HatVenom: native powerful payload generation and shellcode injection tool
HatVenom
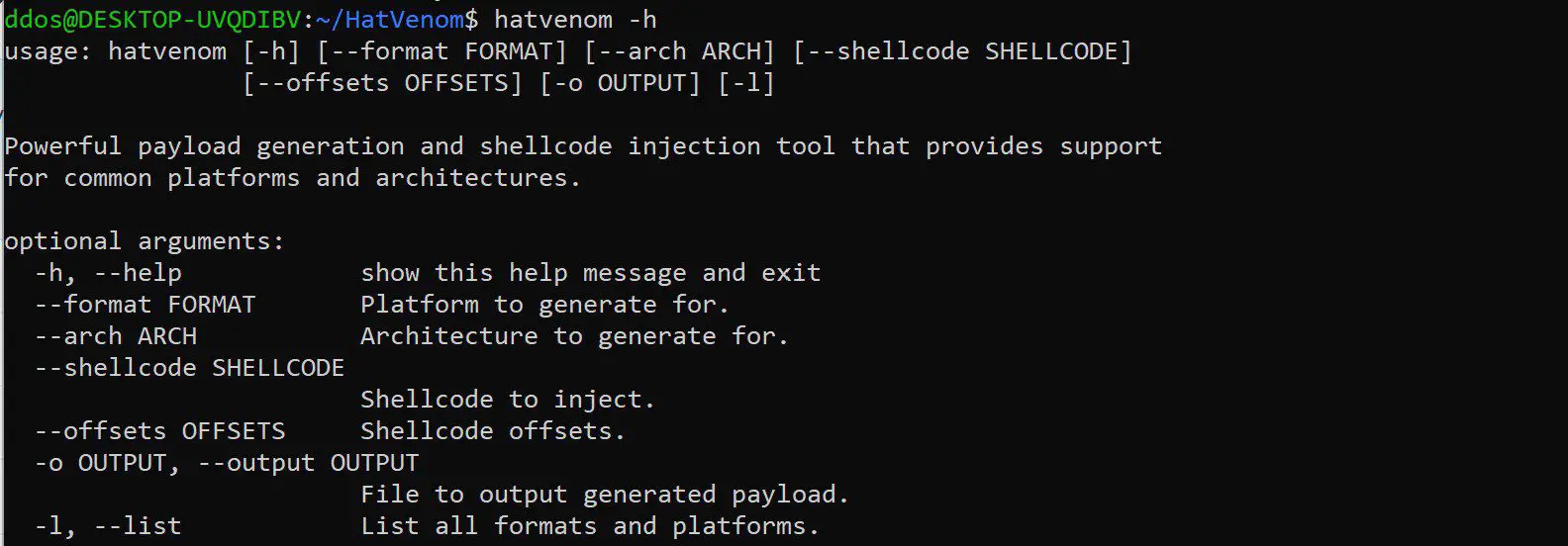
HatSploit native powerful payload generation and shellcode injection tool that provides support for common platforms and architectures.
Features
- Support for most common executable formats like elf, macho, pe.
- Support for most common architectures like x64, x86, aarch64, armle, mipsle, mipsbe.
- Ability to modify shellcode by changing pre-defined offsets.
Basic functions
There are all HatVenom basic functions that can be used to generate a payload, covert data, or inject shellcode.
- ip_bytes(ip) – Converts IP address to bytes allowed by the shellcode.
- port_bytes(port) – Converts numeric port to bytes allowed by the shellcode.
- string_bytes(string) – Converts a string to bytes allowed by the shellcode.
- generate(file_format, arch, shellcode, offsets={}) – Generates payload for specified target and with specified shellcode.
- generate_to(file_format, arch, shellcode, offsets={}, filename=’a.out’) – Generates payload for specified target and with specified shellcode and saves it to the specified file.
Install
pip3 install git+https://github.com/EntySec/HatVenom
Use
Generating payload
It’s very easy to generate a payload for various targets in HatVenom. Let’s generate a simple payload that calls shutdown for Linux and save it to a.out.
Payload offsets
Payload offsets is a variables used to add something to shellcode on the preprocessing stage. Offsets looks like this:
\x90\x90\x90\x90:message:string:\x90\x90\x90\x90
Where message is an offset name and string is an offset type. So the basic usage of the offset looks like:
[shellcode]:[name]:[type]:[shellcode]
There are some possible offsets types:
- string – Plain text that will be converted to bytes on the preprocessing stage.
- ip – IP address that will be converted to bytes on the preprocessing stage.
- port – Numeric port that will be converted to bytes on the preprocessing stage.
So if you want to replace offset with bytes instead of string, ip and port, you can use this type:
[shellcode]:[name]:[shellcode]
Examples
Let’s generate a simple payload that executes provided through file offset file for macOS and save it to a.out.
Copyright (c) 2020-2021 EntySec
Source: https://github.com/EntySec/





