hate_crack v1.09 released: automating cracking methodologies through Hashcat
hate_crack
A tool for automating cracking methodologies through Hashcat from the TrustedSec team.
Installation
Get the latest hashcat binaries
mkdir -p hashcat/deps
git clone https://github.com/KhronosGroup/OpenCL-Headers.git hashcat/deps/OpenCL
cd hashcat/
make
make install
Changelog v1.09
- Revamped the hate_crack output to increase processing speed exponentially combine_ntlm_output function for combining Introducing New Attack mode “Bandrel Methodology” Updated pipal function to output top x number of basewords
Download hate_crack
git clone https://github.com/trustedsec/hate_crack.git
- Customize binary and wordlist paths in “config.json”
- Make sure that at least “rockyou.txt” is within your “wordlists” path
Create Optimized Wordlists
wordlist_optimizer.py – parses all wordlists from <input file list>, sorts them by length and de-duplicates into <output directory>
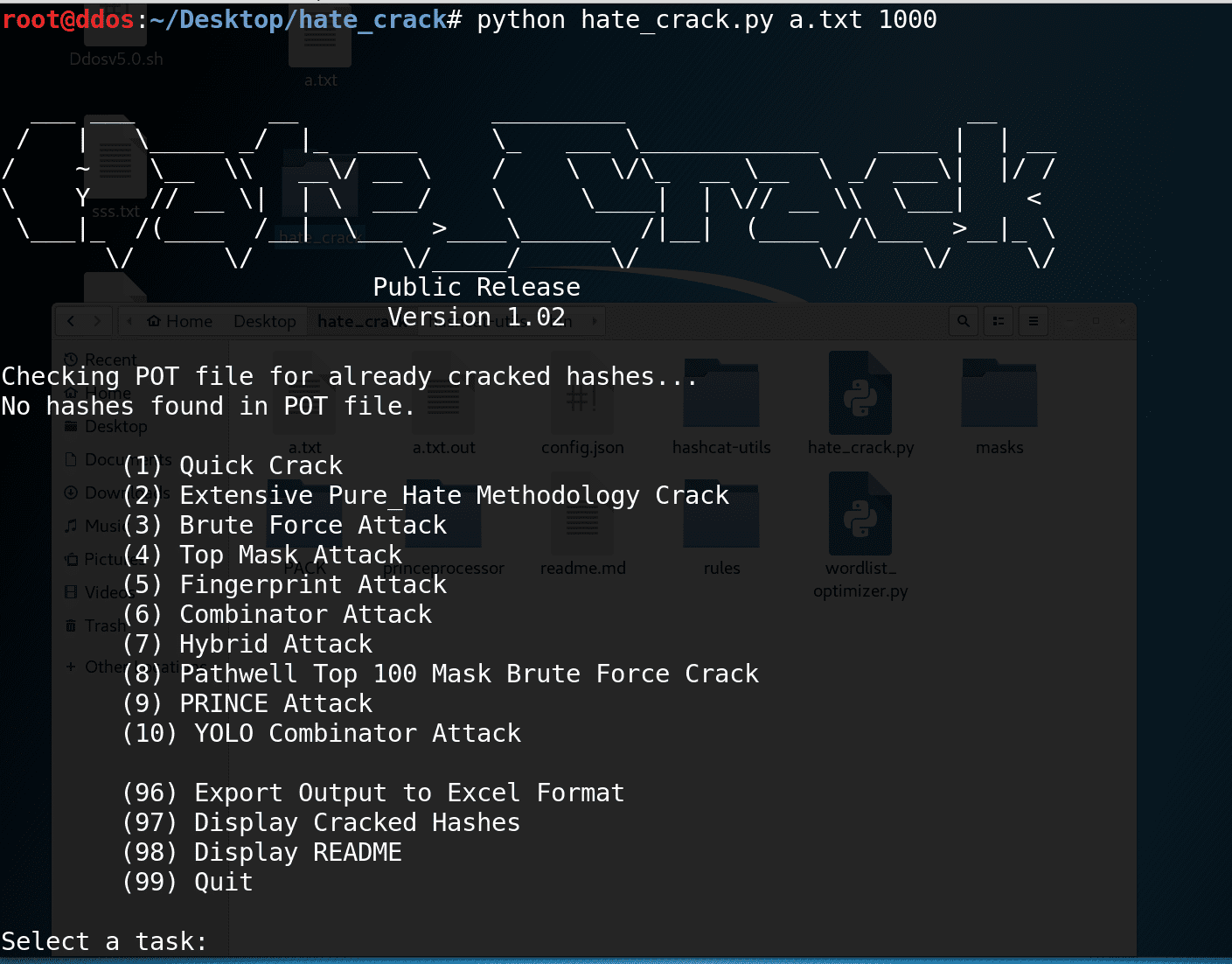
Usage
python hate_crack.py <hash_file> <hash_type>
Quick Crack
- Runs a dictionary attack using all wordlists configured in your “hcatOptimizedWordlists” path and applies the “best64.rule”, with the option of chaining the “best64.rule”.
Extensive Pure_Hate Methodology Crack
Runs several attack methods provided by Martin Bos (formerly known as pure_hate)
- Brute Force Attack (7 characters)
- Dictionary Attack
- All wordlists in “hcatOptimizedWordlists” with “best64.rule”
- wordlists/rockyou.txt with “d3ad0ne.rule”
- wordlists/rockyou.txt with “T0XlC.rule”
- Top Mask Attack (Target Time = 4 Hours)
- Fingerprint Attack
- Combinator Attack
- Hybrid Attack
- Extra – Just For Good Measure
- Runs a dictionary attack using wordlists/rockyou.txt with chained “combinator.rule” and “InsidePro-PasswordsPro.rule” rules
Brute Force Attack
Brute forces all characters with the choice of a minimum and maximum password length.
Top Mask Attack
Uses StatsGen and MaskGen from PACK (https://thesprawl.org/projects/pack/) to perform a top mask attack using passwords already cracked for the current session. Presents the user a choice of target cracking time to spend (default 4 hours).
Fingerprint Attack
https://hashcat.net/wiki/doku.php?id=fingerprint_attack
Runs a fingerprint attack using passwords already cracked for the current session.
Combinator Attack
https://hashcat.net/wiki/doku.php?id=combinator_attack
Runs a combinator attack using the “rockyou.txt” wordlist.
Hybrid Attack
https://hashcat.net/wiki/doku.php?id=hybrid_attack
- Runs several hybrid attacks using the “rockyou.txt” wordlists.
- Hybrid Wordlist + Mask – ?s?d wordlists/rockyou.txt ?1?1
- Hybrid Wordlist + Mask – ?s?d wordlists/rockyou.txt ?1?1?1
- Hybrid Wordlist + Mask – ?s?d wordlists/rockyou.txt ?1?1?1?1
- Hybrid Mask + Wordlist – ?s?d ?1?1 wordlists/rockyou.txt
- Hybrid Mask + Wordlist – ?s?d ?1?1?1 wordlists/rockyou.txt
- Hybrid Mask + Wordlist – ?s?d ?1?1?1?1 wordlists/rockyou.txt
Pathwell Top 100 Mask Brute Force Crack
Runs a brute force attack using the top 100 masks from KoreLogic:https://blog.korelogic.com/blog/2014/04/04/pathwell_topologies
PRINCE Attack
https://hashcat.net/events/p14-trondheim/prince-attack.pdf
Runs a PRINCE attack using wordlists/rockyou.txt
YOLO Combinator Attack
Runs a continuous combinator attack using random wordlists from the optimized wordlists for the left and right sides.
Source: https://github.com/trustedsec/