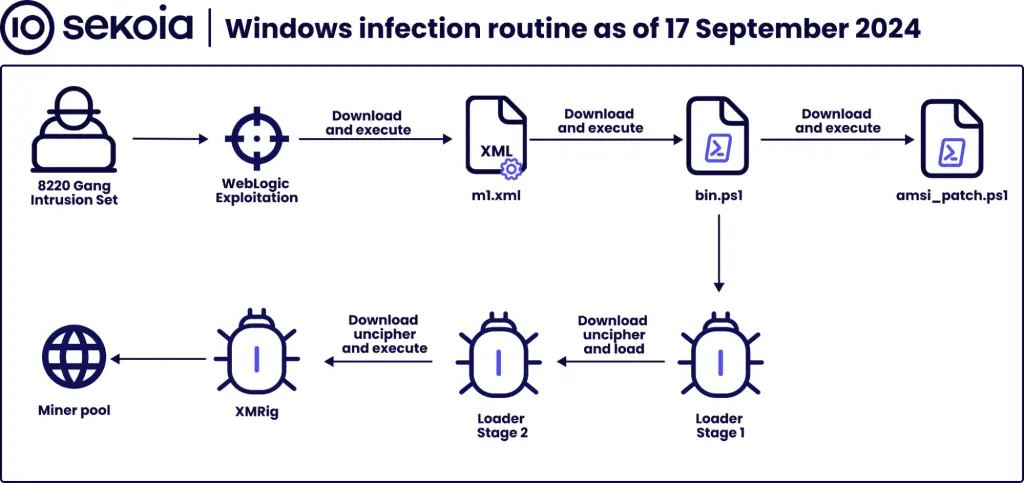
The 8220 Gang has demonstrated an opportunistic approach by targeting both Windows and Linux systems without prior reconnaissance. The infection routine begins by exploiting WebLogic vulnerabilities to execute scripts that download loaders responsible for installing cryptomining malware.
On Windows systems, the infection chain includes the use of PowerShell scripts to bypass antivirus protections, while on Linux, the attackers deploy shell and Python scripts to disable cloud security tools and propagate malware across networks.
The K4Spreader malware ensures persistence on compromised machines by leveraging cron jobs and systemd services, ensuring it remains active even after system reboots. Infected systems are forced to mine Monero through a private mining pool, with IP addresses linked to the run.on-demand[.]pw domain.
Both K4Spreader and Hadooken use the sck-dns[.]cc domain to maintain persistence by downloading the malicious “c” script. This shared infrastructure and the overlapping tactics, techniques, and procedures (TTPs) strongly suggest that the same threat actors are behind both malware strains.
The 8220 Gang’s primary focus remains on cloud hosting services, particularly targeting vulnerable systems in Asia and South America. A significant number of compromised IPs belong to Oracle Cloud, reflecting the group’s continued exploitation of cloud environments for cryptomining operations. Interestingly, the presence of Portuguese function names in the K4Spreader code suggests the possible involvement of a Brazilian operator, further highlighting the global reach of the 8220 Gang.
For more detailed information and indicators of compromise (IoCs), visit the official Sekoia GitHub repository.
Related Posts:
- France Leads International Effort to Eradicate PlugX Trojan from 3,000 Systems
- Hadooken Malware: A New Threat to WebLogic Servers
- Beyond Crypto: 8220 Gang Expands Arsenal with k4spreader
- Quad7 Operators Unveil New Moves with Advanced HTTP Reverse Shells and Botnet Expansion
- Defend Your Cloud: 8220 Gang Targets Linux & Windows