Halogen
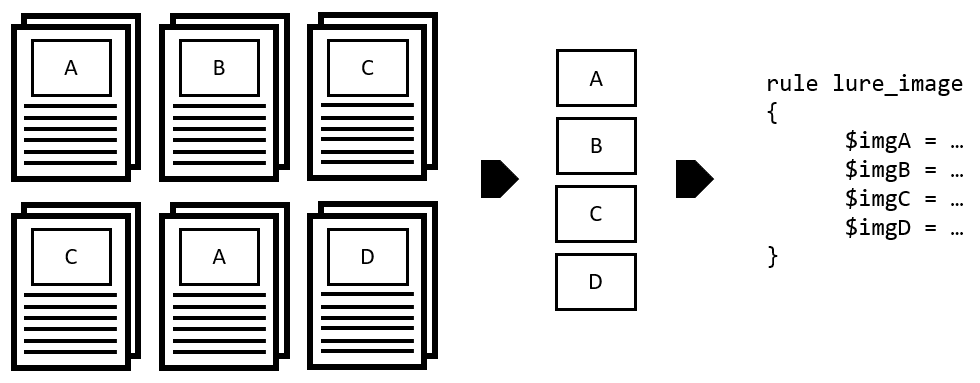
Halogen is a tool to automate the creation of yara rules against image files embedded within a malicious document.
Download
git clone https://github.com/target/halogen.git
Use
Testing it out
We’ve included some test document files with embedded images for you to test this out with. Running python3 halogen/halogen.py -d tests/ > /tmp/halogen_test.yara will produce the test yara file containing all images found within the files inside the tests/ directory.
From here you can run yara -s /tmp/halogen_test.yara tests/ and observe which images match which files.
Notes
- We use two patterns for JPG matching. One is less strict to the typical JPG file header, and we use this because we’ve seen some malicious files use this format. If Halogen finds both, it’ll default to writing out the more strict match. Typically, these have the same matching content, so no detection really gets missed.
- For PNG files you can choose to start by default at the file header, or with –png-idat you can start at the IDAT chunk found within a PNG file. We also reduced the bytes returned when matching on the IDAT chunk.
- Similar to the above, you can start JPG matches at the Start of Scan marker by using the –jpg-sos flag.
Copyright (c) 2020 Target Brands, Inc.
Source: https://github.com/target/